| © 2022 Black Swan Telecom Journal | • | protecting and growing a robust communications business | • a service of | |
| Email a colleague |
August 2022
The Bitė Group Teams with Elitnet to Deliver Advanced Wangiri and ML-based Fraud Control
Telecom fraud protection is never permanent. Any success is merely a temporary safe haven like the eye of a typhoon where the winds are calmer and the skies are clear. But of course, as soon as the eye passes on, you’re hit with the full strength of the storm.
Protection is short-lived because fraudsters never stand still: they constantly seek to: discover an operator’s fraud triggers; improve their own automation; hide in data outliers; and step up the speed and variety of their attacks.
Thus, a solid fraud defense is a never a one-and-done deal. Periodic upgrades are required to add new layers of protection beyond the basic rules-based engines that almost every operator has as a minimum.
Large operators, of course, have a key advantage in fraud control: their economies of scale allow them to justify the high cost of FMS machine learning, cloud databases, and other advanced technology.
Small and mid-sized operators are not so lucky. They have a hard time getting first class fraud protection and customization at an affordable price. Suppliers who serve that market are rare. One of them, Equinox Information Systems, has delivered its Protector FMS to 2nd and 3rd tier U.S. telecom providers for 35 years.
So it’s a rare pleasure for Black Swan to feature this extended fraud management conversation with The Bitė Group — a mobile operator serving Lithuania and Latvia — and their solution provider, Elitnet, an up-and-coming FMS vendor who is delivering the kind of off-the-shelf system a small- to mid-tier operator is looking for.
Joining us is Jonas Milerius, Head of Fraud Management at the Bitė Group, and Vidmantas Šablinskas, Elitnet’s solution architect and product manager of their FMS, Onyx. Jonas explains the operator’s dilemma: significant fraud losses; failure of an in-house FMS build; the search for a flexible and affordable solution; the value of constant communication with the vendor; and negotiating for new customized features.
And Vidmantas gives us the vendor view: the growing complexity of fraud attacks such as Wangiri; the urgency of Machine Learning; the value of an advanced rules engine; and the importance of system flexibility/openness.
| Dan Baker, Editor, Black Swan Telecom Journal: Jonas, to begin, can you give us a quick backgrounder on yourself and your responsibilities at Bitė today? |
Jonas Milerius: Sure, Dan. I first worked at the Bitė Group 10 years ago. I began in the program management office, and worked there for a few years. Then I moved to Tele2 Lithuania where I was in product management and had profit responsibility for the postpaid. It was there where I also got involved with systems for roaming, pricing, and steering.

I suppose it was my experience on the business side that attracted Bitė to hire me back a couple years ago. Though my new responsibilities at Bitė are not as wide as they were before: I am highly focused on one critical area — fraud control.
Now to ramp up my knowledge I recently attended an excellent GSMA educational session in Croatia, where a wide range of fraud topics were discussed including network security and cybersecurity.
Since my main interest is in traffic-related fraud cases, I sought out people with that kind of experience. And I was fortunate to have a beer with a guy from Tele2 Sweden who’d been working there as a fraud specialist for an incredible 30 years. When I said to him, “30 years sounds like ancient history in the telco business”, he explained:
“Actually, in all my 30 years, the fraud control business has never been boring to me. Every year I constantly faced new challenges. So every day, you wake up to do your job the best you can.
But another thing motivated me, too: somebody living on another corner of the globe also wakes up every day to do their job — and that job is to commit fraud and steal as much money as they possibly can from me and my company.“
That comment set my mind straight on the mission critical nature of fraud control.
| What does the fraud threat look like in Lithuania and Latvia? |
Well, Lithuania and Latvia are in a very interesting position. Together, the population in our countries is less than 5 million people, and yet if you look at the GSMA reports, you notice Lithuania and Latvia combined are in the top 20 countries in terms of Wangiri fraud destinations.
So it’s a challenge to be an operator here. When our customers travel to Europe, USA, or other places, the operator who connects their call may have had a bad fraud experience, so they block every phone call to our countries. And when our customers return, they naturally call to complain.
Another even more important challenge we face, I believe, is that operators in our region are hit with more fraud attacks than normal.
| Do you work with the regulators or other operators in the region? |
In years past, we tried to coordinate with regulators and other operators to create a common detection system, but that effort was not successful.
Normally a regulator’s role is to control the operators and bring them in line with policy. But the guidance we actually get from them is of a softer variety: “this traffic might not look natural, so it might be fraud.” Another key issue is that the bad actor operators are not being prosecuted for their crimes, which probably is a topic relevant all around the world.
So while regional cooperation remains a long term goal, our sharp focus today is building our own fraud defense capability based on an off-the-shelf solution.
| Can you give us a quick history of fraud control at the Bitė Group? |
Ten years ago Bitė was using an off-the-shelf fraud management system from Sweden. Later we had an in-house solution for 5 or 6 years before recently switching to Onyx from Elitnet.
We first explored working with a large, well-known FMS vendor, but it’s hard to work with those firms because customizations take too long and they cost a fortune.
Our in-house developed fraud solution worked well at first, but it eventually lost its competence as fraud specialists left to take other jobs. And this was also the time we experienced some huge fraud cases where we lost hundreds of thousands of Euros.
At that time, a customer had a number of mobile data rate plans, SIM cards, and other things. That customer took 100 SIM cards and all of sudden those SIMs appeared in Peru, Afghanistan, and lots of other countries.
This was a well-prepared attack. They chose operators who do not have Camel. We were fortunate to stop the attack as soon as we did, but we still had a huge loss. It was such problems that prompted us to move to the Onyx system from Elitnet.
| Vidmantas, from your perspective as Bitė’s fraud solution provider, what are some of the build vs. buy issues they faced as they selected and adopted your Onyx FMS? |

Vidmantas Šablinskas: Dan, the basic challenge Bitė and other small operators face is taking their FMS to the next level. Bitė’s rule-based tool was excellent in detecting well-described frauds. However it was weak at detecting frauds with new or changing patterns.
Since fraud patterns have become increasingly dynamic, it often takes too much time to update a configuration in an existing system, and that significantly increases the fraud window. Then, in some types of frauds, a rule-based approach cannot be applied at all.
In short, investing in a more flexible off-the-shelf FMS is vital for a small operator. It is not effective to have an in-house process for developing a full-featured FMS. A product vendor is in a much better position to look across the market and continuously develop a system to address the latest fraud threats.
| Jonas, what was it about Elitnet that attracted you to invest in the Onyx FMS? |
Jonas Milerius: First of all, Elitnet has delivered for us in the past. With their real-time/SS7 application experience, they provided the Bitė Group with an NGIN platform, IN services, and a wide range of value-added services.
We also liked the idea that Onyx has been previously deployed in law enforcement agencies, so it was a fully functioning off-the-shelf FMS before it was implemented and customized for Bitė.
But most of all, I appreciate their flexibility and real openness. For example, Elitnet provides proactive support and is open for customizations. And we certainly have a much greater influence on Onyx’s roadmap compared to any larger, well-known FMS provider.
For example, we are now investigating a very big problem with SMS phishing. I’m talking about messages to your mobile phone where someone pretends to be your bank.
I called the Elitnet guys and said, “Hey, we don’t have anything to solve this issue today, but maybe we should.” And they said, “Let’s look into it.”
And this is not an easy project to commit to. The biggest challenge here is the EU’s GDPR regulation that protects customer data. The tricky part is we can’t examine the content of the message. So our plan is to use rules-based approaches then at the last stage we can apply some machine learning.
Other things I like include:
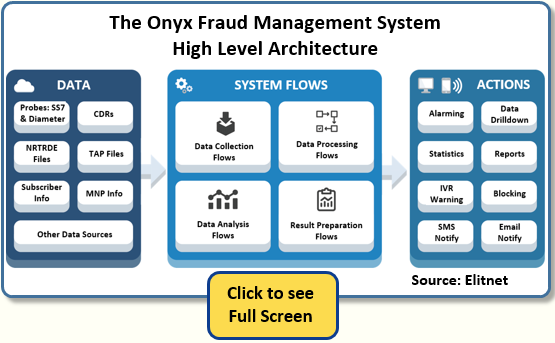
- Onyx as a system is completely open for customizations. You can
add totally new data collectors, new data processors, and even customizations
provided by third parties.
- The system includes a powerful rule engine and innovative ML that
synchronize in real time.
- We are getting excellent price performance and fast time to production.
Finally the results are impressive. Our fraud losses are very minimal now. Even within the first few days of using Onyx we saw a big difference, especially in the Wangiri area.
| Vidmantas, can give some details on the challenge of stopping Wangiri fraud? |
Vidmantas Šablinskas: Well, our Wangiri fraud control is something we are very proud of.
But it’s first important to recognize that the character of Wangiri fraud has changed. A few years ago, the pattern of attack was 2 or 3 attacking numbers at a time. In those days it was prudent to fight Wangiri with a rules-based system alone.
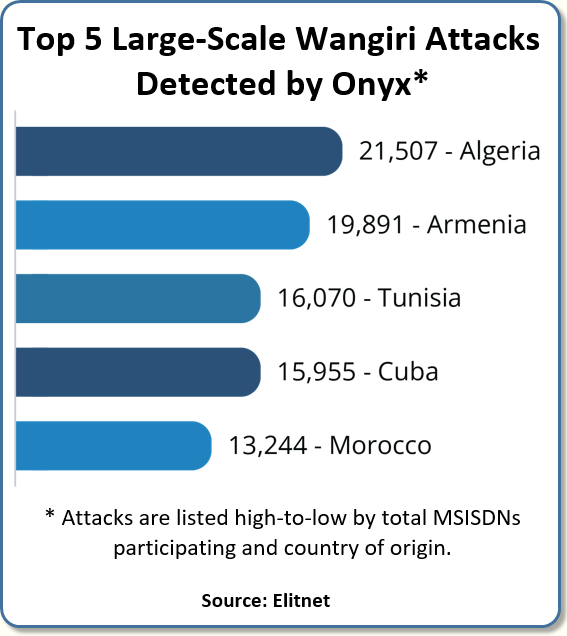
However, Wangiri attacks today are typically based on a very big number of MSIDSNs attacking. In one attack, we’re seeing 2,000 numbers, 4,000 numbers, or even more. So we are detecting these massive attacks using our state-of-the-art Wangiri detection ML model.
Remember, the traffic-pumping fraudsters doing Wangiri calls don’t focus on a particular operator. They simply select number ranges from the IPRN number providers and do traffic pumping to discover the number ranges that make the most money for them.
Yet as we started catching these Wangiri fraud attacks, the total amount of Wangiri attacks at Bitė dropped and the phone numbers participating in Wangiri attacks also fell.
| Jonas, what sort of blocking or treatment strategy do you use to stop the fraudulent call backs? |
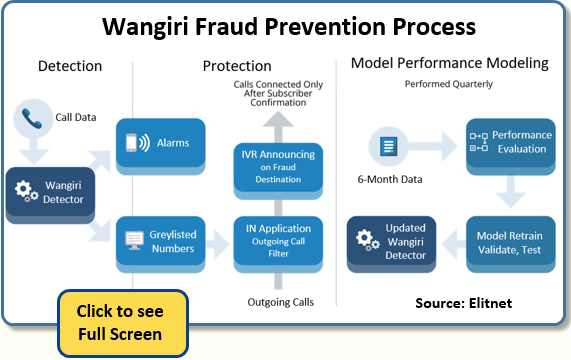
Jonas Milerius: It’s pretty straightforward, Dan. After the machine learning detector identifies that a Wangiri attack has started, our IN and provisioning systems are triggered to redirect calls to an IVR system across a wide range of numbers. And when the number is called back, the customer hears an IVR warning them the call may be fraud.
Now some of our Lithuania competitors block the calls automatically. But we don’t like that approach because the customer is given no explanation of why his call won’t go through.
Instead we use the IVR to communicate with our customer about the problem. In fact, the Bitė Group’s slogan is “It’s easier”. So we have that kind of customer focus in mind.
Another issue with automatic blocking is when the customer calls back and nothing happens, he’s apt to complain to the call center — which ends up wasting everybody’s time.
Our IVR message to customers is this: “Most likely the number you are calling is a fraudulent call. If you are sure who you are calling, we will continue to connect the call. Otherwise, we suggest you do NOT call this number.”
Now when a Wangiri attack begins, we don’t know how many numbers will participate in the Wangiri attack, so we put the IVR on an entire range of numbers.
But after the Wangiri attack is over, for 24 hours we might keep the IVR active. Afterwards, the IVR remains only on the numbers that were actually participating in the Wangiri attack: the rest of the big range of numbers go back to normal.
Yesterday we had a short Wangiri attack from Tunisia that went on for 30 minutes. So we redirected maybe 10,000 numbers to IVR. But after 30 minutes, only the numbers actually participating in the attack did we divert to IVR.
As you’d expect, we occasionally get complaints, especially from companies who are doing international business. But an unexpected warning for one customer calling to a compromised direction is justified if it prevents wide ranging fraud to many customers.
By the way, I firmly believe we are not only protecting our own network and customers, but indirectly protecting ALL Lithuania and Latvia customers. If the fraudsters are not getting Wangiri callbacks through, they are forced to attack operators in other regions of the world.
| Are you making progress in pro-active and preventative fraud areas? |
Yes, preventative measures are always on our agenda. Because of Elitnet’s proactive approach to support and development of Onyx, we constantly follow up and strategize with them about prevention of any new fraud cases.
So we are definitely getting more proactive. For instance, there’s the customer’s life cycle. If a customer is new, they are already under the “suspicious” flag, warning us that something may happen. So progress here is about dreaming up new rules and creating algorithms for machine learning.
In terms of rules, we key on things like an expected sequence or a certain ratio — and Onyx sees that all this is built into rules that identify certain patterns out of the norm.
Another proactive measure provided by Onyx is anomaly detection in subscriber behavior, trunks, and other areas. For example, a phone call might be within the norms of rules, but machine learning provides exception alerts where there are deviations from normal traffic. All machine learning models are retrained proactively and periodically and we’re always in touch with Elitnet about how they can be improved.
| How do the rules-based and ML sides of the solution work together? |
The rules and ML overlap each other: machine learning picks up things that the rules engine misses.
Fraudsters understand rules-based techniques. They try hard to insert their traffic in the gaps that our rules don’t catch. They are constantly testing to achieve the best fraud results.
Maybe the fraudsters can learn or estimate what our fraud alert triggers are, so maybe they wait 10 minutes before making the next Wangiri call. That’s why our ML system tracks the sequence or timing of a fraud attack.
With the rules based system we catch a lot. Today I suppose it’s like Pareto’s law — 80% is captured by the Rules and another 20% is ML. In the future, I think that split will shift dramatically towards ML detection.
| Jonas and Vidmantas, thanks for this fine briefing. I think your combined perspective on the special needs of small operators will be well-read by Black Swan readers. |
Jonas: Thanks, Dan. I don’t think the problems we face at Bitė are limited to Lithuania, Latvia, or even the EU. There are so many small- to mid-sized operators worldwide who need to be served better than they are today.
We feel lucky. And I hope our partnership with Elitnet grows. We greatly value their openness and flexibility to say, “Yes, let’s try something new that adds value.”
The beauty is I no longer feel I’m boxed in a system development corner. I’m now in a position where I can afford to experiment and recommend new tools and integrations that can really make a difference in protecting and growing our business.
Vidmantas: Jonas, thank you for your kind words. If I were to highlight the key things we’ve delivered to Bitė, it’s four things:
- State-of-the-art ML models that are very good at detecting many types of fraud;
- Synergy of rule-based approach and ML.
- Embedded analytics and good system manageability.
- Openness for integrations in the future, for example with third-party FMSs,
IPRN database, etc.
Copyright 2022 Black Swan Telecom Journal
Black Swan Solution Guides & Papers
- Expanding the Scope of Revenue Assurance Beyond Switch-to-Bill’s Vision — Araxxe — How Araxxe’s end-to-end revenue assurance complements switch-to-bill RA through telescope RA (external and partner data) and microscope RA (high-definition analysis of complex services like bundling and digital services).
- Lanck Telecom FMS: Voice Fraud Management as a Network Service on Demand — Lanck Telecom — A Guide to a new and unique on-demand network service enabling fraud-risky international voice traffic to be monitored (and either alerted or blocked) as that traffic is routed through a wholesaler on its way to its final destinations.
- SHAKEN / STIR Calling Number Verification & Fraud Alerting — iconectiv — SHAKEN/STIR is the telecom industry’s first step toward reviving trust in business telephony — and has recently launched in the U.S. market. This Solution Guide features commentary from technology leaders at iconetiv, a firm heavily involved in the development of SHAKEN.
- Getting Accurate, Up-to-the-Minute Phone Number Porting History & Carrier-of-Record Data to Verify Identity & Mitigate Account Takeovers — iconectiv — Learn about a recently approved risk intelligence service to receive authoritative and real-time notices of numbers being ported and changes to the carrier-of-record for specific telephone numbers.
- The Value of an Authoritative Database of Global Telephone Numbers — iconectiv — Learn about an authoritative database of allocated numbers and special number ranges in every country of the world. The expert explains how this database adds value to any FMS or fraud analyst team.
- The IPRN Database and its Use in IRSF & Wangiri Fraud Control — Yates Fraud Consulting — The IPRN Database is a powerful new tool for helping control IRSF and Wangiri frauds. The pioneer of the category explains the value and use of the IPRN Database in this 14-page Black Swan Solution Guide.
- A Real-Time Cloud Service to Protect the Enterprise PBX from IRSF Fraud — Oculeus — Learn how a new cloud-based solution developed by Oculeus, any enterprise can protect its PBX from IRSF fraud for as little as $5 a month.
- How Regulators can Lead the Fight Against International Bypass Fraud — LATRO Services — As a regulator in a country infected by SIM box fraud, what can you do to improve the situation? A white paper explains the steps you can and should you take — at the national government level — to better protect your country’s tax revenue, quality of communications, and national infrastructure.
- Telecom Identity Fraud 2020: A 36-Expert Analysis Report from TRI — TRI — TRI releases a new research report on telecom identity fraud and security. Black Swan readers can download a free Executive Summary of the Report.
- The 2021 State of Communications-Related Fraud, Identity Theft & Consumer Protection in the USA — iconectiv — This 49-page free Report on communications-related fraud analyzes the FTC’s annual Sentinel consumer fraud statistics and provides a sweeping view of trends and problem areas. It also gives a cross-industry view of the practices and systems that enable fraud control, identity verification, and security in our “zero trust” digital world.



