| © 2022 Black Swan Telecom Journal | • | protecting and growing a robust communications business | • a service of | |
| Email a colleague |
February 2021
Mobile Security Leverage: MNOs to Tool up with Distributed Security Services for Globally-Connected, Mission Critical IoT

“Give me a Lever and a place to stand on, and I will move the World.”
Archimedes (3rd Century BC)
The ancient Greek scientist and engineer, Archimedes, was a pioneer in leverage.
He understood that great mechanical advantage could be gained from simple levers, pulleys and screws. He designed a block-and-tackle pulley allowing sailors to move heavy objects. To defend his city of Syracuse from siege by the Romans, he even invented a crane to grapple enemy ships close to the city’s wall and lift them partly out of the water to shake them.
Leverage is just as crucial in the digital world as it was in the age of wooden wheels. And it’s especially challenging in security because the attackers exploit system weak points and operate in the outliers of behaviors where computers can’t easily detect them.
In telecom, the whole point of leverage is to make security protection affordable enough to keep the customer safe and the operator profitable. Without some form of leverage, fraud/security staffing and analytic systems simply can’t keep up with the criminals.
Yet clever techniques that boost leverage can have an enormous impact on protection:
- SIM bypass fraud was hard to block because fraudsters could discover the A numbers operators use for test calls that detect the bypass. Then SIGOS (now Mobileum) created a way to multiply the A numbers of test calls into
the millions, making it impossible for fraudsters to keep up.
- Hackers daily launch relentless automated identity attacks on the on-line
service ordering systems of telecoms. However NuData Systems’ solution
deeply and anonymously tracks on-line data-entry patterns to quickly determine
if an on-line persona is who they say they.
- For decades, IRSF and Wangiri traffic pumping attacks have cost telecoms
several billion dollars’ worth of losses each year. But Lanck Telecom
has developed a simple-to-deploy A-to-B Handshake IP exchange allowing the A
number operator of a voice call to know prior to the call that the B number
is legitimate.
Perhaps the biggest telecom security challenge yet is global IoT — applications such as connected cars and real-time/mission-critical industrial apps that cross national boundaries and operators.
The massive complexity of Global IoT naturally raises security concerns, yet telecoms have a huge stake in IoT's success which motivates them to innovate and collaboratively clear the security bottlenecks with their IoT and enterprise partners.
And that’s the subject of another discussion I had with security evangelist Jimmy Jones of Positive Technologies. Jimmy weighs in on the challenge of distributing security intelligence and gives his thoughts on how 5G/IoT security is evolving plus the threats and regulatory burdens being faced by MNOs in particular.
| Dan Baker, Editor, Black Swan Telecom Journal: Jimmy, the name of Positive Technologies came up in a recent conversation I had with iBASIS. They are rolling out to their MNOs a portfolio of services to enable them to gain a considerable security edge as they move to support mission critical and international IoT. |
Jimmy Jones: Dan, we view this as a great development. iBASIS is going to deliver that as a service that merges their secure IPX network (globally connecting 800+ MNOs) with the services of security partners — Positive Technologies and others.
Were an MNO to build this level of security themselves, it would require a huge capital investment and major staff training.
Consider how Positive Technologies goes to market. Our core business is security research and intelligence. And every service or solution we offer is merely a different way of delivering that security intelligence — either through an audit, a monitoring platform, a firewall — whatever it is.
But a company like iBASIS is better at the delivery side of security than we’ll ever be. And effectively distributing security intelligence is as vital as capturing it.
| All of this interest in enhanced security is to prepare for coming rollouts of 5G networks which will greatly enable IoT’s global expansion. What’s your take on 5G’s progress to date? |
Well, 5G deployment seems to be moving at a good pace, despite Covid-19. Of course, at the moment, it’s not full 5G. Today we have the so-called “non-standalone” 5G or NSA5G, basically a hybrid network where equipment on the edge of the network increases download speeds.
Now while getting better 5G coverage and speeds is one goal, another big one is to enable operators to virtualize their networks so niche innovative network products can come to life. These could be aimed at target industries for instance, without the cost and delay of having to build out dedicated physical networks.

You can build a network, but then you need to segment it for different needs — the slicing of the network you hear about. Previously there was a single slice for communications as it was just humans using the network, now each flavor of IoT requires a tailored slice to provide the environment and QoS it needs. Some will require low latency. Or a slice might require high bandwidth or low bandwidth.
Now, to get to full 5G standalone will take a very long time because large investments in money and resources need to made. In our view, then, 5G is more like an evolution than a revolution.
The gradual deployment of 5G elements will steadily co-exist and replace the 4G elements until 5G becomes dominant. Then 4G will merely fill the gap for the folks who haven’t upgraded their phones or devices to 5G.
The rollout will be hugely complex and time-consuming in itself because the operators are going to deploy a new network with new elements and services while having to support the previous generation’s maintenance needs.
And they need to make sure they are working seamlessly and securely. So even that evolutionary part will be super complex. Frankly, one of the dangers of living with these hybrid networks for a long time is it introduces a backward threat into your 5G infrastructure.
| OK, the virtual networks will enable telcos to move to a service-based architecture. |
Yes, up to now, network consisted of different network functions connected point to point with separate dedicated interfaces. With full 5G, the network underneath is configured in software to achieve the service-based scheme. Here’s a quick analogy to explain the difference:
Let’s say you live in a small American town with three major restaurants: a McDonalds cooking hamburgers, a Golden Lotus serving Chinese, and Mama Mia’s doing Italian dishes.
Now on the 4th of July, people are looking to eat hamburgers — not sweet-and-sour chicken or spaghetti dinners. So McDonald’s is doing some good business. Trouble is, McDonald’s doesn’t have enough cooks to meet the high demand for hamburgers.
Meanwhile, the chefs at the Golden Lotus are sitting idle and playing Mah Jong to kill time.
So these dedicated restaurants are similar to today’s network. Their design is too single-purpose and inflexible in terms of fitting resources to the market’s needs.

This is where an All-You-Can-Eat-Buffet style restaurant solves this problem by enabling a wide variety of menu items a customer can get at one location. So on the 4th of July, the cooks merely shift to serving more hamburgers.
And yet, there’s a problem with the All-You-Can-Eat restaurant, too. If everything is working together, then it increases the complexity in the kitchen. It’s easier for mistakes to happen — or in the case of networks, a security breach can cause wider damage and failures than in the old dedicated networks.
| In fact, it seems regulators around the world are deeply concerned that security could rapidly get out of hand with 5G, IoT, and the growing reliance of society on communications, especially mobile service. |
True. Global administrations really stepped up the pressure for greater 5G mobile security in a 2019 conference in Prague. It was attended by 32 countries representing all the EU countries, and NATO countries like the US.
And they came to an accord at that meeting. That led to the European Union producing the EU Toolkit, a very good document that lists all the different things operators need to do, such as achieve diverse networks and remove equipment vendors who are insecure. Auditing is in there, too. Essentially they aim to increase their regulatory powers to better secure the network supply chain and overall security.
Half a year later the CISA in America produced a very similar document. And soon after, Latin American countries like Brazil, Ecuador, and other got involved as well.

Finally, toward the end of 2020, the UK’s Ofcom passed the first actual legislation, basically putting the EU Toolkit into law. The regulator set up some pretty stiff fines: 100,000 pounds a day or up to 10% of an operator’s revenue for non-compliance.
Odds are this trend will continue. India, for example, is part of a well-established, three-way security agreement with the UK and US and has some legislation being debated, so I expect something soon from them.
More regulation is coming: there’s no way the operators can avoid it. And that means all operators — but particularly smaller ones — are going to have additional overhead to deal with.
This is why having security available as a service makes a lot of sense. You avoid the expense of putting more boxes in your network and the burden of training all your staff to become more security-aware.
By the way, though the legislation affects 5G, it encompasses legacy elements security, so it affects 4G, 3G, and 2G as well.
And there’s good reason behind these administrations security concerns. If one operator goes down in a country, government officials can wash their hands of the problem and blame the operator. But if multiple operators fail, then the public is going to blame the governors.
You can bet the regulators are worried about that. Also we need to keep in mind mobile networks will no longer be just our phones. Imagine if all the IoT controlled traffic lights in a major city broke down.
| How well is the industry preparing the groundwork to protect the signaling side of 5G? |
Well, 5G brings in new and different technologies to be secured. In telecom security we are used to hearing about SS7 and Diameter, protocols used in previous generations where networks are quite closed and the protocols niche.
However, with 5G we see the HTTP/2 and virtual environments, both of which are well known and highly accessible to hackers. Another challenge is these protocols will expand access to supporting APIs and open up a far greater number and variety of partner relationships.
When the engineers were at the university, these are the protocols they were learning about. They were not interested in learning much about SS7, something that rolled out in 1979 during the digital dark ages.
What we used to have in telecom is “security by obscurity” — those were the days when SS7 was known by only a small group of telecom engineers and a very few committed hackers. Those days are gone.
Now Positive did some testing of 5G labs — some internal and some external. We found interfaces out in the open and a surprising lack of verification. Our researchers could connect with many different infrastructures and gather sensitive info without being challenged.
In particular, we looked at the PFCP (Packet Forwarding Control Protocol) which is used to set up data connections. We discovered if you could access that, you could intercept data using man-in-the-middle attacks. You could also deny service to equipment. Both of those attacks are pretty serious.
Imagine if I was logging onto my bank website from my 5G phone, the man-in-the-middle attack could allow them to be between me and my bank.

We need to ensure those PFCP interfaces are really well-configured, as they should be locked away in the network away from external access.
Trouble is: PFCP’s security protection, then, is similar to what we see for Diameter and GTP which should also be isolated interfaces, but which we can penetrate. And yet now, you’re building a whole new network while still looking after a previous generation network, and combining them.
So the key question is: With all these new services, are you sure you’re not going to repeat the same configuration mistakes you made previously?
Besides the signaling protection issues, a second key vulnerability is the plan to put everything on a single bus enabling access to all network functions via APIs. The issue with this service based architecture bus is it won’t be just telephone companies connecting to it. You’ll potentially have IoT companies and other partners coming in and gathering data or maybe even sending an update over the network.
This is dangerous. If the wrong people gets near this bus, it could cause huge problems. So that needs to be locked away.
| Up to this point, we’ve discussed future threats. But how well are MNOs combatting security attacks TODAY against the signaling infrastructure? |
Dan, to assess the progress MNOs are making, a few years ago Positive Technologies decided to do an annual series of signaling defense reports. Each year we probe the networks and assess the security of 40 to 50 of our MNO clients. The high level annual findings create a sort of “health check” on MNO progress — or lack of progress — in defending their signaling systems.
The chart below rolls up our analysis from year 2015 to 2019:
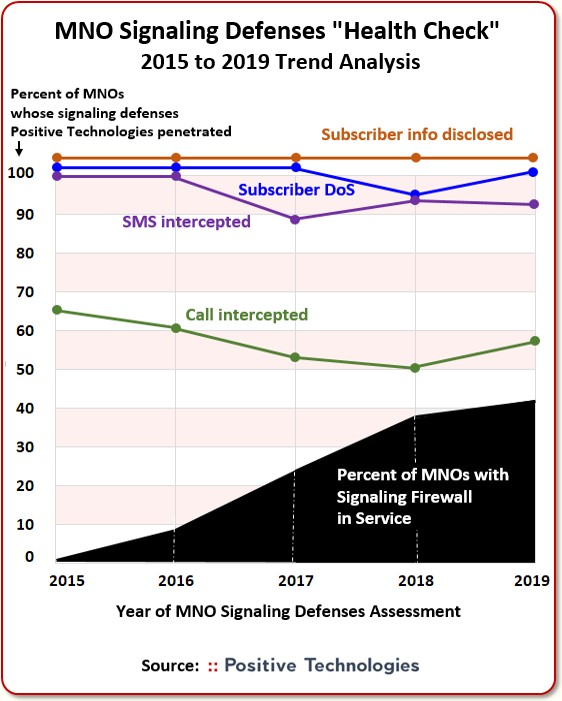
Note: at the bottom of the chart we plotted the percent of MNOs we surveyed who had a signaling firewall in service. Back in 2015, no MNO we surveyed had such a firewall, but by 2019, 41% of the MNOs we tested had invested in and deployed a signaling firewall.
At the top of chart we plotted how well Positive’s researchers could simulate a hacker attack and penetrate defenses. They tried four kinds of attacks: 1) capture valuable info on subscribers; 2) succeed in a Denial of Service (DoS) of a mobile phone; 3) intercept an SMS; and 4) intercept a voice call. And here are the key results:
- Subscriber info disclosure — In 100% of the networks we tested,
we were able to successfully capture some valuable subscriber info. In
some cases it was account information. In other cases we could track the location of the phone.
- A successful Subscriber DoS attack means the ability to take the subscriber
off the network. This can be done in a number of ways. For instance,
if I know the IMSI of your phone, I can make it look like the phone is located
in London instead of New York, which would allow all the messages to be routed to the hacker.
PP
Or they can make it look like the mobile phone is on the move. If it looks like it’s not in New York, then the subscriber is not getting his messages. When the hackers push you off the network; they can even delete your roaming registration, which means you lose service in some way.
Sometimes you need to restart your phone to renew your registration. Other times it renews itself as you move to a new cell tower. On average, a mobile phone DoS attack will cause a downtime of about 3 hours.
- In the first few years, the MNOs we tested succeeded in lowering voice call
and SMS intercepts. Unfortunately, in our 2018 and 2019 tests, those
numbers began creeping up, meaning our testers were getting through defenses
more often.
Now, since MNOs made big investments in signaling firewalls from 2015 to 2019, you’d naturally expect the success rate of attacks to come down. But that’s not what happened: the success rate of attacks actually stayed fairly level.
| So why didn’t the investment in signaling firewalls deliver a better security payoff? |
Well, it’s because hackers have adapted and broadened their attack capability over the years.

They know when a signaling firewall is in place that certain techniques they used before won’t work anymore. So what do they do? They begin fingerprinting the network — testing it again and again until they gather enough intelligence to guess which bypass techniques they can use.
Positive has identified about 4 or 5 major types of bypass. And each of those can be tweaked a bit to try and get through. Basically the hackers exploit the list of things that are not allowed to happen, as well as the things that ARE allowed to happen.
For example, certain kinds of messages will be blocked via access control lists. But if they can find in that list a message tweak that triggers the access list to implement a forward action rather than a message block, then the hacker can get inside before the firewall figures out it’s supposed to block you.
That’s how the bypass techniques work. And the techniques get complex very quickly. Based on the testing our white hat hackers do on behalf of our clients, we succeed in getting through defenses at nearly 70% of the operators we tested.
| Jimmy, thanks for another splendid briefing. You’ve given us a nice mix of industry predictions and granular detail to think about. |
My pleasure, Dan. I think the key message to take away is that siloed security expertise is not sufficient as 5G and IoT go global. Remember, 5G will cause networks to grow exponentially. Plus there’s going to be huge growth in devices on the network.
Bottom line: the security guys are going to have to work closer and closer with the guys moving packets to embed security into every object. For example, Oracle’s platform has some very good filtering. But Oracle is not an independent vendor exclusively focused on security. Their business is to move packets from A to B.
Yet if we can put our intelligence onto the Oracle equipment, that’s no different from putting it on the Positive Technologies or iBASIS filtering equipment.
We need to get security inside the element that needs it. That means security must become more agile and deliver its intelligence more centrally into the network.
So people like us are going to have to work closely with distributors of security intelligence. Otherwise the MNOs won’t be able to afford the security it takes to keep their networks safe.
Copyright 2021 Black Swan Telecom Journal
Recent Stories
- Epsilon’s Infiny NaaS Platform Brings Global Connection, Agility & Fast Provision for IoT, Clouds & Enterprises in Southeast Asia, China & Beyond — interview with Warren Aw , Epsilon
- PCCW Global: On Leveraging Global IoT Connectivity to Create Mission Critical Use Cases for Enterprises — interview with Craig Price , PCCW Global
- Subex Explains its IoT Security Research Methods: From Malware & Coding Analysis to Distribution & Bad Actor Tracking — interview with Kiran Zachariah , Subex
- Mobile Security Leverage: MNOs to Tool up with Distributed Security Services for Globally-Connected, Mission Critical IoT — interview with Jimmy Jones , Positive Technologies
- TEOCO Brings Bottom Line Savings & Efficiency to Inter-Carrier Billing and Accounting with Machine Learning & Contract Scanning — interview with Jacob Howell , TEOCO
- PRISM Report on IPRN Trends 2020: An Analysis of the Destinations Fraudsters Use in IRSF & Wangiri Attacks — interview with Colin Yates , Yates Consulting
- Telecom Identity Fraud 2020: A 36-Expert Analyst Report on Subscription Fraud, Identity, KYC and Security — by Dan Baker , TRI
- Tackling Telecoms Subscription Fraud in a Digital World — interview with Mel Prescott & Andy Procter , FICO
- How an Energized Antifraud System with SLAs & Revenue Share is Powering Business Growth at Wholesaler iBASIS — interview with Malick Aissi , iBASIS
- Mobileum Tackles Subscription Fraud and ID Spoofing with Machine Learning that is Explainable — interview with Carlos Martins , Mobileum


