| © 2022 Black Swan Telecom Journal | • | protecting and growing a robust communications business | • a service of | |
| Email a colleague |
February 2020
LexisNexis Risk Solutions Takes Identity Checks from Physical/Biometric to Network-Behavior-Sharing with 7,000 Digital Businesses

The beauty of the Internet is that it has enormously reduced friction. It has enabled the free-flow of information by bypassing countless brick-and-mortar middle-men and gatekeepers who slowed access to getting answers and buying things with speed and efficiency.
Unfortunately, new layers of friction and inefficiency have been added to the on-line and mobile experience in recent years. These obstacles were added to ensure much greater internet and mobile security. And today, identity verification involves a cumbersome mix of methods:
- Physical IDs — Once upon a time, personal ID numbers from driver’s licenses and passports were accepted in on-line verification. Today, news of large scale data breaches proves those IDs are easily compromised;
- Personal Biometrics were added as a second-factor verification via the recognition of customer voice patterns and the user’s device habits; and,
- Passwords, SMS authentication, and Personal Questions — Though effective, this method is time-consuming and somewhat frustrating for customers.
But what if a single verification solution could achieve the same purpose and deliver near real-time verification?
- What if instead of relying on internal customer intelligence gathering, you could cast a wider identity net by sharing transaction data anonymously with thousands of other digital businesses?
- What if you could greatly reduce friction and vastly improve your customer’s digital journey?
Such an advanced system exists today and is called the LexisNexis® Digital Identity Network®. Offered by LexisNexis Risk Solutions, it runs online verification for some of the largest financial and e-commerce firms in the world.
Very few telecoms have adopted the solution thus far, but it looms as an alluring paradigm shift that may revolutionize current identity and fraud control operations.
I spoke to telecom fraud expert and globetrotter, Jason Lane-Sellers of LexisNexis Risk Solutions, who is evangelizing the solution to telecoms.
Jason, of course, is a veteran fraud fighter and the current President of the CFCA. My conversation with him was a full hour long and filled with interesting detail on this ground-breaking solution.
So at 4,000 words, this interview is twice as long as our usual Black Swan story. But I found the content so packed with good examples and explanations that you’ll thank me for sparing the editor’s knife. Enjoy!
| Dan Baker, Editor, Black Swan Telecom Journal: Jason, our first conversation was in 2015 when you were a key champion of subscription fraud control at cVidya. And it seems you’re still in the identity business. |
Jason Lane-Sellers: Yes, Dan. In the late 2000s, I saw subscription fraud and account takeover on the rise. While at cVidya I was a voice saying, “Let’s not overlook subscription and account takeover fraud.”
The frustrating thing over the years was that we could never really address fraud prevention. The best we could do was see fraud happen and react to it.
Then I tuned in to the advanced things ThreatMetrix was doing on the digital identity side and I got excited about coming to work for them. Then a short time later, we were acquired by LexisNexis Risk Solutions, a global giant in the risk and information business who helps customers reduce risk and improve decision making. And so my role today is teaching them the language of “telecom-ese”.
| Can you gives us a quick backgrounder on LexisNexis Risk Solutions? |
Sure. LexisNexis Risk Solutions is owned by RELX, a global provider of information-based analytics and decision tools for professional and business customers. With more than 30,000 people, the group serves customers in more than 180 countries and has offices in about 40 countries.
In the last six years, LexisNexis Risk Solutions has been building up its analytics and risk portfolio, sometimes through acquisition. In 2018, they bought the firm I was employed at — ThreatMetrix — which operated one of the largest repositories of online digital identities in the world.
| Before we discuss what online digital identities are all about, can you cover a bit of the evolution that identity verification is going through? |
Yes. Traditionally, in the retail business, identity meant physical identity validation. You checked a person’s documents then validated their credit score and LexisNexis Risk Solutions was a leading provider of that kind of information in North America and Europe.
Physical identities, however, are problematic in an online world because consumer identity data is increasingly compromised.
We believe the way forward is to evolve today’s physical verification to digital verification. That is what we are championing here: enabling both physical and digital identity verification. It’s the digital side that is going to see more rapid growth.
We know the legacy way of digital authentication is limited in the new retail world. SMS one-time authentication is not reliable and passwords are frustrating for customers because they often forget them.
While the key challenge is to secure online transactions with customers, we’re determined to make mobile and online transactions as smooth and fast as possible, achieving a quality customer experience while monitoring for fraud and other threat vectors.
| What about telecoms? Are they on the path from physical to digital identity verification? |
Traditionally, mobile operators sold their devices through a retail outlet. Now, a great deal of phone buying happens online. Frankly, customers are demanding it since they already bank by phone and shop online.

Whether you love Amazon or loathe them, the digital experience they deliver is smooth and excellent and people are starting to expect that same online treatment from their traditional providers.
A key trouble for telecoms is they have yet to improve their own online experience to that higher level of simplicity.
Although most sales interaction still happens in the store or call center, when you interact with a telecom online or on a mobile phone today, they still ask for an ID and they usually ask a few questions to verify you.
But yes, I do think telecoms are ready to move to the next level. In recent years, they have put great energy into improving their Net Promoter Scores. Another driver is the roll-out of next generation LTE and 5G networks, which will require more streamlined and lower cost interactions with customers.
| And let’s not forget that telcos are the security watchdogs for the entire digital ecosystem who ride on our networks and use our mobile devices. |
Absolutely. Telcos are the conduit for the network, the infrastructure and security for everyone’s online experience.
We also know that the target of SIM swaps is not the telco, but the bank accounts of mobile phone users.
So this all points to the need for telcos to have their own digital protection network. A digital network identity solution will protect and improve the digital journey for their own customers and also remove the risk of becoming a conduit for fraud across the whole digital ecosystem.
| How is a digital entity captured and followed in the Digital Identity Network? |
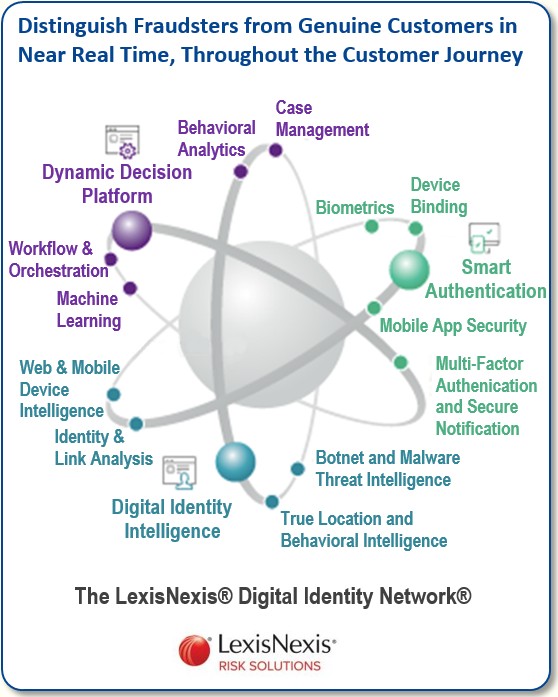
Here’s where digital identities provide a key advantage: they go way beyond relying on the data you are giving. They rely on the network to continuously learn and continue to monitor “digital entities” — real people, plus fraudsters pretending to be real.
Take myself as an example. I have a digital entity that is understood by looking at various things.
- Devices — In my case I use an iPhone, an iPad, and a PC, and I’m using those constantly throughout the day. The Digital Identity Network takes account of and understands all those device changes as part of my identity.
- Network access — How am I using those devices? Maybe it’s via my home WiFi network, the cell network or the WiFi at a café I frequent.
- Location — Where am I digitally interacting from and to? The Digital Identity Network can detect whether I am engaging from my usual locations or transacting from somewhere not normally associated with my profile, like Russia.
- Method of network access — Am I navigating in the clear or am I using a VPN or proxy? Fraudsters like to hide their activities as much as possible.
- Different email accounts for different purposes — Digital users typically have multiple emails. On my phone I might have five different email accounts. One is for family, another for business. A third is specifically used to collect spam. I may digitally interact with all of them over any given day.
- Interactions — Are the mobile apps and online places I frequent consistent or is there new remote access software being used in my latest transaction?
- Behavior — Are my behavioral biometric indicators consistent, like how I navigate a web page, enter data or use short cuts on my keyboard?
So if your network understands all those different elements, you begin to build up a solid digital picture of individual network users.
Now, traditionally this proved quite a challenge because these digital identities are not static. Across a 24-hour cycle, a user is bound to use different devices, lots of different locations and many different kinds of online interactions.
| So how is LexisNexis Risk Solutions sorting out digital identities through its network? |
What we have done is build a global digital network fed by thousands of customers, such as major banks, insurance companies, web sites, retail websites and online marketplaces. Since all these companies use our product, we can monitor digital traffic and build a network of digital identities on a massive scale — close to three billion identities on the network today.
Remember: Out of the seven billion people on the planet, there are significant parts of the globe where very little internet transactions happen at all. So the three billion identities we follow cover a huge portion of the active internet population.
In other words, when a telco comes and says, “Can we use your platform?” what we can do is actually verify personal identity specific to their devices and at various locations even before the consumer becomes a customer of the telco.
| So how can you identify a telco’s customer even before the telco shares detail with LexisNexis Risk Solutions? |
Let me start by saying that no private details about the customer are ever shared. Crowd sourcing in the digital world is not raw data where the user is exposed. Rather, data is collected and organized in an encrypted and tokenized manner so that only the originator has the details of the transaction.
Imagine a digital identity is your customer and she interacted with you two times in the past two weeks. How does the Digital Identity Network know it is she? We check all transactions across the network to understand what, where and how the digital identity elements are being used. This is done across all interactions (e.g. there may be 100 recent transactions) and we can simply identify potential risks or changes in the latest transaction.
Therefore, if they are highly trusted, we then allow that consumer to transact on the website again with a simpler user journey or we manage the user interaction more cautiously when risk is present. This allows true risk-based authentication and validation of user interactions, dependent on the type of interaction. This is all done in real time, not impeding the digital journey, which is the goal of all digital interactions.
| How fast can you identity the digital entity? What are some of the real-time steps you take to find a match? |
Well, let me share the experience of a customer of ours who has been in the telecom business for 25 years. Their customers are all interacting digitally and it could be across broadband, mobile, TV and/or other services.
Our objective is to fast track the user through the process and create an appropriate level of friction for that customer. For example, when the consumer is a long-term, established, trusted user applying for new service, we may choose not to perform external checks if we have confidently verified the interaction.
It starts when the person hits the sales landing page. If we use the solution at this point, we can start to analyze the digital entity performing the transaction immediately in order to help manage the customer journey. By performing a validation at an early stage, our customers can verify an element of risk even before they start progressing further into the digital interaction.
As they process further details on the webpage and start to process selections or click-through, more of the data is analyzed through a next-level risk assessment. If some of those details have not been associated with that identity before, we can identify potential fraud risks associated with this interaction (based upon elements such as device, location and details entered that are not associated with this digital identity).
At a simple level, let’s say the identity email address used in this application was utilized 20 times from 20 different applications in the past 24 hours and so the transaction raises an alert. This could be because a proxy is being used to hide the originating location of the transaction (purporting to be in New York when actually in Russia).
This allows our analysis to build digital identities in the Digital Identity Network, correlate them with a transaction and allow risk assessment on the transaction. These transactions are validated using rules and modeling to enable trusted utilization over periods of time. We then find good trust scores and can identify high risk actions within individual transactions and provide risk score indicators, all in real time as the customer lands on a page, negotiates a web journey or interacts with a mobile app.
This allows full management of the customer journey. Good, trusted customers get smooth frictionless journeys and risky customers can be given the appropriate risk-based journey.
| From what you’re just said, it sounds like your system is not only good at identifying customers, but also for tracking fraudsters. |
Actually we noticed in the e-commerce world that as soon as a company launches a new sales offering, the fraudsters go there right away to try and manipulate it.
In fact, we see across the network in e-commerce, close to one in five new sales interactions were attempts at fraud. That is significant. For our customers, we are able to identify and stop these fraud attempts before the fraud ever hits.
In the previous Telco example, they potentially could have had a 20% fraud rate, but they experienced next to no fraud with LexisNexis® ThreatMetrix®.
What they further found — after four or five weeks of our network stopping the attacks — was that the fraudsters gave up attempts at fraud because they could not get access. When a window is stuck closed in your house, you eventually stop trying to open it.
Eventually we brought their fraud attempts down from 20% to less than 2% and that is ATTEMPTED fraud, not actual fraud.
As fraudsters process their digital journey, we can capture much valuable info from an investigation and analysis point of view. We learn what details and methods they are trying to use, both digital and account-based. We may see the same fraudster rotate through 20 different addresses in his or her attempts and we also see correlations of attackers across industries.
This allows customers to prevent related attacks. In this way, we built a smart intelligent network by tracking very specific inputs of the fraudsters. It takes a network to catch a network.
| Are the companies using the Digital Identity Network able to save some money on risk validation queries to other firms? |
That’s what our customers tell us. For a fraud application, even if you found the fraud manually, the customary practice was to do a validation or credit check with a third party source. And that might cost you a dollar each time.
However, if you have good intelligence at the very top of the waterfall — at the start of the identity verification — it means we remove the need to do extra costly checks.
This was what was exciting to me. Our solution is truly preventative, without being a drag on the customer experience! Our customer is able to maintain total control of their journey with their users.
| How do you see consortium networks changing the practice of telco fraud control? |
My concern is the current, archaic structure for telcos to handle fraud concerns is not suited to solving the problem in the right way.
We’re still talking mostly about voice call fraud, SMS fraud and Wangiri. Yes, these frauds are still happening and are still important. However, the way we deal with those problems is still reactive. Telcos wait for things to happen. They investigate after they have been hit.
When I look back, it was always about putting in more and more controls. The trouble with that is they end up blocking consumers, blocking SIMs, and those kinds of things.
In the digital world, no one has the time to do that. One bad media story about a telco being the target of fraud is enough to cause big consumer defections and lawsuits. How do you factor that into your risk formula? One of our recent studies on the true cost of fraud found that for every dollar lost to fraud, retailers in particular pay $3.13 on average.
I foresee the fraud department will face big pressure from marketing, sales, customer services, finance and other internal teams to become more anticipatory than reactionary.
In the digital world, if the customer cannot get through to the place they want to go in a few clicks, they will go somewhere else. Then marketing people will say, “You can’t do that fraud check. It will cost us money because it will cause the sale to take 10 minutes instead of five. We can’t have that. It’s got to be a real-time customer interface.”
The goal is to deliver a far simpler consumer experience.
The beauty of our approach is that enterprises are doing real prevention at the same time they are recognizing 99% of its good consumers. That is great because you can then improve the experience for those users, making things go smoother and more quickly.
Some of our customers have actually eliminated passwords as a tool. They are using our digital network to provide the same protection.
| Wow, it’s shocking to think you can get rid of passwords. |
Yes, but that is the type of interaction experience you can achieve as the Digital Identity Network raises the ability to verify accurately within the right process.
At one client we matured to the point of allowing their consumers to go straight into their app without even asking for a password or username.
Interestingly, their consumers became alarmed at not having to enter a username or password, saying, “Are you really protecting me?”
To keep customers happy, they modified the user interface a bit to include what was perceived as an acceptable level of friction. We still verified the customer in real-time, but they also popped up a “security check in progress” notice on the mobile screen that ran for a few seconds. This little change gave customers more security assurance.
| I’ll bet the early adopters of your system really took a risk, but I suspect it’s all paid off for them now that your Digital Identity Network has grown so big. |
It’s true. LexisNexis Risk Solutions now has 7,000 customers around the globe using this network. They include many of the top 20 European and U.S. banks. Then there are major retail companies and e-commerce firms. We also serve a big number of large insurance, healthcare and online gaming companies. Our network partners come from all corners of the online business world.
When I give conference talks, I demonstrate how our consortium network works by having everyone in the conference stand up for a moment then ask, “How many of you are using this one particular app?” For those who raise their hand, I ask them to sit down. Then I ask, “Who uses this one particular website?” And then I ask those people sit down.
In any room around the globe after throwing out only the names of five or six of our customers using our consortium, everyone will have sat down.
And it’s that kind of breadth that allows us to have a powerful platform.
| Are telecoms ready for adopting a solution like this? |
I think they are. They want to do more selling online because digital selling is more effective and less costly.
In addition, online selling is what their customers expect. People nowadays are less inclined to have a buying conversation with another person. Maybe that is a human failing in the digital age. Regardless, the trend is unmistakable: online buying has taken over at least in terms of sales volume and where the world’s trending.
When you face that business reality of the 2020s, telcos are very naturally receptive to the kind of solution LexisNexis Risk Solutions offers.
The other important angle is the financial risk.
Within all my banking, social media and personal interactions — even gas and utility transactions — all of them are moving online. If someone stole my online identity by penetrating my mobile phone, they could access everything in my life. That could lead to a fraudster robbing a customer of his entire life savings.
That is the kind of nightmare scenario telcos are thinking about now. Fraudsters with a SIM card swap, porting a number or a synthetic identity can easily take over accounts. This element needs protection from the telcos rather than blaming the end target of the attack.
| The anonymous intelligence from those 7,000 customers is what drives the LexisNexis Risk Solutions system. Is there still a role for biometrics? |
Absolutely, we use biometrics as well. We find biometrics is most useful when you do not have the customary key identifier in the digital stream.
Here are some examples of the biometric factors we look to track:
- Does the person cut and paste when entering text? Or is the entity computerized, entering text with orchestrated credentials. Fraudsters often use these techniques to see what entries are valid, then perform a concerted attack on active accounts.
- How long does it take a user to go from one page to another? How are they navigating the website (normal or streamlined)?
- How is the person holding the phone? Are they right or left-handed? Do they type in their passwords slowly or quickly?
- How often does a person use their mouse or keyboard? What is their speed and smoothness of tracking?
The helpdesk technicians use remote access software to troubleshoot your PC. Fraudsters use the same kind of software to take over your accounts. The telltale sign is that remote access takes a couple seconds longer than normal to click from page to page.
So if someone logs onto your account, but with totally different biometrics — different location and different device than we have seen before — then all these factors add up to say, “Increase the risk score,” or “This is likely to be an attack.”
Biometrics is important especially if you factor in the context of what is going on in the transaction. The main power of identity verification is in the Digital Identity Network itself. However, if biometrics is blended with network analysis, you then have something very powerful.
|
Jason, thanks for this detailed brief. This is quite a paradigm shift,
I think. Previously a company digitally protected itself by building up
internal intelligence on the physical records and behavioral habits of its customers.
What you’re saying is that a telco can get out of the game of in-house built digital identity analysis. Instead it can access a much wider, safer and more real-time security blanket by sharing its data anonymously in a virtual partnership with a 7,000-customer-strong consortium. |
Thanks, Dan. LexisNexis Risk Solutions has been very successful with banks and fintechs and is a leading digital identity player in those industries now. We even help secure media and digital content providers, so we are getting into other new digital frontiers. Telecoms need to be part of that.
There are just a handful of telecoms using such a system today, so we predict wide adoption once the word gets out.
The beauty of all this is that telcos can leverage the power of an identity network and fully protect consumer privacy at the same time.
I think this also presents a fantastic opportunity to upgrade the consumer experience. The key paradox is this: your telco is selling the smartest cell phones enabling the best digital journeys, and yet the digital life the telco delivers to its users is sub-par to the major digital retailers of the world.
My role is to educate telcos about all the unnecessary process steps they can remove by using the Digital Identity Network. Once they see the power of the network approach, it's no longer a challenge for telcos to see how they can evolve from an archaic manual process to something that delivers much greater outcomes for their company and their consumers.
Copyright 2020 Black Swan Telecom Journal
Black Swan Solution Guides & Papers
- Expanding the Scope of Revenue Assurance Beyond Switch-to-Bill’s Vision — Araxxe — How Araxxe’s end-to-end revenue assurance complements switch-to-bill RA through telescope RA (external and partner data) and microscope RA (high-definition analysis of complex services like bundling and digital services).
- Lanck Telecom FMS: Voice Fraud Management as a Network Service on Demand — Lanck Telecom — A Guide to a new and unique on-demand network service enabling fraud-risky international voice traffic to be monitored (and either alerted or blocked) as that traffic is routed through a wholesaler on its way to its final destinations.
- SHAKEN / STIR Calling Number Verification & Fraud Alerting — iconectiv — SHAKEN/STIR is the telecom industry’s first step toward reviving trust in business telephony — and has recently launched in the U.S. market. This Solution Guide features commentary from technology leaders at iconetiv, a firm heavily involved in the development of SHAKEN.
- Getting Accurate, Up-to-the-Minute Phone Number Porting History & Carrier-of-Record Data to Verify Identity & Mitigate Account Takeovers — iconectiv — Learn about a recently approved risk intelligence service to receive authoritative and real-time notices of numbers being ported and changes to the carrier-of-record for specific telephone numbers.
- The Value of an Authoritative Database of Global Telephone Numbers — iconectiv — Learn about an authoritative database of allocated numbers and special number ranges in every country of the world. The expert explains how this database adds value to any FMS or fraud analyst team.
- The IPRN Database and its Use in IRSF & Wangiri Fraud Control — Yates Fraud Consulting — The IPRN Database is a powerful new tool for helping control IRSF and Wangiri frauds. The pioneer of the category explains the value and use of the IPRN Database in this 14-page Black Swan Solution Guide.
- A Real-Time Cloud Service to Protect the Enterprise PBX from IRSF Fraud — Oculeus — Learn how a new cloud-based solution developed by Oculeus, any enterprise can protect its PBX from IRSF fraud for as little as $5 a month.
- How Regulators can Lead the Fight Against International Bypass Fraud — LATRO Services — As a regulator in a country infected by SIM box fraud, what can you do to improve the situation? A white paper explains the steps you can and should you take — at the national government level — to better protect your country’s tax revenue, quality of communications, and national infrastructure.
- Telecom Identity Fraud 2020: A 36-Expert Analysis Report from TRI — TRI — TRI releases a new research report on telecom identity fraud and security. Black Swan readers can download a free Executive Summary of the Report.
- The 2021 State of Communications-Related Fraud, Identity Theft & Consumer Protection in the USA — iconectiv — This 49-page free Report on communications-related fraud analyzes the FTC’s annual Sentinel consumer fraud statistics and provides a sweeping view of trends and problem areas. It also gives a cross-industry view of the practices and systems that enable fraud control, identity verification, and security in our “zero trust” digital world.
Recent Stories
- Epsilon’s Infiny NaaS Platform Brings Global Connection, Agility & Fast Provision for IoT, Clouds & Enterprises in Southeast Asia, China & Beyond — interview with Warren Aw , Epsilon
- PCCW Global: On Leveraging Global IoT Connectivity to Create Mission Critical Use Cases for Enterprises — interview with Craig Price , PCCW Global
- Subex Explains its IoT Security Research Methods: From Malware & Coding Analysis to Distribution & Bad Actor Tracking — interview with Kiran Zachariah , Subex
- Mobile Security Leverage: MNOs to Tool up with Distributed Security Services for Globally-Connected, Mission Critical IoT — interview with Jimmy Jones , Positive Technologies
- TEOCO Brings Bottom Line Savings & Efficiency to Inter-Carrier Billing and Accounting with Machine Learning & Contract Scanning — interview with Jacob Howell , TEOCO
- PRISM Report on IPRN Trends 2020: An Analysis of the Destinations Fraudsters Use in IRSF & Wangiri Attacks — interview with Colin Yates , Yates Consulting
- Telecom Identity Fraud 2020: A 36-Expert Analyst Report on Subscription Fraud, Identity, KYC and Security — by Dan Baker , TRI
- Tackling Telecoms Subscription Fraud in a Digital World — interview with Mel Prescott & Andy Procter , FICO
- How an Energized Antifraud System with SLAs & Revenue Share is Powering Business Growth at Wholesaler iBASIS — interview with Malick Aissi , iBASIS
- Mobileum Tackles Subscription Fraud and ID Spoofing with Machine Learning that is Explainable — interview with Carlos Martins , Mobileum


