| © 2022 Black Swan Telecom Journal | • | protecting and growing a robust communications business | • a service of | |
| Email a colleague |
January 2017
The Early Warning Power of IPRN Test Call Detection in Blocking IRSF Fraud

International Revenue Share Fraud (IRSF) remains the primary means criminals use to defraud telecoms of many billions of dollars per year.
Just one successful IRSF attack can easily cost an operator or enterprise $50,000 after only a weekend of massive calling to high-tariff numbers around the globe.
However, in recent years, fraud management (FM) experts have learned to protect themselves better by detecting the test calls made to International Premium Rate Numbers (IPRN) prior to fraudsters launching their IRSF attacks.
To explain the importance of IPRN test calls and the value of detecting them via commercial databases, I spoke with Colin Yates, a leading FM consultant and the former head of Fraud Management at Vodafone.
| Dan Baker, Editor, Black Swan: Colin, to begin, it seems odd that fraudsters would openly reveal the test call numbers used prior to launching an IRSF attack. Why do they do that? |
Colin Yates: Dan, the fraudsters use test calls because it’s a practical necessity. Before a fraudster commences his IRSF attack, he needs to confirm that the device he’s using to make the calls (through stolen handset/SIM card, hacked PBX, etc) and the country he’s calling from permit calls to terminate in the IRSF country.
The test call typically lasts one minute or less, and is placed immediately prior to an IRSF attack, or is mixed in with the fraud records as the fraudster is preparing to change his calling destination.
| OK, excellent. Now before we get into the details of how IPRNs and test numbers are employed, can you review for us the basic flow of criminal operations in IRSF fraud — it’s rather complex. |
Dan, it’s easier to understand if you break the fraud down into the roles of the three key parties who must coordinate to pull off a successful IRSF attack:

The Call Generator (often called the Fraudster) pumps a massive volume of calls — in a relatively short period of time — through a hacked device (PBX or cellphone/SIM). Those calls are sent to high-tariff telephone numbers across the globe. The Call Generator may also manage global traffic flow through transit operators, some of whom may be in on the fraud. However, managing the global traffic flow may also be completed by the IPRN Provider.

The Hacker uses brute force hacking of passwords to break into the PBX machines, or they steal cellphones and SIM cards — the devices to pump fraudulent call through. The Call Generator often pays the Hacker a fixed fee for the password for a PBX or for a particular mobile device.
The IPRN Provider is the insider party who has control over the destination
phone numbers within the country the Call Generator calls into.

The numbers called can be those allocated to a type of 900-number/ information service, or an unallocated set of numbers. Some may be provided to him by the number range owner. Other numbers may be simply misappropriated, or hijacked and used without the number range owner’s knowledge.
In all cases, the IPRN provider inserts himself into the billing stream or gets a payoff from an insider. When payment is received from the transit operator, the IPRN Provider then pays the Call Generator the agreed-upon fee and pockets the rest himself.
(NOTE: Not all IPRN Providers are involved in fraud. Some are run a legitimate business and provide IPR Numbers for billing, content services etc. Most of these providers monitor their traffic to identify and block fraud).
| Sounds like fraudsters need to coordinate quite a bit. The Call Generator needs to know what routes are available and the current payoff rates the IPRN Provider is offering. Meanwhile, the parties want to exchange that information anonymously. |
Exactly, and this why the IPRN Provider information is shared anonymously through public websites and online registration forms.
Today there are more than 120 of these websites around the globe. It’s here where the Call Generators decide which IPRN providers and call destinations they will use. A typical Rate Card on these sites is shown below:
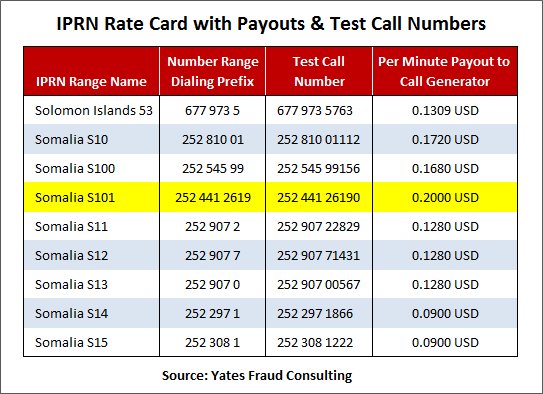
So in the example above, the Call Generator goes to say, IPRNsite.com, and selects Somalia route S101 as the destination he will pump calls to.
And in the rate card you see that by sending calls to the +252-4412619 number range, the IPRN Provider will pay him 0.2000 USD for every minute of traffic generated into that range.
So the Call Generator will make a test call to 252-44126190 and if that’s successful, he’ll make arrangements with the IPRN Provider to start his revenue share fraud to that number range and obtain more numbers to do this.
Now, there’s generally a time lag of 15 and 60 minutes between the time the test call is made and the start of IRSF call pumping. Time is needed for the fraudsters to coordinate payment terms and other details with each other.
So given this time delay, you can see why detecting the test number dialled provides early warning of an impending attack. If this number is known by the originating operator, the number can be “hot listed” as a high risk number, and the IRSF attack can be blocked before it even starts.
| It’s interesting to hear how the fraudsters work with each other to set up an IRSF attack. So how do operators actually do “early warning” test call detection of imminent IRSF attacks? |
Dan, operators need to either track the IPRN websites on their own or work with a commercial firm who maintains an up-to-date IPRN database of global numbers.
For the past 3 years, my company, Yates Fraud Consulting Limited, has teamed up with FRSLabs to harvest these IPR test numbers across the 120+ known IPRN Providers websites.
Our test number database — with almost 400,000 numbers today — is now being used by 40 telecom operators worldwide. We update the database twice a month — the typical frequency at which IPRN providers update the test numbers on their on-line catalogs.
What’s interesting to note is the increased rate of new IPRN numbers being added to these websites. In January 2016, for example, we added 9,800 new numbers to the database. However, in January 2017, new numbers jumped to 27,000.
| And what’s been the experience of operators using your IPRN database? |
I think every one of them consider our IPRN database to be a critical tool in their defence against IRSF. Some have told us the database is stopping 75% of their IRSF attacks.
All of them are using the database to drive a ‘called number hotlist’ which raises an alert once a call is matched to a known test number.
| Is there an objective measure of how successful the IPRN database is in stopping IRSF fraud? |
It would be great if an objective measure existed, but fraud data is so scattered that any benchmark would probably not be statistically valid.
However, a number of operators — who have experienced IRSF losses already — have contacted us to see if using our database might have helped them prevent their IRSF loss.
So far, in 100% of the operators sending us their IRSF call records, we found telltale test call numbers in our database.
In one unusually big IRSF case, the operator lost $2.3 million after an attack lasting only three days. Details of the case are in the diagram below.

| Colin, thanks for this splendid brief on the complexities of IPRN and the value of test call number detection. Can you tell us how an operator can gain access to your IPRN database? |
Sure, Dan. Access to our PRISM database is available to telecom operators for a modest annual subscription. The amount can easily be recovered if it assists a new user avoid the loss of just half a day of a modest IRSF attack. Generally access to our database can be finalised within 24 hours of applying.
Copyright 2017 Black Swan Telecom Journal
Black Swan Solution Guides & Papers
- Expanding the Scope of Revenue Assurance Beyond Switch-to-Bill’s Vision — Araxxe — How Araxxe’s end-to-end revenue assurance complements switch-to-bill RA through telescope RA (external and partner data) and microscope RA (high-definition analysis of complex services like bundling and digital services).
- Lanck Telecom FMS: Voice Fraud Management as a Network Service on Demand — Lanck Telecom — A Guide to a new and unique on-demand network service enabling fraud-risky international voice traffic to be monitored (and either alerted or blocked) as that traffic is routed through a wholesaler on its way to its final destinations.
- SHAKEN / STIR Calling Number Verification & Fraud Alerting — iconectiv — SHAKEN/STIR is the telecom industry’s first step toward reviving trust in business telephony — and has recently launched in the U.S. market. This Solution Guide features commentary from technology leaders at iconetiv, a firm heavily involved in the development of SHAKEN.
- Getting Accurate, Up-to-the-Minute Phone Number Porting History & Carrier-of-Record Data to Verify Identity & Mitigate Account Takeovers — iconectiv — Learn about a recently approved risk intelligence service to receive authoritative and real-time notices of numbers being ported and changes to the carrier-of-record for specific telephone numbers.
- The Value of an Authoritative Database of Global Telephone Numbers — iconectiv — Learn about an authoritative database of allocated numbers and special number ranges in every country of the world. The expert explains how this database adds value to any FMS or fraud analyst team.
- The IPRN Database and its Use in IRSF & Wangiri Fraud Control — Yates Fraud Consulting — The IPRN Database is a powerful new tool for helping control IRSF and Wangiri frauds. The pioneer of the category explains the value and use of the IPRN Database in this 14-page Black Swan Solution Guide.
- A Real-Time Cloud Service to Protect the Enterprise PBX from IRSF Fraud — Oculeus — Learn how a new cloud-based solution developed by Oculeus, any enterprise can protect its PBX from IRSF fraud for as little as $5 a month.
- How Regulators can Lead the Fight Against International Bypass Fraud — LATRO Services — As a regulator in a country infected by SIM box fraud, what can you do to improve the situation? A white paper explains the steps you can and should you take — at the national government level — to better protect your country’s tax revenue, quality of communications, and national infrastructure.
- Telecom Identity Fraud 2020: A 36-Expert Analysis Report from TRI — TRI — TRI releases a new research report on telecom identity fraud and security. Black Swan readers can download a free Executive Summary of the Report.
- The 2021 State of Communications-Related Fraud, Identity Theft & Consumer Protection in the USA — iconectiv — This 49-page free Report on communications-related fraud analyzes the FTC’s annual Sentinel consumer fraud statistics and provides a sweeping view of trends and problem areas. It also gives a cross-industry view of the practices and systems that enable fraud control, identity verification, and security in our “zero trust” digital world.
Recent Stories
- Epsilon’s Infiny NaaS Platform Brings Global Connection, Agility & Fast Provision for IoT, Clouds & Enterprises in Southeast Asia, China & Beyond — interview with Warren Aw , Epsilon
- PCCW Global: On Leveraging Global IoT Connectivity to Create Mission Critical Use Cases for Enterprises — interview with Craig Price , PCCW Global
- Subex Explains its IoT Security Research Methods: From Malware & Coding Analysis to Distribution & Bad Actor Tracking — interview with Kiran Zachariah , Subex
- Mobile Security Leverage: MNOs to Tool up with Distributed Security Services for Globally-Connected, Mission Critical IoT — interview with Jimmy Jones , Positive Technologies
- TEOCO Brings Bottom Line Savings & Efficiency to Inter-Carrier Billing and Accounting with Machine Learning & Contract Scanning — interview with Jacob Howell , TEOCO
- PRISM Report on IPRN Trends 2020: An Analysis of the Destinations Fraudsters Use in IRSF & Wangiri Attacks — interview with Colin Yates , Yates Consulting
- Telecom Identity Fraud 2020: A 36-Expert Analyst Report on Subscription Fraud, Identity, KYC and Security — by Dan Baker , TRI
- Tackling Telecoms Subscription Fraud in a Digital World — interview with Mel Prescott & Andy Procter , FICO
- How an Energized Antifraud System with SLAs & Revenue Share is Powering Business Growth at Wholesaler iBASIS — interview with Malick Aissi , iBASIS
- Mobileum Tackles Subscription Fraud and ID Spoofing with Machine Learning that is Explainable — interview with Carlos Martins , Mobileum


