| © 2022 Black Swan Telecom Journal | • | protecting and growing a robust communications business | • a service of | |
| Email a colleague |
June 2017
Telecoms Need to Step Up their Game in Subscription Fraud and Customer Onboarding Control

Know thy customer. Those words are the spearhead of the massive cross-industry movement to block criminals from penetrating customer accounts or gaining access to services that can absolutely kill a business.
The implications of stopping subscription fraud are enormous: the majority of telecom fraud and bad debts can be stopped if a telecom is vigilant as it onboards customers for services.
After all, a fraudster can only abuse your service if you let them have access in the first place.
Today the banking/financial industry, in particular, is very serious about protecting their perimeter: that industry has invested enormously in biometric systems and financial compliance accounting.
Now telecoms certainly care about their onboarding problems but possibly dismiss the solution — they do not fund the internal customer verification systems that can screen customers better and at a much lower cost than paying external service bureaus to perform the same task.
To this end, I recently interviewed Luke Taylor, Chief Commercial Officer of Neural Technologies, the leading supplier of customer onboarding and subscription fraud control systems to the telecom industry.
In Luke’s insightful briefing he shows why the onboarding is bound to become more critical, as well as covering key topics such as: delivering first-class onboarding controls; selecting risk mitigation targets; and integrating back end systems.
| Dan Baker, Editor, Black Swan Journal: Luke, I guess a telecom could easily go out of business today if it solely relied on external service bureaus to screen customers for services. |
Luke Taylor: Yes, Dan, the first question that needs to be asked is: how can we onboard or acquire a customer at minimal cost and of course minimal risk.
This is especially important at the low end of the market. If a customer is only generating $100 a year for you, you simply must lower the costs to acquire them in the first place to maximize your margin.
So at Neural we try to figure out: what simple checks can we carry out before the need to engage a third party service bureau for an additional credit check.
Why would you ever send a subscriber’s name off to Experian or some other bureau and pay for their respective service if you already know that this prospect is on your black list, or that they have already been declined for another one of your services?
Operators that offer a variety of services need to get their different departments talking to one another because the subscriber will try to get through any door that is open to them.
For example, some fraudsters will try to subscribe through the cable service first. If they succeed, they would then move onto other services. The costs of connecting these cable customers are substantial, and once the wheels are turning on the delivery, then those costs are being expended. Others will try to penetrate the mobile side, with the objective of stealing high value phones and reselling them as well as maximizing the service plan.
Now some of these are very expensive handsets. So if you’re selling an Apple iPhone, you’d better spend a little more time ensuring you are taking on legitimate customers. With subsidized handsets, short-term loans, and other techniques to acquire customers, there is a high-risk level attached to retrieving your initial investment in the customer onboarding process.
| What is involved in delivering first-class control in subscription fraud and customer onboarding? |
First of all, if your IT system is not good at crossing your t’s and dotting your i’s during verification, it’s very easy for fraudsters to discover your vulnerabilities and infiltrate your onboarding business processes.
You basically need to determine two things: 1) is the customer able to pay his bills?; and 2) is he likely to use the service legitimately?
To answer those questions, at Neural Technologies we first look at the in-house black list or the data warehouses where such insightful data could be stored. We also look at the information the subscriber is giving us and combine this data to see if there is a similar person on the network already with account details that are only slightly different. Maybe the same credit card details, maybe the same contact number, etc.
It’s amazing how many people try to get back on the service after they’ve been denied. And the way they often do that is to change something in their profile in a very slight way. For example, the address could be fudged: instead of "5 New York Avenue", it might be "5th and New York Avenue".
The result of our analysis is a statistical likelihood that the person being checked is, say, 85% likely to be Michael Jones, the same person who is on our black list. There are many repeat applications, and similar functions used by our system, and we check everything from email addresses and telephone contacts numbers to credit cards and nearby addresses of other blacklisted customers.
We can also check aspects like national IDs. We will basically use anything the subscriber provides in an application to bounce our analysis off of.
Only once you finish these sanity checks, if the onboarding person is still maybe in the gray area, that’s the point when you should go out and request more information from a third party service bureau. But the real objective is to greatly reduce the need to go outside and pay unnecessary fees.
And if their credit facility is not good enough to be on a subsidized iPhone contract for example, you do not want to turn them away. So maybe offering them a plan using a lower-cost brand phone could be feasible.
Now, one of the valuable things we do here at Neural is wrap workflow around a telecom’s credit checking processes. Internally you can verify a number of things based on historic data and other triggers like address validity, credit card numbers, bank account/sort codes and much more. These can be checked at no cost or a very low cost with internal data or some standard API’s before a telco resorts to spend serious money on a bureau to do a credit check/reference.
After this step if the application needs further validation, we direct the decision flow to third party bureaus or possibly to a call centre operative to garner further information, supply additional documentation, etc.. Some operators use many external services bureaus, and use them for different types of applications, i.e. SME’s. Others stick to relying on one bureau.
We also serve banks who are looking for the same sort of risk mitigation as telecoms. Will I get my money back by allowing this person to setup a credit card facility, bank account, loan, etc.?
So by looking at subscribers in this way, the control of the onboarding of customers and stopping subscription fraud is really just another name for proactive revenue assurance.
| Do you feel the risks of onboarding bad customers are higher than they were before? |
Yes, for a number of reasons. The service volumes in telecommunications are ramping up, even though revenues are staying pretty flat. That means that telcos need to cut costs to the bone to ensure profitability; having full understanding of your financial exposure is crucial for this.
If you allow too many people to obtain your service and they are not profitable, that spells trouble.
The other risk is that telecoms are shifting a greater portion of their revenue toward small medium size businesses — and away from everyday consumers and large business accounts. The trouble is that the exposure is much greater with this approach. For example, a fraudster could persuade you to set up 10 DSL lines for a fictional "business" and then they make a ton of calls in 2 months time and never pay. Likewise they could also request 20 mobile handsets for their employees, then disappear.
In the more mature regions — North America, Europe, Middle East and East Asia — good subscription fraud controls are a key requirement. The developing markets in Africa, South America, and Southeast Asia will be slower to adopt, but they’ll soon need to do this too. As consumers demand more post paid, higher value services and the like, telcos in these regions will need to catch up.
In more mature nations, customer financial data is everywhere and usually easy to access. In the developing worlds with less available historic data, we can still stitch the data together by the wise use of internal data. For example, by possibly examining the calling profile, top up behavior, etc. of an individual you can create a limited profile that can be used to assess their financial risk.
This study of mobile phone activity can be developed into a tremendous risk mitigation tool because so many transactions are going through each person’s mobile device. Such initiatives I see will expand in the near future to assist in reducing the number of unbanked/financially excluded.
| One of Neural Tech’s claims to fame is serving Kenya’s Safaricom and supplying the fraud system for their huge mobile money service M-PESA. What’s happening there? |
Yes, Safaricom has broken all sorts of records. As you know, M-PESA is the established way companies send weekly pay home to pay the families of relatives working in the city. And today, more money is transmitted through M-PESA than through Kenya’s national bank. The contribution it has made to increase GDP in Kenya in substantial.
A big initiative now with such visible success of mobile money/remittance services such as M-Pesa at Safaricom and other mobile money operators is adding money laundering controls.
Operators never worried much about compliance with banking controls, but now that telcos are offering more financial services, they are getting pressure to implement these more rigorous financial controls.
One of the drivers of this is the US government who instigated the Patriot Act, who is saying to countries: if you want to trade with us, you need to make sure all your financial services align with strict anti-money laundering policies.
There is now the Financial Action Task Force (FATF) and its Policy on Prevention of Money Laundering and Terrorist Financing.
So that’s a new service that Neural offers our customers — to monitor their transactions for money laundering. Even e-commerce transitions are increasingly falling under this category.
These anti-money laundering systems are also considered crucial to law enforcement as they try to identify potential terrorists or criminals.
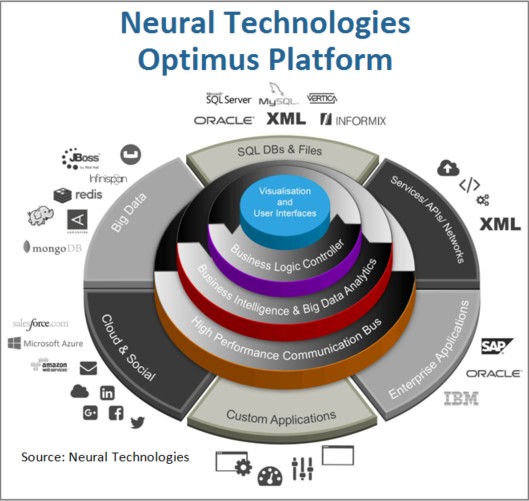
| How can a small operator manage its fraud and credit risks best? If you’re an MVNO or OTT provider, risk management can be daunting to figure out. How can they pinpoint their system needs and move forward confidently? |
Well, when we go in, we have them take a look at the big picture first. What are your risks? IRSF is one of them. Roaming and subscription fraud are others. Bad debt is still another. These are hard dollar losses, not opportunity to make money within your business.
If you have a big comprehensive risk solution with lots of bells and whistles, you may not have the time or resources to manage that. Systems are better managed in smaller slices because you always need someone to then look at all the process issues, investigate them, and close them down. If you do not have the infrastructure in place to manage that, then you’re not going to get any productivity out of the system. Timeliness is critical in such a quick moving industry, where over time the risk of substantial losses becomes vast.
You need to understand your priorities. If the priority is International Revenue Share Fraud IRSF, (i.e. this is causing the biggest challenge) then you need to get that system up and running. And most importantly — show tangible results to senior management for improving in IRSF control.
Only this way can you win the business case for diversifying and starting to look at broader threats.
And even then, if your team is only three people, you can’t accomplish too many things. How are you going to actually monitor it all?
So that’s where our ability to come in and deliver a foundation is very helpful. What we usually do is give them the basics to get up and running in one fraud or risk area — and then we sit down and go through the processes.
| Can you walk me through a typical implementation, Luke? How do you work with clients to get them rolling? |
Whenever we deploy Revenue Assurance and fraud systems, the biggest hurdle is almost always the data discovery aspect. The customer doesn’t quite understand his own data or its availability — that’s the longest pole in the tent. For instance:
- Can we find this data?
- Where is this data?
- What does this data mean?
- What do these fields match with?
- When do I know my data is outdated?
- How does database ABC map with database XYZ?
The initial stages of a customer engagement are crucial. In order to get data into a useful format for analysis, we need help from the IT and network teams to identify and locate the data sources. To make good decisions, you need to blaze paths to an organization’s reliable information sources.
Time is precious too because the IT and network teams can be pulled away anytime to other priorities like billing, CRM, or the network side.
So it’s a huge systems integration problem. We need to take feeds from data scattered all over the place. And in many cases the fraud and RA teams don’t fully appreciate the context of their data.
| In terms of data management and integration, which area is easier: revenue assurance or fraud control? |
I would say revenue assurance is a bit easier because it’s more repeatable.
Once you configure the RA systems and the data feeds are coming in, you’re doing your accounting, reconciliation, and other checks. This will continue until something at the source changes, for instance, the data sources change or a new network switch or billing system comes in.
Fraud is trickier because you are layering on top of those things, and the fraudster is constantly changing methods to attack you. The introduction of new services also bring new challenges.
Fraud is also steadily adopting analytics tools used in marketing. For instance, social network analysis techniques are as useful in fraud as they are in marketing campaigns.
We learn how fraudsters work in teams. You notice similarities and that enriches your ability to predict and analyze criminal behavior. You notice a terrorist is in Sierra Leone. OK, who does he travel with? Who’s near him?
| Thanks for this interesting briefing, Luke. Fraud control is often seen as merely a technical software issue. But as you've shown, a surprising degree of depth is needed to fit the software to the organization’s data sources, prioritize risk mitigation programs, analyze criminal behavior, and comply with international money laundering controls. |
Dan, the good thing is there’s enough integration complexity in the fraud sphere to keep us busy for a very long time : — )
Actually, some customers are even asking us to help them solve integration problems outside risk management.
So we now productize our data integration platform and use it to help IoT ecosystem providers merge the business models of their multiple IoT service providers, then aggregate and mediate their data. So we’ve got a side gig going on in the digital transformation and integration game.
Copyright 2017 Black Swan Telecom Journal
Black Swan Solution Guides & Papers
- Expanding the Scope of Revenue Assurance Beyond Switch-to-Bill’s Vision — Araxxe — How Araxxe’s end-to-end revenue assurance complements switch-to-bill RA through telescope RA (external and partner data) and microscope RA (high-definition analysis of complex services like bundling and digital services).
- Lanck Telecom FMS: Voice Fraud Management as a Network Service on Demand — Lanck Telecom — A Guide to a new and unique on-demand network service enabling fraud-risky international voice traffic to be monitored (and either alerted or blocked) as that traffic is routed through a wholesaler on its way to its final destinations.
- SHAKEN / STIR Calling Number Verification & Fraud Alerting — iconectiv — SHAKEN/STIR is the telecom industry’s first step toward reviving trust in business telephony — and has recently launched in the U.S. market. This Solution Guide features commentary from technology leaders at iconetiv, a firm heavily involved in the development of SHAKEN.
- Getting Accurate, Up-to-the-Minute Phone Number Porting History & Carrier-of-Record Data to Verify Identity & Mitigate Account Takeovers — iconectiv — Learn about a recently approved risk intelligence service to receive authoritative and real-time notices of numbers being ported and changes to the carrier-of-record for specific telephone numbers.
- The Value of an Authoritative Database of Global Telephone Numbers — iconectiv — Learn about an authoritative database of allocated numbers and special number ranges in every country of the world. The expert explains how this database adds value to any FMS or fraud analyst team.
- The IPRN Database and its Use in IRSF & Wangiri Fraud Control — Yates Fraud Consulting — The IPRN Database is a powerful new tool for helping control IRSF and Wangiri frauds. The pioneer of the category explains the value and use of the IPRN Database in this 14-page Black Swan Solution Guide.
- A Real-Time Cloud Service to Protect the Enterprise PBX from IRSF Fraud — Oculeus — Learn how a new cloud-based solution developed by Oculeus, any enterprise can protect its PBX from IRSF fraud for as little as $5 a month.
- How Regulators can Lead the Fight Against International Bypass Fraud — LATRO Services — As a regulator in a country infected by SIM box fraud, what can you do to improve the situation? A white paper explains the steps you can and should you take — at the national government level — to better protect your country’s tax revenue, quality of communications, and national infrastructure.
- Telecom Identity Fraud 2020: A 36-Expert Analysis Report from TRI — TRI — TRI releases a new research report on telecom identity fraud and security. Black Swan readers can download a free Executive Summary of the Report.
- The 2021 State of Communications-Related Fraud, Identity Theft & Consumer Protection in the USA — iconectiv — This 49-page free Report on communications-related fraud analyzes the FTC’s annual Sentinel consumer fraud statistics and provides a sweeping view of trends and problem areas. It also gives a cross-industry view of the practices and systems that enable fraud control, identity verification, and security in our “zero trust” digital world.
Recent Stories
- Epsilon’s Infiny NaaS Platform Brings Global Connection, Agility & Fast Provision for IoT, Clouds & Enterprises in Southeast Asia, China & Beyond — interview with Warren Aw , Epsilon
- PCCW Global: On Leveraging Global IoT Connectivity to Create Mission Critical Use Cases for Enterprises — interview with Craig Price , PCCW Global
- Subex Explains its IoT Security Research Methods: From Malware & Coding Analysis to Distribution & Bad Actor Tracking — interview with Kiran Zachariah , Subex
- Mobile Security Leverage: MNOs to Tool up with Distributed Security Services for Globally-Connected, Mission Critical IoT — interview with Jimmy Jones , Positive Technologies
- TEOCO Brings Bottom Line Savings & Efficiency to Inter-Carrier Billing and Accounting with Machine Learning & Contract Scanning — interview with Jacob Howell , TEOCO
- PRISM Report on IPRN Trends 2020: An Analysis of the Destinations Fraudsters Use in IRSF & Wangiri Attacks — interview with Colin Yates , Yates Consulting
- Telecom Identity Fraud 2020: A 36-Expert Analyst Report on Subscription Fraud, Identity, KYC and Security — by Dan Baker , TRI
- Tackling Telecoms Subscription Fraud in a Digital World — interview with Mel Prescott & Andy Procter , FICO
- How an Energized Antifraud System with SLAs & Revenue Share is Powering Business Growth at Wholesaler iBASIS — interview with Malick Aissi , iBASIS
- Mobileum Tackles Subscription Fraud and ID Spoofing with Machine Learning that is Explainable — interview with Carlos Martins , Mobileum


