| © 2022 Black Swan Telecom Journal | • | protecting and growing a robust communications business | • a service of | |
| Email a colleague |
March 2019
Why SIM Box Bypass Fraud is a Growing Concern in A2P SMS, Especially on the Roaming Side

Most men live and satisfy their wants through their work, which creates value
for themselves, their family, or others. Now man is naturally inclined
to avoid pain — and working for a living causes certain hardships
and pain. It follows, then, that many men will resort to plunder whenever
plunder is easier than work.
Claude-Frédéric Bastiat (1801-1850) in The Law
Bastiat was a French economist and writer who lived at the dawn of the Industrial Revolution. His now-famous book, The Law, lays down the political argument for a Free Society and explains why Governments tend to invite fraud and corruption.
Interestingly, had Bastiat been born only a few decades later, he would have noticed how large industries (which didn‘t exist in his time) foster their own forms of corruption.
Looking at the international wholesale voice/SMS industry of today, we can see two classes of network provider: the established and the struggling.
An example of the established operators are the highly successful large wholesale providers (iBasis, BICS, Tata Communications) who have gained a strong market foothold. These companies are not just champions of industry laws, they pride themselves on maintaining their trusted, “fraud-free” ecosystems with hundreds of partner carriers.
The struggling operators, meanwhile, don‘t own a membership card to any of the big wholesaler clubs. So they need to make it on their own: many barely make enough money to say alive. Their margins are squeezed by the established firms, and they fear their “partners” may swindle them tomorrow.
So if your telecom firm is just surviving, it’s much easier to turn a blind eye to fraudsters offering some financial help. In short, many of the struggling will sell grey routes because they want to keep their firms afloat and pay their employees.
Now seeing this Darwinian battle in our industry, it’s hard to conceive of a day when telecom can eliminate fraud altogether. As long as young and inexperienced operators are struggling to break into the market, fraudsters will always find a natural ally.
Of course, as fraud fighters, our job is to tame the chaos because a telecom industry that lacks rules and doesn‘t fight plunder is an industry in trouble. Bernie Ebbers brought his plundering ways to WorldCom. Fortunately for us, Ebbers was caught and is now serving a 25-year prison sentence in Texas.
Speaking of fraud fighters, we’re pleased to again welcome Philippe Orsini, the Vice President of Product Development at Araxxe. In this interview, Philippe provides a backgrounder on A2P SMS fraud: both “classical” in-market SIM box bypass, as well as the more complex SMS fraud that exploits bypass via roaming scenarios.
| Dan Baker, Editor, Black Swan: Philippe, the A2P SMS is one of the revenue bright spots in the mobile industry. |
Philippe Orsini: It’s true, Dan, A2P SMS traffic is booming. And as you know, P2P SMS traffic is essentially free in many markets, but A2P has become a substantial revenue generator for operators.
How much money the operator makes depends on factors like the country, delivery quality, and message volume, but roughly speaking, to terminate an A2P message earns the operators 2 to 3 cents per SMS.
You have the brands — Google, Facebook, AirFrance, etc. — and then there are the operators who deliver messages to their mobile users. Also, carrying the messages from the brands to the operators are dozens of SMS providers or aggregators.
There are a couple well-known telecom firms in the SMS aggregator group, like Syniverse and Telcordia, but most of them, such as Infobip, MobileImpact, and OpenMarket are more specialized players.
| But fraudsters are in on the A2P game. What are the paths they find attractive? |
Yes, because A2P revenues are growing for operators, where money flows, fraud follows.
And several of the players in SMS are willing to operate grey routes to make more money and deliver brand messages at a lower cost.
We are starting to see practices like SMS-pushing or SMS-faking by the fraudsters.
SIM Boxes are very useful in SMS fraud because they allow the fraudsters to terminate their traffic via cheap P2P SMS. When you combine that with operators offering “Unlimited SMS” promotion plans, that’s a winning combination for the fraudster.
The classical case is an SMS is sent to customers and it goes through one or two SMS aggregators and a SIM box drops the traffic onto the terminating radio network.
So in a message between Google and O2 UK, for example, the SIM box has an O2 UK SIM card which terminates the message on the O2 UK network. This is a very common ploy and at Araxxe we’re seeing this simple method of termination more and more.
And the problem is even bigger now because there are many mobile rate plans that can hide the fraudster’s activities. For instance, in Europe, we have the “roam like you are at home” plans, which means the same rates apply when you’re outside of your home market.
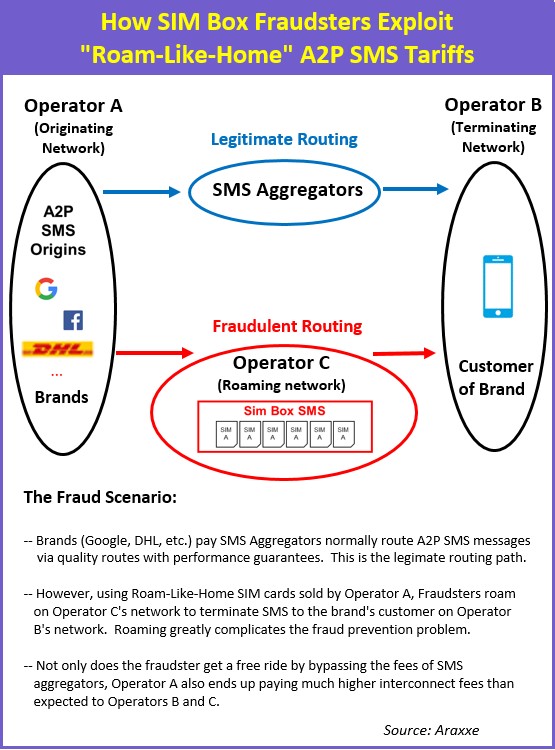
| How do fraudsters exploit Roam Like at Home? |
The problem is Roam Like at Home allows you to send an international SMS at a very low tariff.
Say for example, Google is sending a message to Orange Spain. Well the fraudster can insert an Telefonica Germany SIM card in a SIM box roaming anywhere in Europe and terminating traffic in Orange Spain.
Now, since the SIM card is not from the same country where the traffic terminates, it appears as if the SIM card is a German roamer sending SMS to Spain. But what’s really going on is the traffic is terminating via cheap grey routes and bypassing the expensive A2P SMS rates going direct to the mobile operator.
On top of that, in our previous example, if the same Telefonica Germany SIM cards can be used to terminate in countries like Italy or Belgium, you not only have a SIM box bypass problem, you’re also artificially inflating your interconnect costs.
In this case, the operator owner of the SIM cards in the SIM boxes has a big problem because their SIM cards are being extensively used in a roaming situation by fraudsters.
From a retail revenue perspective, there’s no bad impact because the plan allows for unlimited SMS in Europe. However, on the interconnect cost side, the operator is going to pay a lot for that traffic in terms of inter-operator traffic through roaming and termination.
Basically you have low revenue retail subscribers generating high interconnect costs.
| I see, so the fraudsters are taking advantage of roaming. |
They are. The fraudsters love to run their schemes through roaming because it’s harder to detect this fraud.
Now, for incoming traffic, most operators employ an SMS firewall to filter incoming traffic from fraudulent and grey traffic. Trouble is, even with an SMS firewall in place, they cannot stop incoming traffic via roaming: it’s just not in the SMS firewall’s capabilities.
So these new fraud scenarios mean the operator must explore different approaches to problems. It’s very complex.
| So how does Araxxe help operators combat SMS fraud? |
Well, basically in two ways.
First, the classical Sim Box SMS scenario. For example, we help an operator by generating test A2P SMS traffic toward its network from Google, Facebook, and other brands to check the A2P termination and see if we detect SIM box bypass. When it comes to testing roaming scenarios, that calls for a full-blown international campaign which is quite tricky.
Let’s suppose Operator A wants to know whether Operator A cards are being used to terminate traffic in a particular destination. Well, once again, we generate SMSs from Google, Facebook, etc. and A2P origin towards many networks in Europe or even worldwide. Then we compare the results. Do we see any Operator A SIM cards transforming to P-SMS towards Russia, Canada, Germany, Mexico etc.?
If the answer is no, that’s good news for Operator A. And if we see even one transformation to P-SMS landing, say, in Orange Spain, that’s very valuable information.
It’s very hard to detect, but this is our contribution to SMS fraud control. We first send the traffic to many nations with our robots, then we analyze the results using SIM cards from many operators who are clients of Araxxe.
Along the way, if we detect problems for other operators who are not clients, it’s useful to warn those operators, too.
| Great, Philippe. It’s easy to see how Araxxe’s expertise in fighting SIM box bypass in voice traffic is helping it on the A2P SMS side. |
Copyright 2019 Black Swan Telecom Journal
Black Swan Solution Guides & Papers
- Expanding the Scope of Revenue Assurance Beyond Switch-to-Bill’s Vision — Araxxe — How Araxxe’s end-to-end revenue assurance complements switch-to-bill RA through telescope RA (external and partner data) and microscope RA (high-definition analysis of complex services like bundling and digital services).
- Lanck Telecom FMS: Voice Fraud Management as a Network Service on Demand — Lanck Telecom — A Guide to a new and unique on-demand network service enabling fraud-risky international voice traffic to be monitored (and either alerted or blocked) as that traffic is routed through a wholesaler on its way to its final destinations.
- SHAKEN / STIR Calling Number Verification & Fraud Alerting — iconectiv — SHAKEN/STIR is the telecom industry’s first step toward reviving trust in business telephony — and has recently launched in the U.S. market. This Solution Guide features commentary from technology leaders at iconetiv, a firm heavily involved in the development of SHAKEN.
- Getting Accurate, Up-to-the-Minute Phone Number Porting History & Carrier-of-Record Data to Verify Identity & Mitigate Account Takeovers — iconectiv — Learn about a recently approved risk intelligence service to receive authoritative and real-time notices of numbers being ported and changes to the carrier-of-record for specific telephone numbers.
- The Value of an Authoritative Database of Global Telephone Numbers — iconectiv — Learn about an authoritative database of allocated numbers and special number ranges in every country of the world. The expert explains how this database adds value to any FMS or fraud analyst team.
- The IPRN Database and its Use in IRSF & Wangiri Fraud Control — Yates Fraud Consulting — The IPRN Database is a powerful new tool for helping control IRSF and Wangiri frauds. The pioneer of the category explains the value and use of the IPRN Database in this 14-page Black Swan Solution Guide.
- A Real-Time Cloud Service to Protect the Enterprise PBX from IRSF Fraud — Oculeus — Learn how a new cloud-based solution developed by Oculeus, any enterprise can protect its PBX from IRSF fraud for as little as $5 a month.
- How Regulators can Lead the Fight Against International Bypass Fraud — LATRO Services — As a regulator in a country infected by SIM box fraud, what can you do to improve the situation? A white paper explains the steps you can and should you take — at the national government level — to better protect your country’s tax revenue, quality of communications, and national infrastructure.
- Telecom Identity Fraud 2020: A 36-Expert Analysis Report from TRI — TRI — TRI releases a new research report on telecom identity fraud and security. Black Swan readers can download a free Executive Summary of the Report.
- The 2021 State of Communications-Related Fraud, Identity Theft & Consumer Protection in the USA — iconectiv — This 49-page free Report on communications-related fraud analyzes the FTC’s annual Sentinel consumer fraud statistics and provides a sweeping view of trends and problem areas. It also gives a cross-industry view of the practices and systems that enable fraud control, identity verification, and security in our “zero trust” digital world.
Recent Stories
- Epsilon’s Infiny NaaS Platform Brings Global Connection, Agility & Fast Provision for IoT, Clouds & Enterprises in Southeast Asia, China & Beyond — interview with Warren Aw , Epsilon
- PCCW Global: On Leveraging Global IoT Connectivity to Create Mission Critical Use Cases for Enterprises — interview with Craig Price , PCCW Global
- Subex Explains its IoT Security Research Methods: From Malware & Coding Analysis to Distribution & Bad Actor Tracking — interview with Kiran Zachariah , Subex
- Mobile Security Leverage: MNOs to Tool up with Distributed Security Services for Globally-Connected, Mission Critical IoT — interview with Jimmy Jones , Positive Technologies
- TEOCO Brings Bottom Line Savings & Efficiency to Inter-Carrier Billing and Accounting with Machine Learning & Contract Scanning — interview with Jacob Howell , TEOCO
- PRISM Report on IPRN Trends 2020: An Analysis of the Destinations Fraudsters Use in IRSF & Wangiri Attacks — interview with Colin Yates , Yates Consulting
- Telecom Identity Fraud 2020: A 36-Expert Analyst Report on Subscription Fraud, Identity, KYC and Security — by Dan Baker , TRI
- Tackling Telecoms Subscription Fraud in a Digital World — interview with Mel Prescott & Andy Procter , FICO
- How an Energized Antifraud System with SLAs & Revenue Share is Powering Business Growth at Wholesaler iBASIS — interview with Malick Aissi , iBASIS
- Mobileum Tackles Subscription Fraud and ID Spoofing with Machine Learning that is Explainable — interview with Carlos Martins , Mobileum


