| © 2022 Black Swan Telecom Journal | • | protecting and growing a robust communications business | • a service of | |
| Email a colleague |
October 2019
In the Era of Telecom Security Breaches, Mobileum Brings Signaling’s Deep Detection Capability to the Fraud Fight

The biggest recent news in the telecom fraud and business assurance market is that Mobileum acquired WeDo Technologies, who owns the largest global base of telecom fraud control and RA platform customers.
I recently attended the first conference held by the combined company at the swanky Fontainebleau hotel on Miami Beach. About 130 people attended including delegates from 30 CSPs.
As the conference panels and presentations reinforced, the top issue driving the merger of these two firms is fraud and security control.
In recent years, Mobileum has made its mark pioneering the use of signaling, analytics, and machine learning technologies to improve fraud detection and blocking, especially in mobile roaming where fraudsters like to hide and commit their frauds. In fact, several reference customers are pleased with the results Mobileum achieved for them, especially a Tier 1 mobile operator in the US.
But WeDo also brings great capabilities to the table. In addition to its rich customer base, WeDo has also assembled a top flight consulting team led by experts like Thomas Steagall (formerly Ericsson) and Jim Bolzenius (former head of fraud control at Verizon).
Certainly the merger of Mobileum and WeDo brings tomorrow’s fraud challenges into sharp focus. For example, how will telecom manage the transition from traditional CDR-based detection of ISRF/Wangiri fraud to greater integration with advanced technologies like signaling and machine learning — Mobileum’s strong suit?
Fortunately I spoke in Miami to Miguel Carrero, General Manager of Mobileum’s Security Business Unit (working out of Cupertino, CA) — and he's been focused on telecom security for years.
In the interview that follows, Miguel makes a great case for why an increase in security-breach-driven fraud is to be feared. And through five fraud scenarios — from IRSF to Account Takeover fraud — he explains how Mobileum brings its advanced technology to bear on these problems.
| Dan Baker, Editor, Black Swan Telecom Journal: Miguel, why is there greater interest in telecom security and signaling in recent years? Have the bad actors suddenly become successful at blowing holes in telecom’s firewall? |
Miguel Carrero: Ironically, Dan, telecom networks are not fully secure by design! Now what do I mean by that?
Well, telecom has always relied on trusted relationship between a few operators and ecosystem players, so the security of the signaling network was always built on that trust.
But in 2015 people were shocked to learn that bad actors were intercepting network content and routing traffic by manipulating signaling.
Likewise in 2017, there was a widely publicized fraud in Germany where network was penetrated via signaling to redirect two-factor authentication to a fraudster’s device. And this enabled the fraudsters to take over bank accounts and empty them of their money.
Bottom line, a lot of signaling technologies in place are quite vulnerable. Even SS7, the grandfather of signaling protocols, can be exploited because the bad actors are so familiar with it now.
| How is it that these bad actor and fraudsters have penetrated and learned how to use signaling tools? |
I think it’s a combination of factors. First of all, in the last decade, many new telecom and service providers entered the telecom business, so you have a new generation of wholesalers, SMS aggregators, brokers, and others so the ecosystem is way broader in the number and nature of players.
Further complicating the problem, we have a variety of signaling technologies to connect to: SS7, DIAMETER, SIP, CAMEL, and GTP. So that adds complexity and thus new threats.
Another big threat comes from low-cost barrier of entrance telecom hardware, software, and services available on a commercial basis. See the chart below:
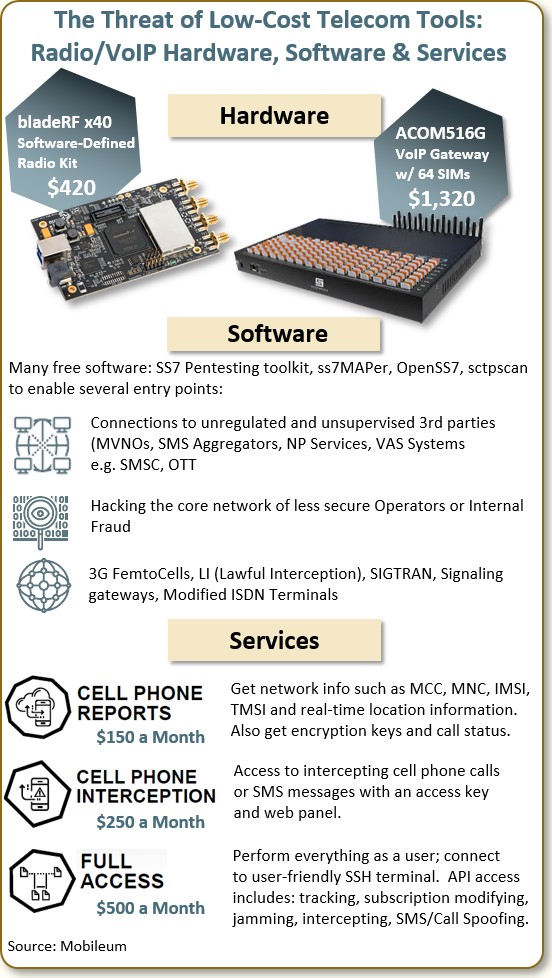
The prices of these tools make it very easy for someone with programming or hacking skills to play around with telecom networks and services.
For example, for only $1,320 you can buy a VoIP gateway with a bank of 64 SIM slots. For a mere $420 you can buy a toolkit to do SS7 penetration testing.
Also available are free and open source signaling analysis software, such as ss7MAPer and OpenSS7. Some of the tools would allow someone to hack into the core network of a less-secure operator, perhaps with the help of an internal fraudster.
To make things even easier, there are actually services you can buy on a monthly basis:
- A Cell Phone Report service provides IDs and other details on active cell phones including equipment location information: it’s only $150 a month.
- Would you like to intercept cellular calls or SMS messages? Sign on for only $250 a month to an Interception Service.
- Want to learn how to modify a subscription or spoof an SMS or mobile call? A Full Access Service enabling that can be had for only $500 a month.
Combine all these elements and they create a perfect storm bearing down on telecom industry security. We are even seeing an increased level of specialization and collaboration among bad actors.
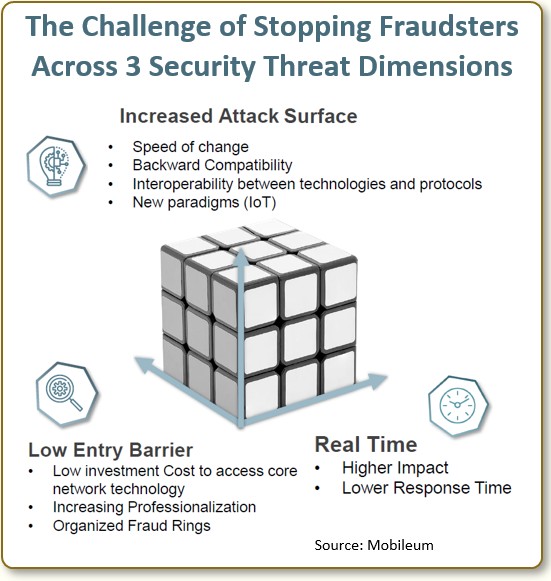
We can think of the telecom security threat as coming from three threat dimensions as shown in the chart below:
| So how can telecom operator respond to these new threats at the core of a telecom network’s security? |
Perhaps the first thing to recognize is we need to think more outside the box — and develop new methods of detection.
In the past, fraud followed well-worn paths and easier-to-recognize patterns. Today, fraudsters employ counter-measures to exploit operator weaknesses. That's why frauds are increasingly enabled by a security breach.
When you add up the wildcards of: 1) increased fraudster sophistication; 2) the growth of social engineering as a way to capture identities; and 3) the pressure of insider fraud — it’s clear that fraud detection, prevention and blocking solutions must become far more adaptive.
Increasingly, network security combines three steps:
- Block the “known” by writing flexible and sophisticated firewall rules that identify subtle attacks (including those that exploit cross protocol activity);
- Detect the “unknown” through security analytics (evolving into ML and AI) to detect anomalies that will lead to better firewalling of your network; and,
- Set the policy rules to block the anomalies you identify as malicious behavior. This will, in turn, stop the potential fraud associated with the attack.
| Today, CDR analysis is the most widely adopted means of analyzing IRSF and Wangiri frauds. And it’s the main technology WeDo, operators, and other solution firms use to curb those frauds. So what does signaling add to the fraud defense? |
Yes, CDR analysis is a very powerful tool in fraud detection. The trouble is, as fraudsters constantly seek to avoid detection, they favor hiding their fraud in complex scenarios such as roaming.
They know in roaming there are significant delays before the home operator gets back its call records. The GSMA standard is 4 hours for NRTRDE and 36 hours for TAP files.
CDRs are important, but don’t give you the full context, since they cannot monitor a call in progress because the record doesn’t get cut till the call ends. Additionally CDRs fall short on monitoring calls attempted, but there’s valuable intelligence to be gained by examining calls attempts and other elements of mobility management.
So overcoming these CDR limitations is where signaling comes into play. Not only does signaling enable real-time detection and blocking, it also allows you to understand the complete context — before and during the call:
- What’s the geographic location?
- What was the originating country of the call? and,
- What can we learn from the things signaling sees: call attempts, dialed digits and various service flags?
Signaling is also a powerful in the SMS domain. When the user sends 200 SMS messages in a minute, it’s clear you’re looking at a robot, not a human being.
| It would be great if you could go through a few Mobileum case studies to illustrate how signaling adds value. |
OK, let’s do that. Let me walk you through highlights of five fraud cases: IRSF, Wangiri, Data Roaming Fraud, SMS Bypass, and Account Takeovers.
1. International Revenue Share Fraud (IRSF)
IRSF is committed by organized groups using illegal connections — such as PBX hijacking and mobile phone traffic pumping — with the aim to place a large volume of calls to premium numbers. And fraudsters very often take advantage of the roaming capabilities of SIM cards to commit this fraud because it allows them to modify headers or exploit billing delays.
The difference with Mobileum is our signaling intelligence gives us a better look when the fraudster roams. Here are some of the steps we can accomplish:
- Detect roaming attachments — Every time a subscriber roams, we receive a CAMEL event that tells us what country they are roaming to.
- Monitor Roaming Usage — Next we can look at the story of this customer and determine, “Is this his first call?” or “Did he ever call from this country?” In this way we can understand the context of the caller’s scenario and immediately block the customer if the usage is suspect.
- Profile the User — We can also access the user’s historical profile of calls so we can learn about calling patterns and the cell IDs he’s using. In fact, as soon as the user inserts a SIM card into a device we can detect that new cell ID is on the network.
2. Wangiri Fraud
Wangiri is a simple, but very effective premium rate attack. As a way to start a Wangiri attack, a robo dialer generates calls to someone from a premium number and immediately hangs up the call, creating a bogus “missed call”
The idea is to get the user to call-back to the premium number where a recorded message entices the caller to stay connected on the call as the fraudster runs up its fraudulent high-rate charges.
Mobileum’s signaling capability once again is useful to:
- Track call attempts — In signaling we see a single premium number is trying to get in touch with multiple customers of the operator. This gives us a real-time way to identify suspicious numbers.
- Targeted blocking — Using our Active Intelligence capability, once we suspect a malicious outbound call or inbound call, we can block it in the network.

3. Data Fraud via Roaming
When fraudsters buy SIM cards, they tend to avoid buying them at a store. A safer approach for them is to buy their SIM cards on a portal using compromised credentials.
In this particular case, the SIM cards in SIM boxes in, say, various countries of Africa, are not used to make phone calls, but to stream data illegally to High Risk Countries via roaming.
When a high number of SIMs are compromised in this way, they create high roaming costs to the Home Operator.
Here’s a quick overview of Mobileum’s solution to this data fraud problem.
- Track SIM card purchases — Whenever the fraudster tries to buy SIM cards, we have ways of figuring out the physical movement of SIM cards. The typical scenario is for the fraudster to buy the SIM cards and then change the address to get the SIM cards to a specific place.
- Monitor the Customer Care Portal — We also closely monitor the volume of requests coming from the same ID and suspicious web traffic on the Customer Care Portal, such as address changes after purchase.
- Prevent SIM card from roaming — Beause our customer portal checks are integrated with CAMEL, we can not only implement a block on requests to High Risk Countries, we also prevent the particular SIM Card from being allowed to roam.
4. SMS Bypass
International brands like Facebook, Uber, airline companies, and many others pay $14 billion (2017) to mobile operators to ensure that their A2P messages are delivered to their customers in a timely, reliable, and high quality manner.
Fraudsters in the SMS aggregator chain illegally send these A2P messages over free P2P networks (“grey routes”), pocketing the savings and defrauding the telco.
Indeed, analyst firm MobileSquared, who follows the messaging industry estimates A2P revenue leaks over so-called Grey Network Routing were a whopping $7.7 billion in 2017.
To curb the problem, Mobileum looks at a variety of factors in the messages (both the variety and velocity of those and certain elements of the content) to determine if those are A2P messages being attempted in a grey route.

5. Account Takeover via SMS Hijack
Another consequence of a fraudster penetrating your network and establishing its own SMS center (SMSC) is breaking the connection between the operator and the mobile user.
With a direct connection to the mobile user, the fraudster can capture sensitive information from the mobile user such as key IDs. Pretty soon, as the fraudster receives SMS for that mobile user, the fraudster can reset passwords and fully take over email and bank accounts.
- Detect network element spoofing — Mobileum’s signaling strength allows us to identify the spoofing network elements in voice and the SMS. Whenever we suspect a network element has been compromised, we can challenge the network element to respond to us and authenticate.
- Examine the message texts — We can also do consistency checks — look inside the message where we often find that mandatory fields are omitted or the message contains wrong information.
- Do an element validity check — Is the element even active in our own network? A validity check will detect, say, when an SMSC is being spoofed.
- Check the country location of the element — If the subscriber is attached to an SMSC in the UK, it’s often the case that a fraudulent SMSC is located in another country, often the US. So this is another way we can tell the SMSC is spoofed.
| Great, these nice examples highlight where signaling adds new capabilities in fraud detection. But your cases also points to the urgency of protecting the telecom network at a higher level. |
Yes, there’s an urgent need to develop a system for guaranteeing security of the signaling side of telecom, and avoid further compromise from a fraud perspective.

We know telecom network will remain a multi-vendor domain that communicates across many different protocols involved. Still, it’s important that a consolidated platform be implemented to understand:
- What is my current security posture right now?
- Is that consistent and in accordance with my risk tolerance?
- What is my expected evolution and thought process into the future?
The issue is much more than understanding the protocols. You also need to sort out inconsistencies in the way DIAMETER or CAMEL or SIP is implemented at specific carriers.
Moreover, designing or architecting security across the telecom network is a tremendous challenge because it needs to work across multiple generations of network technology, a variety of signaling protocols, and thousands of network providers.
The irony, of course, is that if you completely nailed down the network with positive and negative rules, you would stifle innovation, because security doesn’t allow much wiggle room and there are unexpected network behaviors that are not malicious.
So the telecom network should be an organic ecosystem that adapts to market change and new technologies coming into the business. In short, a good balance between innovation-enabling openness and proper protection is required.
| Can network equipment providers (NEPs) play a role in developing an overarching system to reconcile multipole signaling systems? |
They can. The problem is that telecom is inherently multi-vendor, whereas the NEPs have a vested interest in their own approach.
In telecom system design you need to be agnostic to many different flavors — so you can communicate with many different telecom equipment providers. But since they own network equipment themselves, bias enters the picture. They want to sell you a piece of equipment that works especially well with their own family of network elements.
Mobileum, on the other hand, being an independent solution provider has the network and signaling expertise to build the higher-level security systems needed for the future.
|
Thanks for these deep insights, Miguel. There's a lot technical details to master
on the path to delivering security-aware fraud control. But you've laid out here a fine analysis
of where signaling fits into the telecom fraud picture.
Good luck with marketing such solutions, and congratulations on the merger of Mobileum and WeDo. |
Copyright 2019 Black Swan Telecom Journal
Black Swan Solution Guides & Papers
- Expanding the Scope of Revenue Assurance Beyond Switch-to-Bill’s Vision — Araxxe — How Araxxe’s end-to-end revenue assurance complements switch-to-bill RA through telescope RA (external and partner data) and microscope RA (high-definition analysis of complex services like bundling and digital services).
- Lanck Telecom FMS: Voice Fraud Management as a Network Service on Demand — Lanck Telecom — A Guide to a new and unique on-demand network service enabling fraud-risky international voice traffic to be monitored (and either alerted or blocked) as that traffic is routed through a wholesaler on its way to its final destinations.
- SHAKEN / STIR Calling Number Verification & Fraud Alerting — iconectiv — SHAKEN/STIR is the telecom industry’s first step toward reviving trust in business telephony — and has recently launched in the U.S. market. This Solution Guide features commentary from technology leaders at iconetiv, a firm heavily involved in the development of SHAKEN.
- Getting Accurate, Up-to-the-Minute Phone Number Porting History & Carrier-of-Record Data to Verify Identity & Mitigate Account Takeovers — iconectiv — Learn about a recently approved risk intelligence service to receive authoritative and real-time notices of numbers being ported and changes to the carrier-of-record for specific telephone numbers.
- The Value of an Authoritative Database of Global Telephone Numbers — iconectiv — Learn about an authoritative database of allocated numbers and special number ranges in every country of the world. The expert explains how this database adds value to any FMS or fraud analyst team.
- The IPRN Database and its Use in IRSF & Wangiri Fraud Control — Yates Fraud Consulting — The IPRN Database is a powerful new tool for helping control IRSF and Wangiri frauds. The pioneer of the category explains the value and use of the IPRN Database in this 14-page Black Swan Solution Guide.
- A Real-Time Cloud Service to Protect the Enterprise PBX from IRSF Fraud — Oculeus — Learn how a new cloud-based solution developed by Oculeus, any enterprise can protect its PBX from IRSF fraud for as little as $5 a month.
- How Regulators can Lead the Fight Against International Bypass Fraud — LATRO Services — As a regulator in a country infected by SIM box fraud, what can you do to improve the situation? A white paper explains the steps you can and should you take — at the national government level — to better protect your country’s tax revenue, quality of communications, and national infrastructure.
- Telecom Identity Fraud 2020: A 36-Expert Analysis Report from TRI — TRI — TRI releases a new research report on telecom identity fraud and security. Black Swan readers can download a free Executive Summary of the Report.
- The 2021 State of Communications-Related Fraud, Identity Theft & Consumer Protection in the USA — iconectiv — This 49-page free Report on communications-related fraud analyzes the FTC’s annual Sentinel consumer fraud statistics and provides a sweeping view of trends and problem areas. It also gives a cross-industry view of the practices and systems that enable fraud control, identity verification, and security in our “zero trust” digital world.
Recent Stories
- Epsilon’s Infiny NaaS Platform Brings Global Connection, Agility & Fast Provision for IoT, Clouds & Enterprises in Southeast Asia, China & Beyond — interview with Warren Aw , Epsilon
- PCCW Global: On Leveraging Global IoT Connectivity to Create Mission Critical Use Cases for Enterprises — interview with Craig Price , PCCW Global
- Subex Explains its IoT Security Research Methods: From Malware & Coding Analysis to Distribution & Bad Actor Tracking — interview with Kiran Zachariah , Subex
- Mobile Security Leverage: MNOs to Tool up with Distributed Security Services for Globally-Connected, Mission Critical IoT — interview with Jimmy Jones , Positive Technologies
- TEOCO Brings Bottom Line Savings & Efficiency to Inter-Carrier Billing and Accounting with Machine Learning & Contract Scanning — interview with Jacob Howell , TEOCO
- PRISM Report on IPRN Trends 2020: An Analysis of the Destinations Fraudsters Use in IRSF & Wangiri Attacks — interview with Colin Yates , Yates Consulting
- Telecom Identity Fraud 2020: A 36-Expert Analyst Report on Subscription Fraud, Identity, KYC and Security — by Dan Baker , TRI
- Tackling Telecoms Subscription Fraud in a Digital World — interview with Mel Prescott & Andy Procter , FICO
- How an Energized Antifraud System with SLAs & Revenue Share is Powering Business Growth at Wholesaler iBASIS — interview with Malick Aissi , iBASIS
- Mobileum Tackles Subscription Fraud and ID Spoofing with Machine Learning that is Explainable — interview with Carlos Martins , Mobileum

