| © 2022 Black Swan Telecom Journal | • | protecting and growing a robust communications business | • a service of | |
| Email a colleague |
September 2020
Positive Technologies: White Hat Hacking & Testing are Key to Signaling Security in the Era of 5G and IoT

We tend to think the challenges of telecom signaling security and fraud control are unique problems.
But as I sat here writing this story, I got a message from Microsoft saying it was time to reboot my computer to install a new OS update and security patches for Windows.
Security is a mammoth yearly investment for Microsoft. I found a 2017 story that claims the company spends $1 billion a year and has 3,500 employees dedicated to cybersecurity.
The parallels between telecom signaling and Windows security issues are several:
- Backward compatibility to legacy — Both Windows and telecom signaling
are committed to moving customers from legacy to modern, more-capable solutions
with a minimal loss of security and trouble.
- Both use two-layer architectures — For telecom, all services
(voice, SMS, data) are enabled by a separate layer of signaling protocols.
On a PC, the software applications work by sending commands to the Windows OS.
- Regular security updates are absolutely essential. Windows has
been around for decades, yet maintenance reboots are constant. Likewise,
big changes have occurred in signaling protocols, and all these changes require
continual testing, configuration changes, and updates.
- Huge bases of users to protect — The massive reach of the Windows user base is an inviting target for criminal hackers. And with the fast rise of smartphones, signaling and other telecom security may
be an even bigger magnet for hackers and fraudsters, in part because smartphones
are used as personal devices.
So what can we surmise about tomorrow’s signaling challenges? Well, we can safely say: bumpy roads are ahead because telecom is moving to far more complex ecosystems with IoT and 5G — even as legacy networks also require constant attention.
Lots of “white hat” hacker investments will be required to stay ahead of the black hats. And since signaling is the operating system of telecom, a huge amount of testing, probing, configuration fixing, and operator security commitment is needed.
To help sort out the tremendous signaling issues ahead, I once again interviewed Jimmy Jones — Telecom Business Development Lead at Positive Technologies — an expert at explaining signaling security to the layman.
| Dan Baker, Editor, Black Swan Telecom Journal: Jimmy, how would you compare industry awareness of signaling security today versus that of 5 to 10 years ago? |
Jimmy Jones: Telecoms are certainly treating signaling security trends more seriously these days, Dan.
In the past, lots of problems were treated as strictly IP problems whereas the legacy signaling protocols were more isolated and more locked down. So the attitude back then was: “As long as I keep the IP door shut, we’ll be safe”.
But the reality of today is much different. Now, there’s a greater consolidation of signaling technologies, meaning every corner of the network is now open to compromise: SS7 migrated after over three decades from its wired point-to-point circuits to IP networks. This introduced it to threats it was never designed for and it’s a similar story for other telecom protocols, too.
SS7 Protocol
SS7 is the protocol that has seen the most security investment. But now that the fraudsters have noticed telcos are taking greater security care of SS7, they’ve started raising their game by employing more bypass techniques.
And SS7 is really the first protocol in mobile networks where we’ve seen hackers move to more sophisticated bypass practices.
Now the IMSI identifier is your ID on the network and that’s the one thing the mobile operators really try to lock down as it’s the key to preventing more complex attacks such as call and SMS interception. And yet, our white hat hackers at Positive captured that identifier at 93% of the operators we tested. We were able to achieve this by bypassing three-quarters of the firewalls present in the testing.
What’s more, about half of the operators we tested use SMS home routing platforms which are specifically designed to protect the IMSI. But even there, we could penetrate nearly 60% of those telcos.
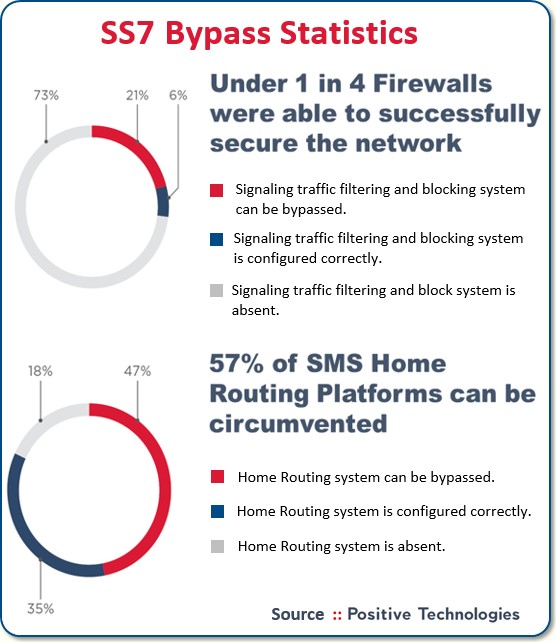
NOTE: Positive Technologies has published a detailed 2020 Report, SS7 Network Security Analysis Report, which you may download.
Diameter Protocol
Like SS7, Diameter is also vulnerable. Positive was able to gain access to the IMSI through Diameter at 90% of the operators we tested, meaning the fraudsters can potentially track a subscriber’s location continuously.
GTP (GPRS Tunneling Protocol)

GTP is a protocol that’s been around since the days of 2G and 3G. Anytime you access the internet from your phone, you’re using GTP.
Unfortunately, the vulnerabilities in GTP are similar to those of SS7 and Diameter. And we can expect GTP to be with us for a long while yet. Only when we move to “5G Standalone” architecture will the internet access threat of GTP compromise be reduced. So you’re probably talking 5 to 6 years.
NOTE: Positive has just published a detail analysis report on GTP Protocol Security which you may download.
| What are some of the specific security issues around the GTP protocol? |
Dan, let me review some of the biggest security issues with GTP:
- Verifying the User’s Location — The first problem with GTP
is you can send a GTP message to your home network from anywhere. So,
to know if it’s real or not, you must understand if that subscriber can
logically be located where he says he is.
And to do that, you need to know where he’s been and how quickly he can get somewhere. For instance, if the user is in London mid-day, there’s no way he can be in New York by 1:00 PM.
In short, you need to access dynamic tables which are not easy to work with. And you can’t determine geo-location directly from GTP. You have to use Diameter or SS7 to do that, so the need for multiple protocols complicates things.
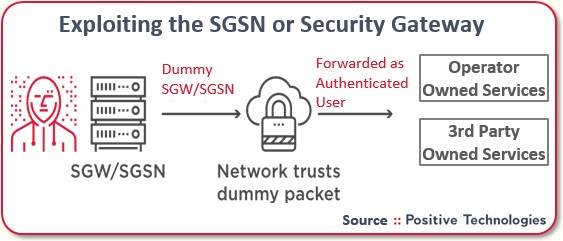
- Exploiting the SGSN or Security Gateway — An even bigger problem
with GTP is the security gateway or SGSN, a device that authenticates that the
user has a valid SIM, and is allowed to use GTP and related services.
The telco really wants to understand: is this guy one of my customers? Has he got one of my IMSIs or identifiers? Unfortunately, our security audit discovered this check is often not being done.
The problem is that you can send messages on the network that look like they come from the SGSN so are already pre-authorized.
The basic attack is to use the internet by hijacking access with a real or fake IMSI identifier. This allows the fraudster to commit subscription fraud, accessing the internet, to either defraud the subscriber if using a real IMSI, or defraud the operator in the case of non-existent or fake IMSI identifiers. On 63% of the networks we tested, we could just use non-existent (fake) identifiers.
By accessing the internet in this way, the hackers can also potentially cover their tracks when attacking other sites or companies. When these breaches are investigated, the originator of the attack will appear to be the unfortunate subscriber, or just a general pool of operator IP’s. Either way, it reflects badly.
- Self-Service Portal Breaches — Using the same technique, hackers
can affect self-service portals. Some mobile operators have self-service
portals where the user logs into them through their phone. Since it recognizes your SIM device, it doesn’t ask you to use
any passwords as the user accesses details on their account. This security hole could
release personal data, giving rise to potential GDPR, CCPA or other data privacy
fines.
Take that case one step further. Imagine a scenario where it’s not the operator’s self-service portal, but the portal of someone who is partnered with the operator.
In that case, a breach could be much more serious. It could lead to identity theft on a more important platform, and then it’s hard to quantify the damage the identity theft could cause.
All this is very possible since — when using GTP — there’s a connectivity hub that connects all the mobile operators. It’s like an IP exchange, but predates them so it retains its old GRX acronym.
Hackers want to get on the hub to attack. And it’s not difficult. What a hacker often does is attack, let’s say, a small operator on an island somewhere. Then once they gain access from there to the hub, they can send messages to the larger operators.
| How do the hackers exploit signaling to enable identity theft and bank account penetration? |
Well, if they can successfully hack the signaling network, they can exploit it a number of ways. And the entry point that’s compromised doesn’t have to be your bank account. It could be your Facebook account or another of a multitude of platforms and services.
I could send an SMS or make a call and pretend to be your bank by presenting a fake calling number that you expect. An individual suspicious of this interaction may insist on calling the bank back if my attempt to phish the data I want is not convincing. However, I can, in some instances, hijack the network call routing and redirect the calls to me — now I am spoofing your bank after you have originated the call. This is much more convincing. Or maybe I could spoof being the government — the options are almost endless.
What can be achieved is less important than how we arrive at a protection mechanism.
In another real situation in Latin America, a subscriber had his profile on the mobile network changed remotely by a hacker to say that it used a different GGSN for his mobile data. A GGSN is basically the gateway device from the operator to the internet.
And when you go look at the mobile website — no matter what you’re looking at — that actual packet goes through a data network. But if they change it so the first hop is one of their devices: that means they were intercepting all of the user’s internet traffic.
So if he visits his bank online, they could see that. And the fraudster can simply spoof the web page of Bank of America, or whoever, for the next time the customer comes through. And the fraudster will capture all the details.
So I think you see: a security breach is far more dangerous because the criminals can use it to accomplish multiple types of fraud. Addressing security also addresses the fraud opportunity, so is very effective.
| What do you feel the impact of signaling security will be on IoT’s future? |
With IoT, security priorities change. For instance, when you and I talk via my phone, what’s important is the network protects the security of our conversation. Privacy is paramount. If we experience denial of service and the call drops, and I have to ring back, I’m probably not that worried, I will think you just lost coverage going through a tunnel or something.
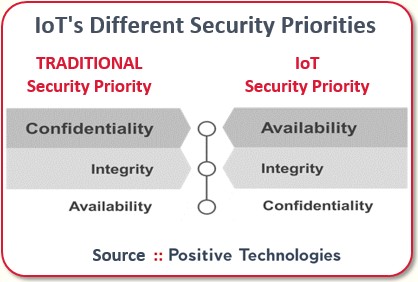
But in many IoT scenarios, greater connectivity security is needed. Say I’m operating an industrial IoT that passes data from a temperature gauge on a major petroleum pipeline. If the reliability of that network is compromised, the IoT could fail to send a critical high-temperature alert and create a big safety issue.
Denial of Service (DoS) attacks are probably the most significant risk in IoT. We found potential DoS vulnerabilities on every GTP network we tested.
| Now in security, I recognize there’s a lot of cross-over between IoT and 5G, but 5G will certainly drive the need to secure high bandwidth performance and big data delivery systems. |
Primarily, Dan, 5G exists to allow IoT. Operators are managing 5G by building networks “slices” where each slice supports the different connectivity needs of different IoT services. This increases complexity as you’re essentially supporting 3 or 4 networks instead of 1. This multiplies your security issues and also introduces the problem of protecting one slice from “infecting” other slices.
Clearly one of the biggest challenges is securing the virtualization of the underlying 5G network. 5G needs virtualization scalable and agile enough to deliver the services it promises and NFV virtualization is currently being used. Think of NFV as essentially a highly regulated private cloud that security people need to constantly monitor. Even as they do so, it is morphing into Cloud Native infrastructure, hybrid public-private clouds, and expanding out of the core network to the edge, so on its own it’s an unenviable task!

The key issue is that telcos need to commit to security and not compromise their standards or let their guard down as they move to these ever more complex and fast developing 5G and IoT environments where lots more partners and third parties are involved.
The temptation to compromise security will be very real. For instance, someone on the business side will come along and say, “I’ve got a massive IoT opportunity we should take advantage of”. And so there’s pressure to divert budget dollars over to the new opportunity and also accelerate development for first mover business advantage, so the company may not be investing enough in security.
But smart operators will recognize, even as you open up the network to take advantage of opportunities, if you allow security to be compromised, you’re asking for trouble given all the devices, network slices, partners, and traffic volumes involved.
The opening up of the network is pivotal but must be secure. API use is growing in all areas and all levels of the network. Creating vendor neutrality, speeding up innovation and opening up the network to outside third parties and allowing IoT are just some use cases. Gartner states that by 2022, APIs will be the most frequent attack vector, so it’s crucial to secure them to protect the network and the new IoT infrastructure it supports.
For instance, all the IoT devices need to be connected to a management platform that is hosted directly or indirectly by the mobile operator. You also need to be super careful about your supply chain because you’re connecting to other organizations who are putting their service and equipment on the network.
And all those IP network security concerns that large enterprises worry about are now coming more and more into the telecom world.
A recent report from IDC says that by 2025 IoT is going to drive 42 billion devices and 75 Zettabytes of data. These are huge numbers. And they suggest that security must become as agile as the network business itself.

| Given all the complexity, would it make sense for operators to tackle one or two IoT/5G sectors really well, and leave the rest to others? |
Well, there might be an option where a mobile operator looks after the automobile or the health sector but their business will inevitably need to expand.
I believe the real consideration is not so much the number of sectors but that the mobile operators need to build more and more value to avoid becoming a dumb 5G pipe. Telcos remember the business Skype and WhatsApp took away from them.
And unless the telcos make the good profit margins that “full wrap” services enable, then they might not have the money to build truly secure networks to the scale 5G needs in the first place: their business model must give them the capital to allow them to grow to support the network expansion. Otherwise, you could see them taken over by a tech behemoth.
Regardless, the next-gen security challenge is pretty daunting. What you’re doing is managing multiple networks, with diverse conditions, running on new virtual infrastructure, moving to a more open environment and service-based architecture, all while integrating more and more partners and still supporting legacy networks. The complexity will grow exponentially.
Complexity is security’s enemy. Regardless of the industry, about a third of the problems we find and help address are configuration errors.
| Thanks again, Jimmy, for taking us down in the weeds of signaling security and helping us make sense of the issues. |
My pleasure, Dan. The good news for 5G is there’s been a lot of good thought on improving security around SIM-enabled devices, so 5G is probably the safest way to connect IoT services. Sure, Zigby and WiFi are cheaper, but SIM access is far more secure.
Compared to other access options, the telcos are actually doing a really good job with 5G security. There’s only one network in the world that adheres to five 9’s reliability and uptime — and that’s telco.
So if your IoT use case requires high quality connections and high security, your only option is 5G with its robust SIM access.
But make no mistake about it: IoT and 5G are tsunamis coming ashore. And figuring out how fraud and security experts should deal with these issues is where the “fun” is really going to start.
Copyright 2020 Black Swan Telecom Journal
Black Swan Solution Guides & Papers
- Expanding the Scope of Revenue Assurance Beyond Switch-to-Bill’s Vision — Araxxe — How Araxxe’s end-to-end revenue assurance complements switch-to-bill RA through telescope RA (external and partner data) and microscope RA (high-definition analysis of complex services like bundling and digital services).
- Lanck Telecom FMS: Voice Fraud Management as a Network Service on Demand — Lanck Telecom — A Guide to a new and unique on-demand network service enabling fraud-risky international voice traffic to be monitored (and either alerted or blocked) as that traffic is routed through a wholesaler on its way to its final destinations.
- SHAKEN / STIR Calling Number Verification & Fraud Alerting — iconectiv — SHAKEN/STIR is the telecom industry’s first step toward reviving trust in business telephony — and has recently launched in the U.S. market. This Solution Guide features commentary from technology leaders at iconetiv, a firm heavily involved in the development of SHAKEN.
- Getting Accurate, Up-to-the-Minute Phone Number Porting History & Carrier-of-Record Data to Verify Identity & Mitigate Account Takeovers — iconectiv — Learn about a recently approved risk intelligence service to receive authoritative and real-time notices of numbers being ported and changes to the carrier-of-record for specific telephone numbers.
- The Value of an Authoritative Database of Global Telephone Numbers — iconectiv — Learn about an authoritative database of allocated numbers and special number ranges in every country of the world. The expert explains how this database adds value to any FMS or fraud analyst team.
- The IPRN Database and its Use in IRSF & Wangiri Fraud Control — Yates Fraud Consulting — The IPRN Database is a powerful new tool for helping control IRSF and Wangiri frauds. The pioneer of the category explains the value and use of the IPRN Database in this 14-page Black Swan Solution Guide.
- A Real-Time Cloud Service to Protect the Enterprise PBX from IRSF Fraud — Oculeus — Learn how a new cloud-based solution developed by Oculeus, any enterprise can protect its PBX from IRSF fraud for as little as $5 a month.
- How Regulators can Lead the Fight Against International Bypass Fraud — LATRO Services — As a regulator in a country infected by SIM box fraud, what can you do to improve the situation? A white paper explains the steps you can and should you take — at the national government level — to better protect your country’s tax revenue, quality of communications, and national infrastructure.
- Telecom Identity Fraud 2020: A 36-Expert Analysis Report from TRI — TRI — TRI releases a new research report on telecom identity fraud and security. Black Swan readers can download a free Executive Summary of the Report.
- The 2021 State of Communications-Related Fraud, Identity Theft & Consumer Protection in the USA — iconectiv — This 49-page free Report on communications-related fraud analyzes the FTC’s annual Sentinel consumer fraud statistics and provides a sweeping view of trends and problem areas. It also gives a cross-industry view of the practices and systems that enable fraud control, identity verification, and security in our “zero trust” digital world.
Recent Stories
- Epsilon’s Infiny NaaS Platform Brings Global Connection, Agility & Fast Provision for IoT, Clouds & Enterprises in Southeast Asia, China & Beyond — interview with Warren Aw , Epsilon
- PCCW Global: On Leveraging Global IoT Connectivity to Create Mission Critical Use Cases for Enterprises — interview with Craig Price , PCCW Global
- Subex Explains its IoT Security Research Methods: From Malware & Coding Analysis to Distribution & Bad Actor Tracking — interview with Kiran Zachariah , Subex
- Mobile Security Leverage: MNOs to Tool up with Distributed Security Services for Globally-Connected, Mission Critical IoT — interview with Jimmy Jones , Positive Technologies
- TEOCO Brings Bottom Line Savings & Efficiency to Inter-Carrier Billing and Accounting with Machine Learning & Contract Scanning — interview with Jacob Howell , TEOCO
- PRISM Report on IPRN Trends 2020: An Analysis of the Destinations Fraudsters Use in IRSF & Wangiri Attacks — interview with Colin Yates , Yates Consulting
- Telecom Identity Fraud 2020: A 36-Expert Analyst Report on Subscription Fraud, Identity, KYC and Security — by Dan Baker , TRI
- Tackling Telecoms Subscription Fraud in a Digital World — interview with Mel Prescott & Andy Procter , FICO
- How an Energized Antifraud System with SLAs & Revenue Share is Powering Business Growth at Wholesaler iBASIS — interview with Malick Aissi , iBASIS
- Mobileum Tackles Subscription Fraud and ID Spoofing with Machine Learning that is Explainable — interview with Carlos Martins , Mobileum


