| © 2022 Black Swan Telecom Journal | • | protecting and growing a robust communications business | • a service of | |
| Email a colleague |
March 2020
Positive’s Research Keeps Telecoms One Step Ahead of Signaling Hackers and Fraud Disasters

As we publish this story, most countries of the world are battling an invisible enemy and killer, the Coronavirus.
Many of us today are working at home, keeping a “social distance”, and saying a prayer as we await the ultimate outcome of the fight. But in the meanwhile, the crisis has at least given us some time to think about risk problems and how experts in disease control deal with black swan epidemics.
There are parallels here between fighting viruses and blocking threats from another invisible enemy — criminal hackers and fraudsters:
- Treatments vs. Infections — Before a new virus cure or vaccine
is found, tremendous clinical research is required to detect the virus, statistically
examine its behavior, develop drugs, then test treatments.
Likewise, fraud control software and best practices treat “criminal infections” caused by insider security breaches, PBX hijacking, and hackers penetrating signaling systems to spoof, say, a mobile user’s identity.
- Virus Threats Never End — Contagious viruses, such as influenza,
the common cold, HIV, and SARS, are a constant plague on mankind. And
tracking the spread and transmission of viruses is a never ending research task.
For this reason, the U.S. Center for Disease Control (CDC) alone employs
17,000 people.
Telecom security also requires vigilance as criminals constantly adapt their methods. While the vast majority of attacks can be blocked by embedded intelligence in firewalls and other systems, unfortunately, it only takes a few successful attacks to cause great damage.
So there remains a great need for dedicated security professionals to constantly research threats, especially in these times when the mobile phone has become a favorite path of those committing fraud against banks, insurance companies, e-commerce firms, and other organizations.
One company at the forefront of guarding telecom signaling security is Switzerland-based Positive Technologies. And joining us to discuss signaling threats and protection techniques is Jimmy Jones, Positive Technologies’ Telecom Business Development Lead.
Jimmy does a great job of simplifying this highly complex domain. You’re going to enjoy how he: walks through the signaling security problem; shows how hackers penetrate; analyzes the growing signaling bypass threat; and explains the strategies taken by security-savvy telecoms.
| Dan Baker, Editor, Black Swan Telecom Journal: Jimmy, SS7 has been the signaling backbone of telecom since the late 1970s, and it survived the industry’s big move to IP networking. But that’s when many security problems began. |
Jimmy Jones: Dan, it’s true. A big catalyst for growing security concerns was the industry move to IP networking that happened around 2000. IP networks saved operators a lot of money, but it also exposed protocols to environments they weren’t designed for.

SS7 was originally a point-to-point protocol that operated on four wires, but then it moved to IP and combined with the global growth of network operators and the need for IP exchanges to connect to them created a perfect storm.
The same goes for Diameter. It’s a protocol absorbed by later cellular generations, but Diameter was never really designed for use in the roaming environment. The standards says it should be end-to-end encrypted, but nobody is actually doing that.
Bottom line, there are lots of things telecoms do in signaling that don’t adequately cover security as they should. And we’re paying for that lack of security robustness today.
| Now as a signaling security specialist firm, Positive Technologies is one step removed from telecom fraud problems. |
Signaling security is something Positive Technologies has been looking at for a long time. There are lots of wonderful companies who handle specific telco frauds such as Wangiri and International Revenue Share.
Positive Technologies instead focuses on discovering the security vulnerabilities that allow hackers to break into networks to commit those and other frauds such as bank account takeovers.
Actually, in preparation for this call, I wanted to refresh my understanding of the fraud enablers that telecoms deal with these days, so I scanned CFCA’s 2019 global fraud survey results.
When I looked at the survey data, some of my hunches were confirmed. For instance, I saw that PBX/IPX hacking and subscription fraud were still high on the fraud losses list. But I also noticed a spike in “configurational weaknesses”, which I never saw on that list before.
That particular finding rings true with what we are seeing here at Positive Technologies as we look across our SS7, 5G, and NFV portfolios. Overall, configuration issues represent a huge 30% of the security issues we discover. And that’s especially true for telcos.

| Tell us about your products and services. How do you approach the telecoms customer? |
We are a security company with a big research component. Of the one thousand people who work for Positive Technologies, half of them are security researchers.
Every day, our objective is to mimic hackers to test and secure the networks of clients. And in that role, we discover over 200 zero-day vulnerabilities a year. We support clients in a number of key industries: telecoms, IP, industrial cybersecurity, finance and more.
We also aim to deliver a high-touch service. The same guys who write our SS7 white papers and present at GSMA conferences are the same people who provide services for the telecom.

Now every two years we publish a statistical paper from our SS7 audits. In fact, the latest edition, SS7 Network Security Analysis 2020, has just been published: and it summarizes how the telecom operators we audit collectively performed in signaling security — and compares that to performance in past years.
Our 2018 survey report showed a big improvement compared to 2015 when hardly any of the operators had a firewall. Overall, our clients became less prone to SMS interception, subscriber location and various other attacks.
However the 2020 report data shows that vulnerabilities have climbed again. We attribute this to greater attack sophistication by the hackers.
In the past, the hackers saw no need to use sophisticated signaling bypass techniques because they could successfully penetrate the security gaps in the SS7 protocol. That attitude changed as operators started putting in SMS home routing platforms, signaling firewalls, and better STP filtering to block bad messages.
This has forced hackers to rethink their attack strategy so today they are turning to more complex bypass attacks to improve their success rate.
Actually, this growth in bypass techniques mirrors what happened in the IP world 20 to 30 years ago. People first had physical firewalls, then evolved toward next generation firewalls and other solutions. Hackers will always exploit the easiest route to get their job done.
| So how does Positive Technologies do its “white hat” hacking to discover the security vulnerabilities of your clients? |
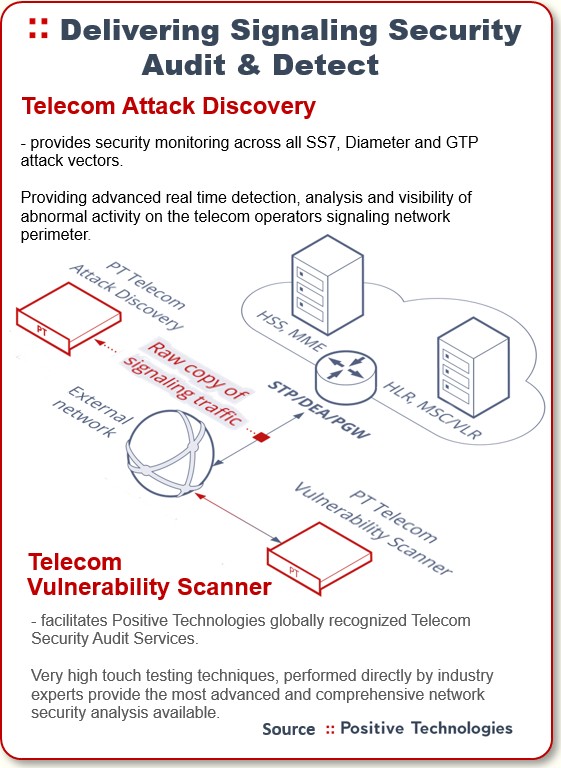
Normally we do that over our IPX network connection using testing devices located at our development center in Bruno, Czech Republic. We use that test system to send messages to whoever we are targeting.
Now because of the expertise these guys have, they are not just walking through a list on an Excel sheet or doing any sort of automated test. Instead they scan each message as it arrives on your network. This is highly tailored work because each operator has a unique set of vendors supported by unique software releases.
When our researchers see something in the data they have not seen before, they will alter the tests to take advantage of that knowledge. That’s exactly what the criminal hackers do: they try to break into a telecom operator the same way they aim to penetrate a bank or government agency.
Now it’s important to realize that the hackers are doing very targeted attacks. They know what they are trying to achieve, so rather than scatter gun attacks, they focus on a specific person’s identity, or the network element they want to compromise.
Positive Technologies experts also organize our reports in a way that’s easy for our customers to fix the vulnerabilities we discover. Not every security firm does a good job at this. When I was on the other side of the fence working in operators in the SIP World, I’d see massive 100-page reports that didn’t clearly highlight and explain the problems that needed to be fixed. They were not as efficient or effective as they could be, so I am proud to be part of a company that makes it easier for telcos to patch flaws.
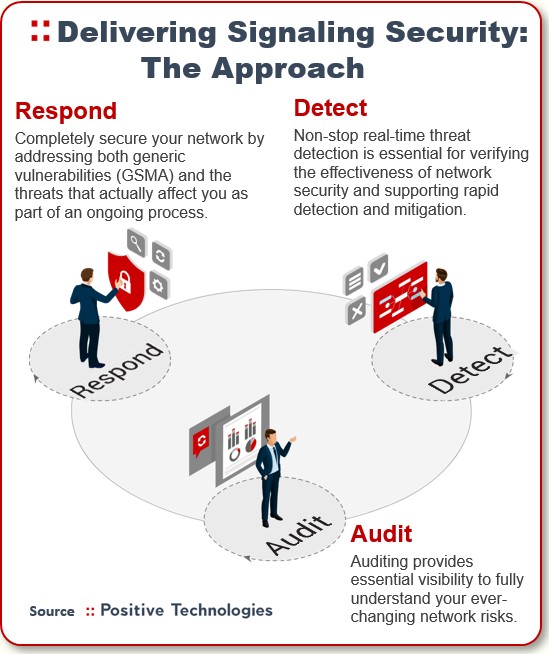
| Can you give me an example of how the hackers break into a telco? |
It all starts by gaining access to a phone number. Maybe they get your business card or learn of a phone number through a web form or email phishing attack.
From there, the hacker’s goal is to obtain the IMSI number which is the Holy Grail of SS7 hacking because it essentially identifies your phone on the network so they can now address your account. The IMSI is so precious that it’s guarded by fake IMSIs that are automatically generated by an SMS home router platform. Instead of sending the real IMSI, a fake number is sent. Then it waits for the next message to come in, and substitutes it for the real IMSI to be sent into the core.
But in 93% of the operators we tested, our researchers can bypass those protections and discover the IMSIs.
And once the hacker has the IMSI, they can do all sorts of other clever stuff. For example, they can send a PSI message and that message will tell hackers which cellular tower you are currently connected with. And depending on whether you are in a city or rural area, they can narrow it down to determine where you are located within very close proximity.
Hackers can continue sending that PSI message every 15 to 30 minutes and can location track you, mapping you to and from work or wherever you go over an extended period.
If the operator takes our audit services and we can also implement our monitoring/analytics platform, they can see what our researchers see and we can deliver richer reports to them, such as detailing the individuals being tracked. Then they can buy the Positive Technologies product and monitor their network themselves with our tools.
| And once the hackers discover the IMSI, how do they typically break into a mobile user’s bank account? |
Well, there’s actually a pretty well-documented 2017 case where some hackers exploited the Telefonica O2’s network in Germany.
A group of guys sent a phishing email and they captured data on six or seven people — all on the Telefonica O2 network. And all of the victims were people of very high net worth.
One evening the fraudsters gained access to their bank accounts and transferred around 100,000 Euros from each of the victims. This wasn’t a simple scheme — it required hijacking SMS authentication on the smartphone.
Their method was to send a message in the evening via SS7 as if they were an operator to Telefonica O2, saying the victim has roamed to my network. So the fake network was telling the real network the mobile user had got on a plane and roamed to another country. The fraudsters coordinated it so that all the victim’s SMS authentication messages were sent within a short time period. This is how the money was stolen.
The bank responsible for the loss reimbursed the victims. But the real damage came when Telefonica O2 went public and their share price dropped about 7 percent. Since that time, they’ve done a lot of work to resolve that issue, and today we believe they have one of the most secure networks in Europe.
| I can now see why preventing access to the IMSI is so crucial. |
Yes, there’s been a huge focus at stopping the IMSI from being compromised, because if you can do that, you’re pretty secure and many attacks are GSMA Category 1, so pretty easy to defend. The GSMA created three categories of network messages to make it easy for security professionals to classify problems:
- Category 1 — Messages transmitted between devices within one operator’s
network. For instance, if I’m Vodafone, messages from within
the Vodafone network are fine. But those messages should never arrive
from Deutsche Telekom, Telecom Italia, etc. These are very easy to defend
against because you can simply block them at the edge of your network.
- Category 2 — Messages transmitted from a subscriber’s home network
to a visited network. Let’s say I’m a Vodafone customer
leaving London and landing in New York where I’m on the Verizon network.
A message seems to be coming for me to the Verizon network. Well, if the
message is from Vodafone and he’s trying to find out something about me,
that’s fine, because my IMSI is registered with Vodafone. But if
the SS7 message looks like it’s coming from Fuji Telecom, then that shouldn’t
be allowed. This problem is solved by have a static table of IMSI ranges
so you know who owns what. This is held by GSMA and is called IR.21.
- Category 3 — Messages transmitted from a visited network to a subscriber’s
home network. For example, Vodafone received a message for me and
it looks like I’ve roamed to New York. This one is a bit harder
to sort out because you need to figure out if I could have actually arrived
in New York. One way you can resolve that is through “velocity tables.”
If my phone registered in London right now, it’s not possible for me to
be in New York in two hours.
| OK, even if an operator tunes its SMS home routing platforms, firewalls — and fixes its configuration issues — the hackers can still bypass these protection efforts. |
True. And that’s what our 2020 auditing revealed. Operators have upped their game to the point where the hackers are forced to bypass the signaling protection. They perform this bypass by slightly manipulating messages and for instance sending incorrect routing parameters to try and bypass the routing platforms.
You can use very similar techniques to get past the signaling firewall as well.
Combatting these bypass threats is precisely what our signaling security services are all about. And recently, the number of operator networks we can penetrate is going up.
We have critical security intelligence our telecom clients are eager to get their hands on because once those hackers break in and gather an IMSI, the threats generated move to Category 3, which is quite difficult to defend.
| Tell me more about your analytics platform. Sounds like that’s the key to reducing the signaling bypass. |
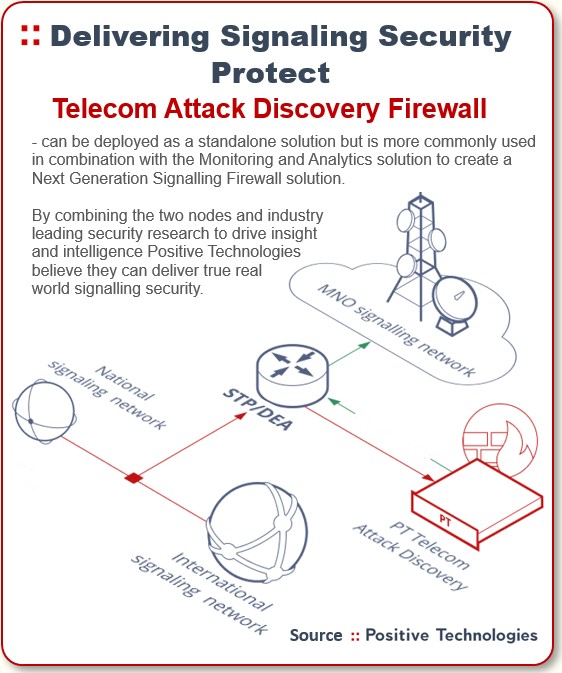
Yes, beyond our full portfolio of security services, we also deploy analytics platforms and firewalls — and these are especially useful in finding and blocking the complex bypass cases.
We have our firewall deployed — like everybody else — receiving packets from the STP: that’s the source. But we also have a monitoring point before the STP to feed our analytics tool.
The analytics platform is useful because it allows the operator to see the status of its security. And when you sit there at the edge of a big network, that analytics platform monitors thousands of illegitimate IMSI requests coming in.
So even if the first device is compromised and a message never goes near our firewall, we’ll still see the problem where we can highlight it for the operator. And 9 times out of 10 the answer is to configure something on the STP or another device on their network.
The up-to-date security intelligence and intuition of our security researchers also plays a major role in combatting signaling bypass attacks.
Say you went to BestBuy and bought two Cisco firewall units — exactly the same hardware, software, and firmware. The first firewall box is configured by a CCNA Cisco-certified IT guy. But the second firewall is configured by guy who has a CCIE certification, speaks at security events, wrote a book on security, and teaches other guy how to do it. You have two working firewalls, but which do you really trust? Probably the one configured by the second guy, the signaling security expert.
Now, in addition to our security intelligence, we are also sensitive to a customer’s specific needs. And here’s where we offer everything from training and support to monitoring and analytics managed services.
| Well, the signaling security problem is pretty daunting already. But now we’ve got 5G being deployed. Will we be better off when it fully arrives? |
Well, the good thing about 5G is that people have made a concerted effort to make sure it’s more secure. But the flip side is that 5G introduces many new vulnerabilities.
5G opens up an API interface into the network and that creates security risks as new third parties come in. How will that all play out? We don’t really know.
On top of opening up the network for APIs, 5G also virtualizes the networks. And that involves slicing the network to manage different network applications on the same infrastructure, which greatly adds to the complexity.
Today you’ve got one network that’s really designed for person-to-person communication, basically one application and one user device. And the application is me ringing my wife. But when you move to 5G, you’re essentially creating an IoT or machine-to-machine — and each of those machines could be vastly different.
It’s easy to see that car communication is far more complex than light bulb communication across the network. The applications that run them are completely different. Is the traffic going to be on the signaling plane or user plane? Who knows?
Everything we’ve had over the last 60 or 70 years in telecoms allows you to fully analyze and fine tune network applications to achieve 99.9999% uptime.
But 5G pushes all that out the window and flips it on its head — and yet you’re going to have to support that. The 5G environment will be immensely complex and the sheer number of devices is exploding too.
| Can you drill down a bit on the issue with virtual networks? |
Most telecom networks have been device driven: there’s a big box over there, an STP or Signaling Transfer Point taking all your messages in and out.
That’s how it used to work. But LTE and 4G transitioned us into an NFV (Network Function Virtualization) architecture, basically putting the telecom network on a cloud, like AWS. And the key virtue is that it takes away the expense: you don’t require as many hardware boxes or engineers.
Everything rides on a blade service, and if one blade goes bad, you send a guy in to replace the blade in the server. So now all those functions that used to be on separate boxes are in a virtual environment. So the same blade server might be an application server today but an STP server tomorrow.
The trouble is, virtualization introduces new vulnerabilities. A hacker may be able to jump from one area of the network to the other. Remember: AWS spent a fortune on protecting the data centers for their cloud environments. And now telecoms must protect themselves from similar threat vectors.
| What’s the threat look like for the Internet of Things (IoT)? |
In many ways, I think IoT is going to be a home run for telecoms. With IoT, instead of having 6 billion people on the planet, you can have 50 billion devices all doing different things. And the devices will vary from being an automated car to a drone, medical device, and devices of all sorts.
Medical needs to be ultra-reliable because you can’t be in the middle of a heart transplant and lose your connectivity. Similarly, with industrial security, you can’t have a robot not being able to communicate because lives may be at stake.
For each IoT device, you have different requirements — some require massive throughput, others need very low latency, or high reliability. And for each of these environments you create a network slice.
As I mentioned before, 30% of security vulnerabilities are the result of configuration problems. Well, with IoT, you can multiply that 30% by all the network slices. So instead of looking after one network, you could be overseeing 10 or more networks.
Yet another challenge comes from the ultra-low latency applications like virtual reality. When you put on that virtual reality helmet, the data can’t move back and forth from a data center in Dallas — it takes too long. So how do they resolve that? Well, they take that cloud environment and move a satellite portion of it close to where you are. This is called multi-access edge computing.
Now all those problems I just described are being put in a satellite station. These are going to be all over the place, and you’re going to have to defend them.
| Jimmy, thank you for this insightful tutorial on the signaling security threat. You’ve closed quite a few gaps in my knowledge of how security breaches lead to fraud and bank account raids. |
Thanks, Dan. Sorry to say that we security guys tend to be the prophets of gloom and doom.
But the signaling security threats are real and getting tougher to control. The number of potential vulnerabilities in 5G is astonishing. And the same problem of network exposure affect the IoT world too. Both environments provide front doors that will allow third party criminals to come onto the network and alter things.
On top of that, you’ve got the built-in vulnerabilities of SS7 and Diameter that will be with us for another 5 to 10 years at a minimum.
Bottom line, there remain rich opportunities for hackers and fraudsters to penetrate and do serious harm. It’s a perfect storm. But we have a way to mitigate the threats through early and comprehensive security strategies.
Copyright 2020 Black Swan Telecom Journal
Black Swan Solution Guides & Papers
- Expanding the Scope of Revenue Assurance Beyond Switch-to-Bill’s Vision — Araxxe — How Araxxe’s end-to-end revenue assurance complements switch-to-bill RA through telescope RA (external and partner data) and microscope RA (high-definition analysis of complex services like bundling and digital services).
- Lanck Telecom FMS: Voice Fraud Management as a Network Service on Demand — Lanck Telecom — A Guide to a new and unique on-demand network service enabling fraud-risky international voice traffic to be monitored (and either alerted or blocked) as that traffic is routed through a wholesaler on its way to its final destinations.
- SHAKEN / STIR Calling Number Verification & Fraud Alerting — iconectiv — SHAKEN/STIR is the telecom industry’s first step toward reviving trust in business telephony — and has recently launched in the U.S. market. This Solution Guide features commentary from technology leaders at iconetiv, a firm heavily involved in the development of SHAKEN.
- Getting Accurate, Up-to-the-Minute Phone Number Porting History & Carrier-of-Record Data to Verify Identity & Mitigate Account Takeovers — iconectiv — Learn about a recently approved risk intelligence service to receive authoritative and real-time notices of numbers being ported and changes to the carrier-of-record for specific telephone numbers.
- The Value of an Authoritative Database of Global Telephone Numbers — iconectiv — Learn about an authoritative database of allocated numbers and special number ranges in every country of the world. The expert explains how this database adds value to any FMS or fraud analyst team.
- The IPRN Database and its Use in IRSF & Wangiri Fraud Control — Yates Fraud Consulting — The IPRN Database is a powerful new tool for helping control IRSF and Wangiri frauds. The pioneer of the category explains the value and use of the IPRN Database in this 14-page Black Swan Solution Guide.
- A Real-Time Cloud Service to Protect the Enterprise PBX from IRSF Fraud — Oculeus — Learn how a new cloud-based solution developed by Oculeus, any enterprise can protect its PBX from IRSF fraud for as little as $5 a month.
- How Regulators can Lead the Fight Against International Bypass Fraud — LATRO Services — As a regulator in a country infected by SIM box fraud, what can you do to improve the situation? A white paper explains the steps you can and should you take — at the national government level — to better protect your country’s tax revenue, quality of communications, and national infrastructure.
- Telecom Identity Fraud 2020: A 36-Expert Analysis Report from TRI — TRI — TRI releases a new research report on telecom identity fraud and security. Black Swan readers can download a free Executive Summary of the Report.
- The 2021 State of Communications-Related Fraud, Identity Theft & Consumer Protection in the USA — iconectiv — This 49-page free Report on communications-related fraud analyzes the FTC’s annual Sentinel consumer fraud statistics and provides a sweeping view of trends and problem areas. It also gives a cross-industry view of the practices and systems that enable fraud control, identity verification, and security in our “zero trust” digital world.
Recent Stories
- Epsilon’s Infiny NaaS Platform Brings Global Connection, Agility & Fast Provision for IoT, Clouds & Enterprises in Southeast Asia, China & Beyond — interview with Warren Aw , Epsilon
- PCCW Global: On Leveraging Global IoT Connectivity to Create Mission Critical Use Cases for Enterprises — interview with Craig Price , PCCW Global
- Subex Explains its IoT Security Research Methods: From Malware & Coding Analysis to Distribution & Bad Actor Tracking — interview with Kiran Zachariah , Subex
- Mobile Security Leverage: MNOs to Tool up with Distributed Security Services for Globally-Connected, Mission Critical IoT — interview with Jimmy Jones , Positive Technologies
- TEOCO Brings Bottom Line Savings & Efficiency to Inter-Carrier Billing and Accounting with Machine Learning & Contract Scanning — interview with Jacob Howell , TEOCO
- PRISM Report on IPRN Trends 2020: An Analysis of the Destinations Fraudsters Use in IRSF & Wangiri Attacks — interview with Colin Yates , Yates Consulting
- Telecom Identity Fraud 2020: A 36-Expert Analyst Report on Subscription Fraud, Identity, KYC and Security — by Dan Baker , TRI
- Tackling Telecoms Subscription Fraud in a Digital World — interview with Mel Prescott & Andy Procter , FICO
- How an Energized Antifraud System with SLAs & Revenue Share is Powering Business Growth at Wholesaler iBASIS — interview with Malick Aissi , iBASIS
- Mobileum Tackles Subscription Fraud and ID Spoofing with Machine Learning that is Explainable — interview with Carlos Martins , Mobileum


