| © 2022 Black Swan Telecom Journal | • | protecting and growing a robust communications business | • a service of | |
| Email a colleague |
December 2019
How Thales Embeds Comms Security for Electronic OEMs & Telecoms Delivering Next Generation IoT Systems & Services

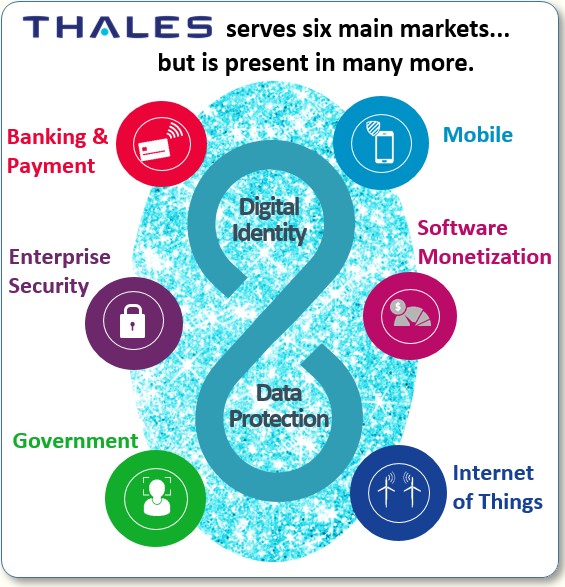
The Internet of Things (IoT) is the next evolutionary step in our communications-everywhere world.
Up until now, mobile communications have been dominated by carriers, large network equipment vendors, and mobile phone giants like Samsung, Apple, and Huawei, but IoT will create a far more open playing field.
In fact, IoT spells massive opportunity for garage-sized to mid-sized electronic OEMs that build a wide variety of comms-enabled devices (meters, sensors, tablets, and electronic panels) in hundreds of IoT apps — in addition to telecom operators providing new IoT services.
Imagine the explosion of IoT use cases that will emerge as these OEMs and telecom operators get their hands on powerful, highly secure, embedded IoT modules and new advanced analytics capabilities. The sky’s the limit.
Well, one of the top five companies providing these vital IoT-enabling connectivity and analytics capabilities is Thales through its Digital Identity and Security (DIS) global business unit.
Joining me to discuss the complex IoT connectivity, security and analytics ecosystem is Stephen Spellicy, Thales VP of Strategy & Marketing within the Analytics and IoT product team inside the DIS global business unit.
In my interview with Stephen he explains: how high-speed communications, advanced security and analytics technology gets delivered to the IoT OEMs and telecom providers; the very different business paradigm of IoT; and why security, performance, cost and reliability are key IoT challenges.
| Dan Baker, Editor, Black Swan Telecom Journal: Stephen, when we first spoke, you were working for Thales’ leading telecom analytics company, Guavus, but now you’ve moved over to Thales’ Analytics and IoT Systems Group. What’s cooking? |
Stephen Spellicy: Yes, Dan, I had been with Guavus for some time, but given my combined expertise in analytics and enterprise security software, I was asked to also assist with business and marketing strategy for the IoT modules business within the Thales’ DIS GBU called Analytics and IoT Systems (AIS).
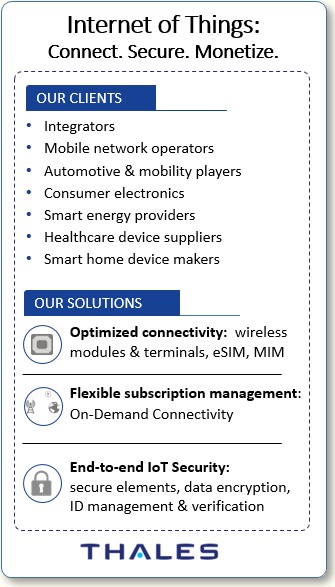
The AIS business offers products in the IoT module and device platform management service, serving verticals such as automotive, home automation, healthcare, energy and retail sectors. I’m still very focused on Guavus. A third of my responsibility is to represent the telecom business; however, I’m spending a lot of my time on our business to provide secure connectivity for verticals seeking to launch products in the industrial IoT market.
| But this IoT connectivity is embedded, and that’s quite a bit different from buying software and getting some servers to run it on. |
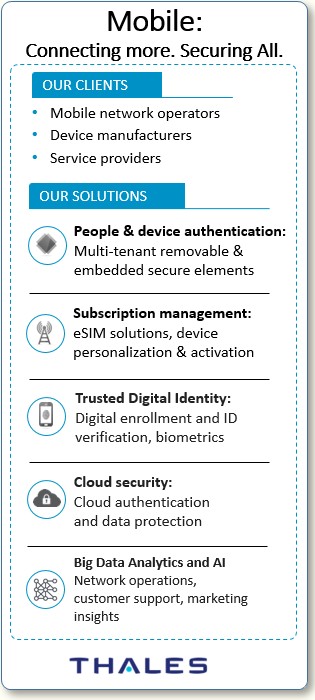
That’s right. Our solution is a high-speed, secure modem technology delivered as a modular component, and ultimately designed for and built into an OEM manufacturer’s end product. The verticals we cater to are firms who build products such as security panels (security and home automation), automotive (connected car connectivity) or make smart energy/metering systems. All of these things are being lit up with mobile connectivity.
This also includes smart retail point of sale (POS) systems that maintain contact with the retail operation’s headquarters to report hourly/daily sales. The chipsets are also used for IoT enabled medical devices, enabling physicians to monitor their patients’ health periodically and to be there to assist in a medical emergency.
We provide cellular modem technology that works across multiple and different radio technologies and bands in different parts of the world. The key to this business is to be able to support a variety of radio technologies, bands, communication standards (2G, 3G, 4G LTE, NB-IoT, 5G, etc.), and to have powerful embedded software for key encryption to deliver a highly secure IoT connectivity.
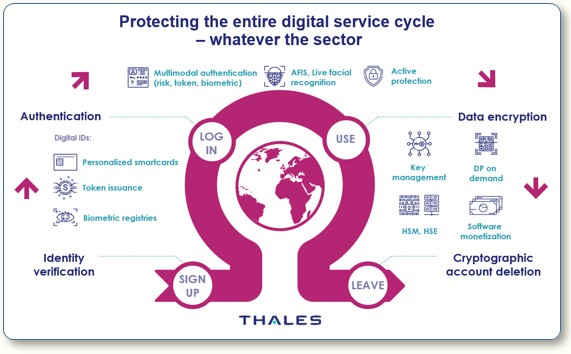
| Can you give us some use cases where your secure modem chipset is important? |
Well, one good example is what a large communication service provider customer of ours is doing for home security. Their offering is basically a smart tablet with cellular connectivity (for external access) and WiFi connected to a network of sensors in the home, such as doors, windows, coupled with secure cameras. That is all being connected back into a control panel for home automation and security management.
Another use case is in smart metering. It’s a similar architecture where we sit inside the meter, but there we speak to a completely different communication standard, NB-IoT or Narrowband IoT (low power WAN), or we communicate using LTE Category 1, M or M1.
Each of these communication standards have unique bandwidth requirements and features. Beyond 2G, 3G, 4G/LTE we will also be serving the 5G market as well. Much of the technical challenge is supporting the unique connectivity requirements in global markets — such as North America, Latin America, Europe, or Asia.
Use cases like video surveillance obviously require higher bandwidth, due to larger data payloads and transfer patterns, requiring higher upload speeds.
Smart meters generally require low power, though they need to have a long battery life, and use low bandwidth for their network communications. Cost is often a factor too. Smart metering manufacturers are deploying hundreds of thousands to millions of IoT devices. They require highly reliable cellular communication on the right networks for the right price.
| How are IoT systems brought to market? How does the carrier interface with the IoT specialist firm or factory? |
Well, typically in the security and home automation sector, for example, it’s the dealers and their installers who are deploying the security panels and selecting the mobile network operator (MNO) at the time of install.
This is where coordination is required by the OEM manufacturer to engineer the panel to support the right connectivity options for a particular region of the world.
As an IoT module vendor, we play a number of different roles in the design and delivery process. Not only do we supply the communication chipset to the security panel or smart metering manufacturer, we also supply the IoT device SIM cards to the MNOs — as well as the over-the-air (OTA) technology to activate and manage those devices.
Thales is, in fact, the world’s leading manufacturer of SIM cards (both physical SIM cards and eSIM technology).
So, developing products that serve both the telecom provider and the IoT device manufacturer markets enables both rapid innovation and gives Thales and our customers a competitive advantage.
| What’s being done to mitigate fraud? Where are these systems vulnerable? |
Fraud is definitely an issue in the cellular network. The SIM card is the vulnerability point from the perspective of potential misuse. Our advanced analytics and SIM management platforms have the ability to reduce the vulnerability of the device and prevent it from being taken over. And obviously, if the SIM is taken over or counterfeited, that leads to a myriad of fraud related threats where a smart device effectively becomes an avenue for IRSF and other frauds.
An emerging area of concern is when a smart device is roaming. Specific to IoT deployments, envision those dealers who are installing IoT smart meters for an energy company. Although the dealer has an agreement with an MNO to supply mobile connectivity at any particular site, connectivity may not be available (or signal strength to the home network may be poor), which means the device will likely roam.
In fact, in certain parts of the world being a “permanent roamer” beyond a certain amount of time is outlawed by regulation. By definition, traditional IoT deployments are not meant to be mobile, thus they aren’t mean to be in a permanent roaming mode. Typically, what you find is after a period of 30, 60 or 90 days, the MNO disables the devices that exhibit this behavior.
Imagine if you’re deploying thousands of devices for smart meters and some of them are popping up on the wrong network or non-preferred roaming partner (where an agreement already exists). That becomes a costly IoT deployment failure. Thus proper detection of these permanent roaming scenarios has become a very important issue to the industrial IoT space.
Another typical issue is when SIMs intended for IoT devices, which are meant to use lower cost, data only networks, are “swapped” from the device and used in a traditional mobile device to take advantage of lower costs fixed data usage. This kind of abuse or misuse is often a violation of the subscriber’s contract and if it can be detected, MNOs will try to disable to stem further use.
What we have in our portfolio is powerful analytics to detect this behavior and trigger alerts to enable the MNO to deactivate the rogue subscriber. The point is to provide a reliable service without any interruption — and to save costs and prevent fraud.
| You mentioned the challenge of getting certificate management and encrypted key management done. What are the deployment risks? |
Ensuring the certification and encryption at the SIM card level allows us to secure down a device’s communication. This expertise is absolutely crucial to vehicle communication, for obvious safety reasons. We are providing our leading SIM card technology to that market, and in some cases our module is being built into automaker designs for connectivity (e.g., potentially for tracking and trace, infotainment and predictive maintenance use cases).
The current generation cars and trucks have all sorts of sensors, such as sensors to measure the distance between vehicles to prevent collisions. You’re also tracking vehicle speed, performance, and potential maintenance issues. Within the world we live, we need to satisfy the passengers’ demand for infotainment, such as getting reliable digital downloads for music, etc. Simply put, if security compromises any of those functions, it’s a problem.
On the horizon, an even greater challenge will arise as vehicles talk to other vehicles (e.g. vehicle to vehicle aka v2v or vehicle to everything aka v2x), traffic lights, and emergency services. If a fire truck is responding to a fire alarm and approaches a 4-way intersection, even if the opposing traffic has a green light, you’d like to prevent it from entering the intersection while the fire truck is crossing the intersection.
| Stephen, this has been a very educational tutorial. IoT is obviously a new paradigm for MNOs, and so your explanation of that IoT ecosystem is very timely. |
Thanks, Dan. IoT requires mobile network connectivity — the pathway — to be successful. The chief concern of the MNO is to make sure they can provide the right service level, availability, and performance for a variety of use cases in the market today (traditional subscriber, M2M and beyond).
The IoT players are looking for connectivity at the right value and cost. And that requires telecom operators to be aware of the use case and the need to prevent service interruptions and otherwise be able to detect performance, security and misuse issues, such as the permanent roaming and SIM swapping problems I mentioned before.
Thales is in a unique position because we make the SIM cards, OTA platform, security infrastructure and IoT cellular module technology that enable secure mobile communication for IoT — and even the means to diagnose connectivity, performance, availability and security issues with our advanced analytics.
It’s a very exciting time at Thales right now, as we have all the right pieces in place to enable IoT device makers and MNOs to build innovative new products and services and really grow their businesses.
Copyright 2019 Black Swan Telecom Journal
Black Swan Solution Guides & Papers
- Expanding the Scope of Revenue Assurance Beyond Switch-to-Bill’s Vision — Araxxe — How Araxxe’s end-to-end revenue assurance complements switch-to-bill RA through telescope RA (external and partner data) and microscope RA (high-definition analysis of complex services like bundling and digital services).
- Lanck Telecom FMS: Voice Fraud Management as a Network Service on Demand — Lanck Telecom — A Guide to a new and unique on-demand network service enabling fraud-risky international voice traffic to be monitored (and either alerted or blocked) as that traffic is routed through a wholesaler on its way to its final destinations.
- SHAKEN / STIR Calling Number Verification & Fraud Alerting — iconectiv — SHAKEN/STIR is the telecom industry’s first step toward reviving trust in business telephony — and has recently launched in the U.S. market. This Solution Guide features commentary from technology leaders at iconetiv, a firm heavily involved in the development of SHAKEN.
- Getting Accurate, Up-to-the-Minute Phone Number Porting History & Carrier-of-Record Data to Verify Identity & Mitigate Account Takeovers — iconectiv — Learn about a recently approved risk intelligence service to receive authoritative and real-time notices of numbers being ported and changes to the carrier-of-record for specific telephone numbers.
- The Value of an Authoritative Database of Global Telephone Numbers — iconectiv — Learn about an authoritative database of allocated numbers and special number ranges in every country of the world. The expert explains how this database adds value to any FMS or fraud analyst team.
- The IPRN Database and its Use in IRSF & Wangiri Fraud Control — Yates Fraud Consulting — The IPRN Database is a powerful new tool for helping control IRSF and Wangiri frauds. The pioneer of the category explains the value and use of the IPRN Database in this 14-page Black Swan Solution Guide.
- A Real-Time Cloud Service to Protect the Enterprise PBX from IRSF Fraud — Oculeus — Learn how a new cloud-based solution developed by Oculeus, any enterprise can protect its PBX from IRSF fraud for as little as $5 a month.
- How Regulators can Lead the Fight Against International Bypass Fraud — LATRO Services — As a regulator in a country infected by SIM box fraud, what can you do to improve the situation? A white paper explains the steps you can and should you take — at the national government level — to better protect your country’s tax revenue, quality of communications, and national infrastructure.
- Telecom Identity Fraud 2020: A 36-Expert Analysis Report from TRI — TRI — TRI releases a new research report on telecom identity fraud and security. Black Swan readers can download a free Executive Summary of the Report.
- The 2021 State of Communications-Related Fraud, Identity Theft & Consumer Protection in the USA — iconectiv — This 49-page free Report on communications-related fraud analyzes the FTC’s annual Sentinel consumer fraud statistics and provides a sweeping view of trends and problem areas. It also gives a cross-industry view of the practices and systems that enable fraud control, identity verification, and security in our “zero trust” digital world.
Recent Stories
- Epsilon’s Infiny NaaS Platform Brings Global Connection, Agility & Fast Provision for IoT, Clouds & Enterprises in Southeast Asia, China & Beyond — interview with Warren Aw , Epsilon
- PCCW Global: On Leveraging Global IoT Connectivity to Create Mission Critical Use Cases for Enterprises — interview with Craig Price , PCCW Global
- Subex Explains its IoT Security Research Methods: From Malware & Coding Analysis to Distribution & Bad Actor Tracking — interview with Kiran Zachariah , Subex
- Mobile Security Leverage: MNOs to Tool up with Distributed Security Services for Globally-Connected, Mission Critical IoT — interview with Jimmy Jones , Positive Technologies
- TEOCO Brings Bottom Line Savings & Efficiency to Inter-Carrier Billing and Accounting with Machine Learning & Contract Scanning — interview with Jacob Howell , TEOCO
- PRISM Report on IPRN Trends 2020: An Analysis of the Destinations Fraudsters Use in IRSF & Wangiri Attacks — interview with Colin Yates , Yates Consulting
- Telecom Identity Fraud 2020: A 36-Expert Analyst Report on Subscription Fraud, Identity, KYC and Security — by Dan Baker , TRI
- Tackling Telecoms Subscription Fraud in a Digital World — interview with Mel Prescott & Andy Procter , FICO
- How an Energized Antifraud System with SLAs & Revenue Share is Powering Business Growth at Wholesaler iBASIS — interview with Malick Aissi , iBASIS
- Mobileum Tackles Subscription Fraud and ID Spoofing with Machine Learning that is Explainable — interview with Carlos Martins , Mobileum

