| © 2022 Black Swan Telecom Journal | • | protecting and growing a robust communications business | • a service of | |
| Email a colleague |
May 2019
WeDo Explores the IoT Ecosystem in Search of Tomorrow’s Pivotal Fraud & Business Assurance Solutions

The rational flâneur
(or strolling urban explorer) is someone who, unlike a tourist, makes a decision
at every step to revise his schedule, so he can imbibe things based on new information.
The flâneur is not a prisoner of a plan.
This ability to switch from a course of action lowers the risk, and you don’t
have to be right that often. All you need is the wisdom to not
do unintelligent things to hurt yourself — and to recognize favorable
outcomes when they come your way.
Nassim Taleb, author of The Black Swan (adapted)
Commercial opportunities in the modern world are bountiful, in part because very few people wander off their current path to think and play around with fresh ideas.
There was a time not long ago when people would lug heavy bags of luggage through air terminals and train stations. Then somebody decided to put tiny wheels on luggage. Today, it’s hard to find luggage without wheels.
In a tech company, the flâneur or new-product developer role rests on the CEO, marketing VP, and company strategist. With current successful products serving as today’s “cash cow”, the goal is to discover and develop new “star” products that will one day carry the company's fortunes into the future. Of course, choosing and nurturing these young stars requires great skill, patience and hard work.
Now while the Internet of Things (IoT) is a limited success today in some industrial settings, it’s getting ready to explode full-scale onto the telecom/digital/mobile network scene in applications such as on-line healthcare monitoring and connected cars.
Well, I had an interesting conversation on IoT with Carlos Duarte Marques, Head of Product Marketing and Analyst Relations at WeDo Technologies. One of Carlos’s key roles is to guide WeDo as it gains experience in the emerging IoT space and works with partners like Amazon AWS to find profitable niches.
In our discussion, Carlos gives us: his view of the IoT terrain; his observations on key challenges; and the preparatory steps WeDo is taking to become a key player in this emerging market.
| Dan Baker, Editor, Black Swan: Carlos, it sounds like moving into the IoT space is quite a sea change from your roots in telecom fraud and business assurance. |
Carlos Marques: Dan, traditionally we have only been collecting information from devices that address one vertical — the telecom industry — where all the information relies on their OSS/BSS. But those data sources are just a subset of information in a more complex ecosystem where you move to deliver customer products or services outside of the traditional telco space and start delivering other industry verticals.
For instance, if the IoT application is connected car or connected home, telcos don’t control the devices in those spheres: sometimes the connectivity provider (telco) is on the blind spot, since the information is being recorded in other platforms.
But as you imagine, some telcos also want to broaden their reach across the value chain. They want to provide the devices themselves so they can expand their market portfolio, allowing them to see the metrics and information collected by the devices.
And this necessarily requires telcos to expand the kind of services they provide. So if Vodafone controls a web of IoT devices for healthcare or connected homes, they are really entering new verticals, aren’t they?
| It’s true. A telco’s knowledge of connectivity and billing is one thing, but it’s a very different challenge to know what’s really important in a healthcare, industrial, or connected car domain. |
Dan, domain knowledge is especially critical when it comes to addressing fraud. Security is less of an issue because you can collect security logs and identity information from the IoT value chain, but fraud requires an actual understanding of the business itself.
So as a telco moves into IoT, an understanding of telco revenue share fraud doesn’t really help you if your IoT service is about stopping healthcare fraud.
That is why we have this vision to start reviewing our customer’s value chain and business models and start deploying IoT controls through our consulting team led by Thomas Steagall, who was the former head of the Risk and Revenue Assurance Practices at Ericsson.
And the reason Steagall’s team is so vital is that building business controls in the IoT space is almost like starting from scratch. When you talk about new industry use cases and their threats, it requires a professional consulting team to get that right. Since some of these projects are still in their early stage, this is the right time to do the “assurance by design” on the IoT value chain.
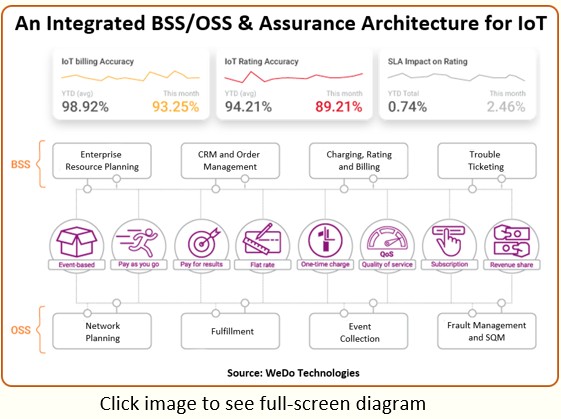
| Carlos, can you walk us through what provisioning a service will be like in IoT? |
So, in terms of provisioning, if the device has a SIM, then the identity of the devices needs to be established even before it reaches the telco. The device will be linked to a subscriber, and with each subscriber come a number of policies which set limits on what the particular device can do.
One very important series of policies are the connectivity ones. For example, you don’t want an IoT device set up for healthcare monitoring to be making premium rate calls!
Every device comes with an identity made by the manufacturer and that ID needs to be provisioned in the telco. If it’s a particular SIM card, then you will have specific tariff plans and policies associated with it.
After identity is established, the device will generate a token to, for instance, an AWS gateway where information will be collected on usage and performance metrics.
So if a General Motors (GM) car requests connectivity from Verizon, then Verizon says, “OK, this car is provisioned in my platform” and the Verizon system then sends a request to the GM platform that runs on AWS where GM is collecting the car metrics. In return, AWS sends a token back saying, “Verizon, you can give access to the GM car to start recording information here.”
With 5G and NFV on its way, from the telco point-of-view there are additional provisioning challenges in slices and on virtual instances, that will want to provision and measure the usage in real-time to create the dynamic billing that you will have on digital services like the connected car.
| What about fraud and revenue assurance for IoT? |
There too, complexity is very high. Billing and rating validation nowadays is much more than just the Call Detail Records (CDRs). You need to also get information from SLAs, quality of service, and much more to produce an accurate bill.
IoT is largely an event-based experience and it could be monetized in a number of ways: pay as you go, pay for results, and flat fee one time charge.
Subscriptions are for a certain time period, but the user may want to periodically connect to and disconnect from the services — and all that needs to be tracked in billing. If you want to keep using the CDR term, then call it: Chargeable Data Records :-)
Another big issue is subscription fraud. For instance, if you provisioned a device by using something similar to OpenID — like a Facebook or Google ID — you really need to get that right from the outset.
A lot of emphasis is being put on verifying the first identity because that identity will link to other devices. Can you imagine having subscription fraud for a fake account and then having linked devices using that identity?
It would soon turn into a mess because you are replicating a false identity accessing a wide range of services that can impact a person’s life much more than simple telecom services.
So this looks to be a very challenging revenue assurance and fraud management environment.
| By the way, I understand there’s going to be plenty of revenue assurance action on the wholesale side of IoT, not just checking the billing and provisioning of the retail consumer. |
Yes, people are not going to settle for flat fee partnering deals — everything needs to be measured out so each partner gets its rightful fee based on its effort to deliver the service. Moreover 5G flexibility for slicing will open new doors to new MVNOs outside of the traditional telecom space.
And I have a very good wholesale example: suppose GM wants to be an MVNO and allow its customers to buy telecom service direct from GM?
What they would need is 5G slices of service with different qualities of service according the services running on the car. And the connected car will have different computers since you will have to run several V2x services:
- V2I — Vehicle-to-Infrastructure,
- V2V — Vehicle-to-Vehicle,
- V2P — Vehicle-to-Pedestrian,
- V2D — Vehicle-to-Device,
- V2G — Vehicle-to-Grid for electrical vehicles to power grid,
- V2N — Vehicle-to-Network, and so on. . .
And logically there’s going to be different priorities and SLAs for information downloads based on rules and the need for bandwidth and quality. All of these different slices of how that GM car is connected must be defined in terms of usage, provisioning, billing and SLA policies.
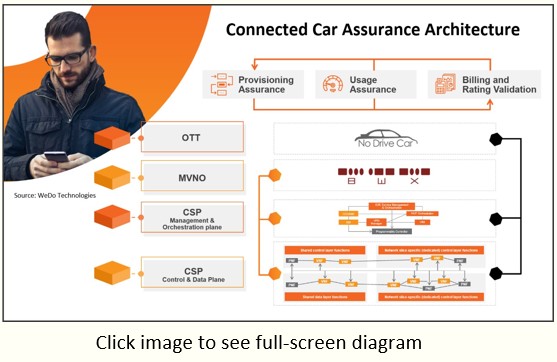
| So how is WeDo getting its feet wet in the IoT ecosystem? |
A lot of it started thanks to our work with our customers and leading IoT gateway providers like AWS. We began our relationships with them deploying our revenue assurance and fraud management platforms for several operators in the U.S. who use AWS to run their applications. And that experience exposed us to some connected car issues where WeDo can apply its knowhow.
We’ve learned you cannot rely on a connected car to be connected all the time. The data architectures the car companies are adopting is similar to mobile cloud architectures moving on our highways. And most will use either an AWS or Azure cloud architecture there, mostly due to the efforts these firms are putting on developing Edge architectures and OS that make connected devices the car truly autonomous and secure even when they don’t have good connectivity.
For example, you cannot rely on connectivity to supply, say, a complete set of up-to-date maps for car navigation. You simply must have the complete set of local area maps in the car’s computer system at all times. You also need an operating system that can navigate when the connectivity is broken. And this is where Edge computing comes in, which links to the cloud and gets updates on a predefined timeframe.
| Tell us a bit more about Edge Computing and why that’s critical going forward. |
The current use case for Edge Computing is being built on existing CDNs, the content distribution networks that ensure, for instance, very fast access to the 80% of internet traffic that is video.
The whole point is to make an efficient network that predicts what content should be cached close to the consumer so you minimize the repeated backhauling of info across the net.
The initial tests running for content distribution on Edge clouds will of course pave the way for connected cars — and they need 5G ultra-fast connectivity and edge computing for running locally all the V2X services that I’ve previously mentioned.
So now’s the time to test the systems while that onboard Netflix system is still dropping movie frames. Better be safe than sorry: nobody wants to put lives at risk on the road because edge technology on a connected car weren't adequately tested.
In fact, WeDo recently did a very interesting project with AWS to support 5G, edge video content distribution. It’s for a U.S. operator with several CDNs across the country and we are bringing the insights for better optimization of the CDNs running on AWS infrastructure.
What we are doing is looking up information in the OSS/BSS and collecting device data from the Edge to optimize how the service and the quality of experience is being delivered. The whole point is to optimize the distribution of the video content and bring the most revenue from a 5G remote content distribution.
Simultaneously, it turns out AWS is a very good data warehouse for us to keep the data because the collected data is not only being used by us but being used by another application running there.
| Carlos, thanks for this highly interesting discussion on IoT. It’s obvious WeDo is doing much preparation, partnering, tinkering, and investing to succeed in this exciting arena. Good luck with it. . . and let’s keep talking. |
Copyright 2019 Black Swan Telecom Journal
Black Swan Solution Guides & Papers
- Expanding the Scope of Revenue Assurance Beyond Switch-to-Bill’s Vision — Araxxe — How Araxxe’s end-to-end revenue assurance complements switch-to-bill RA through telescope RA (external and partner data) and microscope RA (high-definition analysis of complex services like bundling and digital services).
- Lanck Telecom FMS: Voice Fraud Management as a Network Service on Demand — Lanck Telecom — A Guide to a new and unique on-demand network service enabling fraud-risky international voice traffic to be monitored (and either alerted or blocked) as that traffic is routed through a wholesaler on its way to its final destinations.
- SHAKEN / STIR Calling Number Verification & Fraud Alerting — iconectiv — SHAKEN/STIR is the telecom industry’s first step toward reviving trust in business telephony — and has recently launched in the U.S. market. This Solution Guide features commentary from technology leaders at iconetiv, a firm heavily involved in the development of SHAKEN.
- Getting Accurate, Up-to-the-Minute Phone Number Porting History & Carrier-of-Record Data to Verify Identity & Mitigate Account Takeovers — iconectiv — Learn about a recently approved risk intelligence service to receive authoritative and real-time notices of numbers being ported and changes to the carrier-of-record for specific telephone numbers.
- The Value of an Authoritative Database of Global Telephone Numbers — iconectiv — Learn about an authoritative database of allocated numbers and special number ranges in every country of the world. The expert explains how this database adds value to any FMS or fraud analyst team.
- The IPRN Database and its Use in IRSF & Wangiri Fraud Control — Yates Fraud Consulting — The IPRN Database is a powerful new tool for helping control IRSF and Wangiri frauds. The pioneer of the category explains the value and use of the IPRN Database in this 14-page Black Swan Solution Guide.
- A Real-Time Cloud Service to Protect the Enterprise PBX from IRSF Fraud — Oculeus — Learn how a new cloud-based solution developed by Oculeus, any enterprise can protect its PBX from IRSF fraud for as little as $5 a month.
- How Regulators can Lead the Fight Against International Bypass Fraud — LATRO Services — As a regulator in a country infected by SIM box fraud, what can you do to improve the situation? A white paper explains the steps you can and should you take — at the national government level — to better protect your country’s tax revenue, quality of communications, and national infrastructure.
- Telecom Identity Fraud 2020: A 36-Expert Analysis Report from TRI — TRI — TRI releases a new research report on telecom identity fraud and security. Black Swan readers can download a free Executive Summary of the Report.
- The 2021 State of Communications-Related Fraud, Identity Theft & Consumer Protection in the USA — iconectiv — This 49-page free Report on communications-related fraud analyzes the FTC’s annual Sentinel consumer fraud statistics and provides a sweeping view of trends and problem areas. It also gives a cross-industry view of the practices and systems that enable fraud control, identity verification, and security in our “zero trust” digital world.
Recent Stories
- Epsilon’s Infiny NaaS Platform Brings Global Connection, Agility & Fast Provision for IoT, Clouds & Enterprises in Southeast Asia, China & Beyond — interview with Warren Aw , Epsilon
- PCCW Global: On Leveraging Global IoT Connectivity to Create Mission Critical Use Cases for Enterprises — interview with Craig Price , PCCW Global
- Subex Explains its IoT Security Research Methods: From Malware & Coding Analysis to Distribution & Bad Actor Tracking — interview with Kiran Zachariah , Subex
- Mobile Security Leverage: MNOs to Tool up with Distributed Security Services for Globally-Connected, Mission Critical IoT — interview with Jimmy Jones , Positive Technologies
- TEOCO Brings Bottom Line Savings & Efficiency to Inter-Carrier Billing and Accounting with Machine Learning & Contract Scanning — interview with Jacob Howell , TEOCO
- PRISM Report on IPRN Trends 2020: An Analysis of the Destinations Fraudsters Use in IRSF & Wangiri Attacks — interview with Colin Yates , Yates Consulting
- Telecom Identity Fraud 2020: A 36-Expert Analyst Report on Subscription Fraud, Identity, KYC and Security — by Dan Baker , TRI
- Tackling Telecoms Subscription Fraud in a Digital World — interview with Mel Prescott & Andy Procter , FICO
- How an Energized Antifraud System with SLAs & Revenue Share is Powering Business Growth at Wholesaler iBASIS — interview with Malick Aissi , iBASIS
- Mobileum Tackles Subscription Fraud and ID Spoofing with Machine Learning that is Explainable — interview with Carlos Martins , Mobileum


