| © 2022 Black Swan Telecom Journal | • | protecting and growing a robust communications business | • a service of | |
| Email a colleague |
June 2015
Device Intelligence and Big Data Linkage: Guarding Consumer Access Points from the Fraudsters

In the latest prominent breach of a company’s computer network, hackers have infiltrated the online marketplace eBay, gaining access to the personal data of 145 million customers. New York Times, May 2014
Our communications-driven world is blessed and cursed by greater access and “convenience”.
The blessing of convenience is that information is at our fingertips. We’ve moved from checking messages once a day by smart computer. . to once an hour by smart phone. . . to once every 10 minutes via smart watch.
But the curse of convenience is we’ve made it much easier for fraudsters, con artists, and hackers to rob us. The bad guys are only too happy to exploit our Facebook-inspired openness and the many communication devices we use to manage our banking and telecom service accounts.
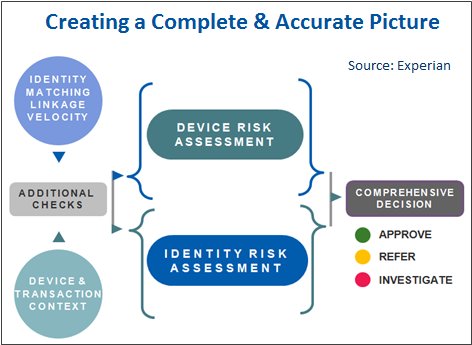
Luckily there are companies out there like Experian whose mission is to protect businesses and consumers and throw inconvenient roadblocks in the path of the fraudsters. Experian believes in customer-experience friendly fraud prevention tactics, such as predictive scores, device risk assessment, and linkage analysis. It applies intrusive methods such as knowledge-based authentication only when the risk and circumstances warrant it.
Staying ahead of the fraudsters is a constant challenge that involves supplementing traditional identity checks with a host of new processes, technology, and big data analytics.
Here to explain how credit and fraud prevention programs are keeping pace today is Matt Ehrlich, product director for Experian’s Decision Analytics Fraud and Identity Solutions.
| Dan Baker: Matt, thank for joining us. Could you give us a quick snapshot of how Experian helps protect telecom operators? |
Matt Ehrlich: Sure, Dan. Experian’s business is really on the front end, on the activation side — helping telecom operators keep the bad actors from getting on their networks or stealing equipment. We help some of the largest telecoms companies in the US and around the world.
If you have a Verizon Wireless account, for example, we can help prevent the takeover of that account — stop criminals from obtaining handsets, shipping them overseas, and selling them at a much higher price in countries where the phones are not subsidized by customer contracts.
| What techniques do you use to establish identity? And how is that practice evolving? |
As you’d expect, we use traditional identity-based fraud prevention, things like name, address, social security number, phone number, and data of birth — matching that with information we have on file for that customer.
But these days, it’s important to supplement traditional identity checks with data about the velocity and consistency of information presented by people. For example, if we are verifying an identity, is there anything suspicious about the information presented to us? Third party identity theft is all over the news in the US — a retail firm has a data breach and millions of credit cards are compromised, for instance.
But third party fraud is not the only issue. There’s also plenty of first party fraud, often called true party fraud. And here the actual person committing the fraud uses their own identity: they do not pose as someone else. However they still obtain handsets or services with no intent to pay for those things. The crime is made to look like simple credit default or credit delinquency.
To get approval, the fraudster needs to misrepresent something about himself: his email address, physical address — perhaps slightly changing his social security number.

Yet another popular identity spoofing scheme is “muling”. This is where the ring leader of a fraud ring will pay cash to someone (the mule) for committing part of the fraud scheme.
In telecom, the mules are often recruited on college campuses, through internet sites such as Craigslist, and as crazy as it sounds — even outside a wireless provider’s retail store. And the mule is instructed to go in the store, apply for credit, and obtain as many handsets as they can. Upon exiting the store, the ring leader will pay the mule a small amount of cash for the handsets.
| What kind of people are recruited as mules? |
Students are one of the more popular groups of people to be targeted. The fraudsters consider them ideal for two reasons: 1) there is typically less credit information on students; and 2) students are more incented to getting quick cash.
Unfortunately, these students fail to understand the long-term consequences of sacrificing their credit.
| Certainly one of the biggest risk challenges today is the many avenues for fraudsters to obtain private identify data thanks to all the desktop computers, laptops, tablets, and smart phone devices out there. |
Yes, convenience and the effort to promote a better customer experience can get in the way of security.
Luckily we’ve found that information collected about all these devices can be very predictive in highlighting risky transactions.
A year and a half ago, we acquired a company called 41st Parameter, experts in collecting information on devices and assessing risks based on the device. This gives us a whole new lens for looking at fraud risk and we have a whole new set of big data to combine with that traditional approach of identity assessment.
Device intelligence is about maintaining a history of activities associated with a particular device. So we recognize whenever that device visits a website or opens up a mobile app. Then, through big data, we investigate any potential linkage of that device to other websites and behaviors. This helps us understand the risks based on past performance and create fraud alerts appropriate to the device.
For example, through an IP address we can recognize that a device is accessing a website from outside the US, yet the user name logged in as a customer who lives in the US. So this will raise an alert. Criminals can even make it look like their inquiry to our client’s website is originating from Austin, Texas but our technology detects that spoofing and knows that access is being made, say, from Eastern Europe.
The nice thing about device intelligence is it allows you to keep the customer experience friendly. For example, when a telecom or wireless customer visits your website or your mobile app, because we can collect and evaluate many points of information on the device and compare it to what we know of its behavior historically, we don’t have to ask the consumer to provide additional information.
| The challenge of keeping the customer experience convenient rings true for me. When I call my bank, I am constantly asked questions to verify my identity. It’s frustrating to keep repeating information they already have access to. |
Dan, a major paradigm shift has occurred in customer care. In the past, you assumed that the person calling you at the call center to make an account change to his wireless account was indeed the legitimate person — because they provided the right identity information.
But in today’s world, we now have to assume that everyone has been the victim of some data breach and that their information is out there for criminals to find.
So I can no longer trust the information I am seeing as they visit my website or as they call into my call center. I am going to assume a position that this identity has been compromised and now look for positive information to support the fact that it is truly them.
You now have to prove to me that you are who you say you are. Now as you experienced, Dan, that kind of treatment is going to turn customers off and they are going to go to your competitor. So you have to verify identity in clever ways and tie that back to your technology and big data.
One of the techniques in common use today is voice biometrics. It’s an emerging technology that has improved a lot over the last few years. The idea is to capture a voice print of you and then check that against a whitelist or blacklist database to ask, “Is this really Dan Baker?”
Given all of the data breaches and security vulnerabilities we hear about in the news nearly every day, it’s no surprise that all identity verification methods are being scrutinized. Take knowledge-based authentication for example. It’s still considered sound practice to screen someone using unique questions that only they should know the answer to. But increasingly, even that has become more and more at risk as a method because of consumers’ openness in social media, the ubiquity of malware, and the extent of breached personal information.
| Thanks, Matt. It is indeed a financially risky world out there. We can liken the situation to security checks at the airport. Sure, they’re a waste of time and are inconvenient. But the technology and careful processes are there to protect us. |
Copyright 2015 Black Swan Telecom Journal
Black Swan Solution Guides & Papers
- Expanding the Scope of Revenue Assurance Beyond Switch-to-Bill’s Vision — Araxxe — How Araxxe’s end-to-end revenue assurance complements switch-to-bill RA through telescope RA (external and partner data) and microscope RA (high-definition analysis of complex services like bundling and digital services).
- Lanck Telecom FMS: Voice Fraud Management as a Network Service on Demand — Lanck Telecom — A Guide to a new and unique on-demand network service enabling fraud-risky international voice traffic to be monitored (and either alerted or blocked) as that traffic is routed through a wholesaler on its way to its final destinations.
- SHAKEN / STIR Calling Number Verification & Fraud Alerting — iconectiv — SHAKEN/STIR is the telecom industry’s first step toward reviving trust in business telephony — and has recently launched in the U.S. market. This Solution Guide features commentary from technology leaders at iconetiv, a firm heavily involved in the development of SHAKEN.
- Getting Accurate, Up-to-the-Minute Phone Number Porting History & Carrier-of-Record Data to Verify Identity & Mitigate Account Takeovers — iconectiv — Learn about a recently approved risk intelligence service to receive authoritative and real-time notices of numbers being ported and changes to the carrier-of-record for specific telephone numbers.
- The Value of an Authoritative Database of Global Telephone Numbers — iconectiv — Learn about an authoritative database of allocated numbers and special number ranges in every country of the world. The expert explains how this database adds value to any FMS or fraud analyst team.
- The IPRN Database and its Use in IRSF & Wangiri Fraud Control — Yates Fraud Consulting — The IPRN Database is a powerful new tool for helping control IRSF and Wangiri frauds. The pioneer of the category explains the value and use of the IPRN Database in this 14-page Black Swan Solution Guide.
- A Real-Time Cloud Service to Protect the Enterprise PBX from IRSF Fraud — Oculeus — Learn how a new cloud-based solution developed by Oculeus, any enterprise can protect its PBX from IRSF fraud for as little as $5 a month.
- How Regulators can Lead the Fight Against International Bypass Fraud — LATRO Services — As a regulator in a country infected by SIM box fraud, what can you do to improve the situation? A white paper explains the steps you can and should you take — at the national government level — to better protect your country’s tax revenue, quality of communications, and national infrastructure.
- Telecom Identity Fraud 2020: A 36-Expert Analysis Report from TRI — TRI — TRI releases a new research report on telecom identity fraud and security. Black Swan readers can download a free Executive Summary of the Report.
- The 2021 State of Communications-Related Fraud, Identity Theft & Consumer Protection in the USA — iconectiv — This 49-page free Report on communications-related fraud analyzes the FTC’s annual Sentinel consumer fraud statistics and provides a sweeping view of trends and problem areas. It also gives a cross-industry view of the practices and systems that enable fraud control, identity verification, and security in our “zero trust” digital world.
cSwans of a Feather
- Registered Caller: A Centralized Registry Service to Collect, Vet and Send Enterprise STIR/SHAKEN and Rich-Call-Data to Consumers — interview with George Cray & Tom Sawanobori — A fraud control solution vendor and national wireless association have teamed up to drive adoption of a new, central cloud service for enterprise vetting and validation to leverage STIR/SHAKEN info for telecoms in the U.S. market.
- Telecom Identity Fraud 2020: A 36-Expert Analyst Report on Subscription Fraud, Identity, KYC and Security — by Dan Baker — TRI releases a new research report on telecom identity fraud and security. Black Swan readers can download a free Executive Summary of the Report.
- How an Energized Antifraud System with SLAs & Revenue Share is Powering Business Growth at Wholesaler iBASIS — interview with Malick Aissi — A classic case of risk management driving a major boost in a telecom’s business. Learn details on the commercial offer, antifraud ystem upgrades, Do It Yourself customer portal and reporting.
- Webinar: Wangiri Warriors: Solutions & Strategies for Fighting Call Back Fraud — interview with Arnd Baranowski & John Haraburda & Igor Skutsenya & Colin Yates — A virtual webinar where four telecom fraud control experts give their perspective on Wangiri, the callback fraud. They discusses strategies and explain the solutions they offer to service providers.
- Black Swan Guide: Lanck Telecom’s Voice FMS as an On-Demand Network Service — interview with Igor Skutsenya — A Guide to a new and unique on-demand network service enabling fraud-risky international voice traffic to be monitored (and either alerted or blocked) as that traffic is routed through a wholesaler on its way to its final destinations.
- SAS Manages an Analytics Hub of Internal, 3rd Party, and AI Data for Telco-Specific, Holistic Fraud Solutions — interview with Sundeep Tengur — A leading cross-industry fraud analytics firm provides: a picture of telecom threats; perspective on subscription and onboarding fraud; parallels to fraud control in banking; and a rundown on its telco-specific approach to solving fraud problems in a holistic way.
- Lanck Telecom Raises Fraud Alarm for International Brands, Enterprise Call Centers & Carriers: Beware of Wangiri 2.0 — interview with Sergey Okhrimenko — An international wholesaler gives details about a new traffic pumping fraud dubbed Wangiri 2.0. The fraud is hard to detect and targets businesses who do lots of international calling.
- In the Era of Telecom Security Breaches, Mobileum Brings Signaling’s Deep Detection Capability to the Fraud Fight — interview with Miguel Carrero — Security-breach-driven fraud is on the increase as fraudsters gain deeper knowledge of telecom spheres such as roaming. Using five fraud cases, an expert shows how advanced signaling techniques are taking fraud control to a higher level.
- Tethering Fraud: How Guavus Blocks the Pumping of Mobile Data Traffic and Tools Up to Deliver 5G Service Management — interview with Kent McIntosh & David Yates — How is analytics being applied to next generation data threats? Learn how tethering fraud occurs and is detected. Also discussed are: data volume reduction at the network edge, IoT fraud concerns, and automating the healing of high-quality 5G data services.
- How GBSD Enables Advanced and Flexible Real-Time Fraud Blocking with its High-Trust, Mobile-Network-Embedded Softswitch — interview with Jeffrey Ross — Learn about a close-to-the-network platform that blocks mobile fruad, Reading a variety of protocols and integrated with external applications, it’s being used to combat: Wangiri, IRSF, SIM box bypass, and mobile money fraud.
- Mobileum on the Move: Attracts Several Operators to its IRSF-Analyzing & Opex-Saving Counter-Fraud Machine — interview with Avnish Chauhan — What’s the value of machine learning in fraud control? CTO of a leading counter-fraud solution provider discusses ML, biometrics, and voice service analytics in the context of fraud, roaming and security.
- Tracfone’s Anti-Fraud Controls and Law Enforcement Actions to Stop Cell Phone Trafficking — by Dan Baker — A conversation with an executive at Tracfone Wireless leads to lessons on MVNO fraud control and the significant law enforcement steps Tracfone is taking to stop cellphone trafficking, curb the violent of organized crime, and bring people to justice.
- Fraud Management in Music City: The 2017 Equinox Protector User Group Meeting — by Dan Baker — Program details of an upcoming fraud management conference in Nashville, Tennessee in November 2017. It’s the Equinox Protector User Group Meeting.
- Mobileum Brings Analytic Scans & Minimally Invasive Treatment to Fraud Removal — interview with Jason Lane-Sellers — Advanced analytics-driven fraud detection has arriving. It enables targeted treatment of fraud cases, lessening customer experience mistakes such as blocking calls to legitimate businesses.
- WeDo Offers Fraud Detection via a New Cloud Platform — interview with Thomas Steagall — A leading vendor introduces a cloud fraud control solution to serve the low cost, easy-to-deploy-learn-and-support requirements of many new operators, OTTs, and MVNOs.
- A Herculean Task: Battling Fraud in an Increasingly Complex Comms World — interview with Michalis Mavis — A fraud control expert walks through some interesting cases, gives us his advice on FMS software, and offers four key lessons on the path to fraud management excellence.
- The Early Warning Power of IPRN Test Call Detection in Blocking IRSF Fraud — interview with Colin Yates — Detecting the test calls made to International Premium Rate Numbers (IPRN) is helping telcos block IRSF fraud. An expert explains fraudster methods and the value of IPRN databases.
- Calculating the Fraud Risks of the Digital Era — by Dror Eshet — Digital and mobile technology are an integral part of our daily lives. Not only is the technology evolving at a frantic rate, but a leading fraud expert explains how fraudsters now team with one another to commit their crimes and magnify the risks to users, companies, and global infrastructure.
- SIM Box Bypass: The Damage to Developing Nations and the Actions Regulators Must Take — interview with Lex Wilkinson — Bypass fraud via the SIM box causes great revenue loss and poses many other dangers, especially in developing nations. An expert discusses the regulator issues and recommended actions in the fight to control bypass.
- Nine Simple Strategies for Protecting an Operator or MVNO from Telecom Fraud — interview with Jim Bolzenius — An expert in telecom fraud management explains essential strategies for aiming a carrier’s or MVNO’s fraud prevention program in the right direction.
- A Sweeping 239-Page Research Report on Fraud Management Solutions & Strategies — by Dan Baker — TRI has released a comprehensive analyst report on fraud management solutions. The study is based on interviews with three dozen leading FM consultants and solution experts. Download the free Executive Summary.
- SMS Bypass Blocking: A Service that Protects & Maximizes A2P Revenue for Mobile Operators — interview with Claire Cassar — A2P messaging is a multi-billion dollar revenue stream that mobile operators need to protect. In this interview, you’ll learn how a managed service solution blocks bulk marketing messages and other bypass fraud in enterprise-to-operator SMS traffic.
- Device Intelligence and Big Data Linkage: Guarding Consumer Access Points from the Fraudsters — interview with Matt Ehrlich — Preventing subscription fraud today means supplementing traditional identity checks with a host of new processes, technology, and big data analytics. A credit and fraud risk expert explains the roles of predictive scores, device risk assessment, and linkage analysis.
- Mapping the Interconnect Resale Routes of Fraudsters: How a Global Robot Network Detects Voice and SMS Bypass — interview with Xavier Lesage — SIM box voice bypass is a persistent problem, but now, bypass is spreading to SMS, OTT apps on the smartphone, and ghost trunks. This interview explains the fast evolving bypass scene, highlights the strategy of fraudsters, and provides case studies.
- Law Enforcement & Security in a World Where Industry and National Boundaries are Blurred — interview with Mark Johnson — Are we destined to be forever reactive over security, fraud, and risk issues? Or will we put wise standards, regulations, and frameworks in place that allow us to deliver technology that’s relatively secure and fraud-resistant?
- Thinking Outside the Comms Box: A New, Cross Industry Fraud Check Service that Telecoms can Leverage — interview with Jim Rice — For decades, telecoms have done fraud and identity checks using comms industry data. This interview explains the power of using cross-industry data to pinpoint known fraudsters and suspicious individuals in finance, retail, and other industry data sets.
- Integrated Test Call & CDR Analysis: A New Tool in the Fight Against SIM Box & OTT Bypass Fraud — interview with Kenneth Mouton — Why not combine the virtues of FMS CDR analysis and test call generators to create a single integrated tool for bypass fraud control? The benefits of that idea, a tutorial on test call systems in SIM box detection, and OTT bypass via mobile services like VIBER are all discussed in this interview.
- White Paper: How to Defend Your Network Against the New SIM Server Threat — by Dan Baker — SIM box bypass is a very stubborn fraud problem: fraudsters are succeeding despite carriers‘ best efforts to defeat the fraud. This white paper explains the impact of SIM Servers as a powerful stealth weapon of the fraudsters. In turn, the paper discusses new technologies and strategies that can defeat the more sophisticated types of SIM box fraud emerging.
- Intelligent Routing: The Case for Blocking IRSF Fraud at the SIP Session Border Controller — interview with Jim Dalton — A bad fraud event can be a huge loss, especially to OTT players who provide a VoIP service. In this interview, you’ll learn about an anti-fraud solution that works in concert with intelligent routing.
- A Privacy-Enabled Data Exchange that Expands Analytics Uses in Fraud, Credit Risk and Beyond — interview with Michelle Wheeler — Analytics data today is managed in a privacy-negligent way. This interview discusses an ingenious privacy and analytics exchange that allows telecoms, banks, and money lenders to trade fraud, credit risk and other data with each other in complete confidence and control.
- From Rules Design to Adaptive Learning Systems in Telecom Fraud Control — interview with Shankar Palaniandy — Adaptive and behaviorial learning systems are at the forefront of R&D in telecom fraud management systems. Here an expert developer explains their usefulness in use cases such as IRSF detection, subscription fraud, application fraud, and voice biometrics.
- Protecting 900+ MVNOs around the Globe from IRSF Fraud Pirates — interview with Colin Yates — Telecom fraudsters are seeking a new, more vulnerable path to riches. Their target: 900+ MVNOs around the globe who generally own no mobile networks, but sell mobile service virtually. This interview with a fraud control expert explains what steps MVNOs must take to protect themselves from IRSF fraud.
- Combating SIM Box Fraud: Network Protocol Analysis to the Revenue Rescue — interview with Lex Wilkinson — International call bypass is fraud perpetrated through SIM boxes equipped with dozens to hundreds of SIM cards that disguise international calls as local domestic phone calls. This article give a backgrounder on SIM box detection techniques and talks about a new, rapid-detection technology based on network protocol analysis.
- Making the Retail Operator Case for Anti-Fraud Protection via Wholesalers — interview with Jan Dingenouts — Small retail operators are highly vulnerable to fraud, so enlisting the anti-fraud assistance of wholesalers is a great idea. This interview explains useful negoiating tactics for retail operators and shows how wholesalers can lend support and grow their business at the same time.
- A Wholesaler’s Fraud Prevention Creed: If You Lose the Trust, You Lose the Traffic — interview with Robert Benlolo — Large wholesalers play a major role in keeping a lid on international telecom fraud. In this interview, a wholesale voice and fraud management expert explains the role of its vendor systems and multi-threaded internal processes in protecting customers from fraud losses and shady wholesale suppliers.
- Telecom Fraud & Credit Protection: A Desperate Need in Unbanked Regions of the World — interview with Luke Taylor — Mobile money plus related fraud and credit protection are crucial to the prosperity of developing nations where most “unbanked” people live. This article discusses the special issues of the unbanked market as well as broader revenue protection challenges and opportunities.
- The Grey Market in Prepaid: Tactics to Combat International Bypass via the SIM Box — interview with Ahmad Syed — SIM box fraud is one of the toughest revenue threats that telecoms face. It is the redirection of international calls via the internet to drop illegal VoIP traffic onto mobile networks. This interview with an expert RA and fraud manager provides a detailed overview of the threat scenario, current SIM box tactics, and some creative ideas for bringing this problem under control.
- Why Deep Packet Inspection Analysis is Essential for Detecting IP Fraud — by Dror Eshet — The IP and mobile broadband revolution is in full swing: time for fraud managers to totally rethink their existing controls and areas of exposure. In this article, a fraud expert discusses the power of DPI technology and the key impact its analysis is having in an FM world where knowing what’s inside the packets is as important as figuring out where those IP packages are going.
- Flexibility & Fraud Management Systems: 8 Questions for Luke Taylor of Neural Technologies — interview with Luke Taylor — Meeting today’s fraud threats is not just about technology, but also the speed of threat detection, the scanning of data outliers, and being enormously flexible. A leading fraud management vendor takes a bead on current FM issues and points to where software is headed.
- What Makes Good Fraud Management Software? 9 Questions for Tal Eisner of cVidya — interview with Tal Eisner — How do you know if the fraud management software you own or are considering is a good one? That’s the starting point of a conversation Black Swan had with a product strategist of a leading FMS vendor. The article discusses everything from maturity and customer collaboration... to PBX hacking and enabling the FMS to actually enhance the relationship a telco has with its enterprise customers.
- Fraud Management at Kyivstar in Ukraine — interview with Anton Pivala — Kyivstar from Ukraine is a leading mobile operator in both voice service quality and consumer value. This case study gives details on Kyivstar’s fraud control program, reveals some of the unique operator challenges faced in Eastern Europe, and explains how Kyivstar is successfully winning the battle against IRSF and SIMbox fraud.
- Gratifying Ghana: Why Listening to Operators Trumps Vendor Technology and Size — interview with Ludvig Lindqvist — The value of technically excellent software is negated if the solution is not implemented right. This article makes a strong case that vendors need to focus on first things first — get in full synch with a service provider’s business, capabilities and unique needs before you recommend or implement any software. Topics discussed include: the benefits of retaining in-house expertise, implementation challenges in Africa, and the meaning of “thorough engagement” with the client.
- “Fraud Is a Wind that Always Blows” and Other Wisdom From a 28-Year Old Software Firm — interview with Gary Beck — Here’s the amazing story of how Beck Computers was pulled out of a Tier 1 account only to be brought back in a few months later. The article explores software vendor service and support challenges, real-time computing requirements, advanced fraud management functions, and ways to educate management on the value an FMS investment.
- Fraud & Credit Risk Software: Setting the Client Free to Innovate — interview with Luke Taylor — Not every operator wants the freedom to configure its own fraud management solution, but certain providers wouldn‘t live without such a “framework” approach . This article discusses: the reasons why operator choose this strategy as it covers many other fraud and credit software implementation issues.
Related Articles
- Tokopedia, Indonesia’s E-Commerce King, Partners with 11 Million Merchants; Adopts Multi-Cloud to Drive Innovation — interview with Warren Aw & Ryan de Melo — Indonesia’s Tokopedia, founded in 2009, has grown to become one of world’s leading e-commerce players. Read about its success, technology direction, and multi-cloud connectivity adoption.
- Bridge Alliance: Knocking Down Regional & Mobile Connectivity Barriers so Connected Car Markets Get Rolling in Asia — interview with Kwee Kchwee — The CEO of an Asian consortium of mobile operators explains how they help simplify and harmonize their members‘ operations in support of multi-national corporations. This integration is enabling two huge industries to come together in Asia: auto manufacturing and telco.
- Epsilon’s Infiny NaaS Platform Brings Global Connection, Agility & Fast Provision for IoT, Clouds & Enterprises in Southeast Asia, China & Beyond — interview with Warren Aw — Network as a Service, powered by Software Defined Networks, are a faster, more agile, and more partner-friendly way of making data global connections. A leading NaaS provider explains the benefits for cloud apps, enterprise IT, and IoT.
- PCCW Global: On Leveraging Global IoT Connectivity to Create Mission Critical Use Cases for Enterprises — interview with Craig Price — A leading wholesale executive explains the business challenges of the current global IoT scene as it spans many spheres: technical, political, marketing, and enterprise customer value creation.
- Senet’s Cloud & Shared Gateways Drive LoRaWAN IoT Adoption for Enterprise Businesses, Smart Cities & Telecoms — interview with Bruce Chatterley — An IoT netowork pioneer explains how LoRaWAN tech fits in the larger IoT ecosystem. He gives use case examples, describes deployment restraints/costs, and shows how partnering, gateway sharing, and flexible deployment options are stimulating growth.
- ARM Data Center Software’s Cloud-Based Network Inventory Links Network, Operations, Billing, Sales & CRM to One Database — interview with Joe McDermott & Frank McDermott — A firm offering a cloud-based network inventory system explains the virtues of: a single underlying database, flexible conversions, task-checking workflow, new software business models, views that identify stranded assets, and connecting to Microsoft’s cloud platform.
- Pure Play NFV: Lessons Learned from Masergy’s Virtual Deployment for a Global Enterprise — interview with Prayson Pate — NFV is just getting off the ground, but one cloud provider to enterprises making a stir in virtual technology waters is Masergy. Here are lessons learned from Masergy’s recent global deployment using a NFV pure play software approach.
- The Digital Enabler: A Charging, Self-Care & Marketing Platform at the Core of the Mobile Business — interview with Jennifer Kyriakakis — The digital enabler is a central platform that ties together charging, self-care, and marketing. The article explains why leading operators consider digital enablers pivotal to their digital strategies.
- Delivering Service Assurance Excellence at a Reduced Operating Cost — interview with Gregg Hara — The great diversity and complexity of today’s networks make service assurance a big challenge. But advances in off-the-shelf software now permit the configuring and visualizing of services across multiple technologies on a modest operating budget.
- Are Cloud-Based Call Centers the Next Hot Product for the SMB Market? — interview with Doron Dovrat — Quality customer service can improve a company’s corporate identity and drive business growth. But many SMBs are priced out of acquiring modern call center technology. This article explains the benefits of affordable and flexible cloud-based call centers.
- Flexing the OSS & Network to Support the Digital Ecosystem — interview with Ken Dilbeck — The need for telecoms to support a broader digital ecosystem requires an enormous change to OSS infrastructures and the way networks are being managed. This interview sheds light on these challenges.
- Crossing the Rubicon: Is it Time for Tier Ones to Move to a Real-Time Analytics BSS? — interview with Andy Tiller — Will tier one operators continue to maintain their quilt works of legacy and adjunct platforms — or will they radically transform their BSS architecture into a new system designed to address the new telecom era? An advocate for radical transformation discusses: real-time analytics, billing for enterprises, partnering mashups, and on-going transformation work at Telenor.
- Paradigm Shift in OSS Software: Network Topology Views via Enterprise-Search — interview with Benedict Enweani — Enterprise-search is a wildly successful technology on the web, yet its influence has not yet rippled to the IT main stream. But now a large Middle Eastern operator has deployed a major service assurance application using enterprise-search. The interview discusses this multi-dimensional topology solution and compares it to traditional network inventory.
- The Multi-Vendor MPLS: Enabling Tier 2 and 3 Telecoms to Offer World-Class Networks to SMBs — interview with Prabhu Ramachandran — MPLS is a networking technology that has caught fire in the last decade. Yet the complexity of MPLS has relegated to being mostly a large carrier solution. Now a developer of a multi-vendor MPLS solutions explains why the next wave of MPLS adoption will come from tier 2/3 carriers supporting SMB customers.
- Enabling Telecoms & Utilities to Adapt to the Winds of Business Change — interview with Kirill Rechter — Billing is in the midst of momentous change. Its value is no longer just around delivering multi-play services or sophisticated rating. In this article you’ll learn how a billing/CRM supplier has adapted to the times by offering deeper value around the larger business issues of its telecom and utility clients.
- Driving Customer Care Results & Cost Savings from Big Data Facts — interview with Brian Jurutka — Mobile broadband and today’s dizzying array of app and network technology present a big challenge to customer care. In fact, care agents have a hard time staying one step ahead of customers who call to report problems. But network analytics comes to the rescue with advanced mobile handset troubleshooting and an ability to put greater intelligence at the fingertips of highly trained reps.
- Hadoop and M2M Meet Device and Network Management Systems — interview with Eric Wegner — Telecom big-data in networks is more than customer experience managment: it’s also about M2M plus network and element management systems. This interview discusses the explosion in machine-to-machine devices, the virtues and drawbacks of Hadoop, and the network impact of shrink-wrapped search.
- The Data Center & Cloud Infrastructure Boom: Is Your Sales/Engineering Team Equipped to Win? — by Dan Baker — The build-out of enterprise clouds and data centers is a golden opportunity for systems integrators, carriers, and cloud providers. But the firms who win this business will have sales and engineering teams who can drive an effective and streamlined requirements-to-design-to-order process. This white paper points to a solution — a collaborative solution designs system — and explains 8 key capabilities of an ideal platform.
- Big Data: Is it Ready for Prime Time in Customer Experience Management? — interview with Thomas Sutter — Customer experience management is one of the most challenging of OSS domains and some suppliers are touting “big data” solutions as the silver bullet for CEM upgrades and consolidation. This interview challenges the readiness of big data soluions to tackle OSS issues and deliver the cost savings. The article also provides advice on managing technology risks, software vendor partnering, and the strategies of different OSS suppliers.
- Calculated Risk: The Race to Deliver the Next Generation of LTE Service Management — interview with Edoardo Rizzi — LTE and the emerging heterogeneous networks are likely to shake up the service management and customer experience management worlds. Learn about the many new network management challenges LTE presents, and how a small OSS software firm aims to beat the big established players to market with a bold new technology and strategy.
- Decom Dilemma: Why Tearing Down Networks is Often Harder than Deploying Them — interview with Dan Hays — For every new 4G LTE and IP-based infrastructure deployed, there typically a legacy network that’s been rendered obsolete and needs to be decommissioned. This article takes you through the many complexities of network decom, such as facilities planning, site lease terminations, green-safe equipment disposal, and tax relief programs.
- Migration Success or Migraine Headache: Why Upfront Planning is Key to Network Decom — interview with Ron Angner — Shutting down old networks and migrating customers to new ones is among the most challenging activities a network operators does today. This article provides advice on the many network issues surrounding migration and decommissioning. Topics discussed include inventory reconciliation, LEC/CLEC coordination, and protection of customers in the midst of projects that require great program management skills.
- Navigating the Telecom Solutions Wilderness: Advice from Some Veteran Mountaineers — interview with Al Brisard — Telecom solutions vendors struggle mightily to position their solutions and figure out what to offer next in a market where there’s considerable product and service crossover. In this article, a veteran order management specialist firm lays out its strategy for mixing deep-bench functional expertise with process consulting, analytics, and custom API development.
- Will Telecoms Sink Under the Weight of their Bloated and Out-of-Control Product Stacks? — interview with Simon Muderack — Telecoms pay daily for their lack of product integration as they constantly reinvent product wheels, lose customer intelligence, and waste time/money. This article makes the case of an enterprise product catalog. Drawing on central catalog cases at a few Tier 1 operators, the article explains the benefits: reducing billing and provisioning costs, promoting product reuse, and smoothing operations.
- Virtual Operator Life: Enabling Multi-Level Resellers Through an Active Product Catalog — interview with Rob Hill — The value of product distribution via virtual operators is immense. They enable a carrier to sell to markets it cannot profitably serve directly. Yet the need for greater reseller flexibility in the bundling and pricing of increasingly complex IP and cloud services is now a major channel barrier. This article explains what’s behind an innovative product catalog solution that doubles as a service creation environment for resellers in multiple tiers.
- Telecom Blocking & Tackling: Executing the Fundamentals of the Order-to-Bill Process — interview with Ron Angner — Just as football teams need to be good at the basics of blocking and tackling, telecoms need to excel at their own fundamental skillset: the order-to-cash process. In this article, a leading consulting firm explains its methodology for taking operators on the path towards order-to-cash excellence. Issues discussed include: provisioning intervals; standardization and simplicity; the transition from legacy to improved process; and the major role that industry metrics play.
- Wireline Act IV, Scene II: Packaging Network & SaaS Services Together to Serve SMBs — by John Frame — As revenue from telephony services has steadily declined, fixed network operators have scrambled to support VoIP, enhanced IP services, and now cloud applications. This shift has also brought challenges to the provisioning software vendors who support the operators. In this interview, a leading supplier explains how it’s transforming from plain ol‘ OSS software provider to packager of on-net and SaaS solutions from an array of third party cloud providers.
- Telecom Merger Juggling Act: How to Convert the Back Office and Keep Customers and Investors Happy at the Same Time — interview with Curtis Mills — Billing and OSS conversions as the result of a merger are a risky activity as evidenced by famous cases at Fairpoint and Hawaiian Telcom. This article offers advice on how to head off problems by monitoring key operations checkpoints, asking the right questions, and leading with a proven conversion methodology.
- Is Order Management a Provisioning System or Your Best Salesperson? — by John Konczal — Order management as a differentiator is a very new concept to many CSP people, but it’s become a very real sales booster in many industries. Using electronics retailer BestBuy as an example, the article points to several innovations that can — and are — being applied by CSPs today. The article concludes with 8 key questions an operator should ask to measure advanced order management progress.
- NEC Takes the Telecom Cloud from PowerPoint to Live Customers — interview with Shinya Kukita — In the cloud computing world, it’s a long road from technology success to telecom busness opportunity. But this story about how NEC and Telefonica are partnering to offer cloud services to small and medium enterprises shows the experience of early cloud adoption. Issues discussed in the article include: customer types, cloud application varieties, geographic region acceptance, and selling challenges.
- Billing As Enabler for the Next Killer Business Model — interview with Scott Swartz — Facebook, cloud services, and Google Ads are examples of innovative business models that demand unique or non-standard billing techniques. The article shows how flexible, change-on-the-fly, and metadata-driven billing architectures are enabling CSPs to offer truly ground breaking services.
- Real-Time Provisioning of SIM Cards: A Boon to GSM Operators — interview with Simo Isomaki — Software-controlled SIM card configuration is revolutionizing the activation of GSM phones. The article explains how dynamic SIM management decouples the selection of numbers/services and delivers new opportunities to market during the customer acquisition and intial provisoining phase.
- A Cynic Converted: IN/Prepaid Platforms Are Now Pretty Cool — interview with Grant Lenahan — Service delivery platforms born in the IN era are often painted as inflexible and expensive to maintain. Learn how modern SDPs with protocol mediation, high availability, and flexible Service Creation Environments are delivering value for operators such as Brazil’s Oi.
- Achieving Revenue Maximization in the Telecom Contact Center — interview with Robert Lamb — Optimizing the contact center offers one of the greatest returns on investment for a CSP. The director of AT&T’s contact center services business explains how telecoms can strike an “artful balance” between contact center investment and cost savings. The discussion draws from AT&T’s consulting with world class customers like Ford, Dell, Discover Financial, DISH Network, and General Motors.
- Mobile Broadband: The Customer Service Assurance Challenge — interview with Michele Campriani — iPhone and Android traffic is surging but operators struggle with network congestion and dropping ARPUs. The answer? Direct resources and service quality measures to ensure VIPs are indeed getting the quality they expect. Using real-life examples that cut to the chase of technical complexities, this article explains the chief causes of service quality degradation and describes efficient ways to deal with the problem.
- Telco-in-a-Box: Are Telecoms Back in the B/OSS Business? — interview with Jim Dunlap — Most telecoms have long since folded their merchant B/OSS software/services businesses. But now Cycle30, a subsidiary of Alaskan operator GCI, is offering a order-to-cash managed service for other operators and utilities. The article discusses the company’s unique business model and contrasts it with billing service bureau and licensed software approaches.
- Bricks, Mortar & Well-Trained Reps Make a Comeback in Customer Management — interview with Scott Kohlman — Greater industry competition, service complexity, and employee turnover have raised the bar in the customer support. Indeed, complex services are putting an emphasis on quality care interactions in the store, on the web, and through the call center. In this article you’ll learn about innovations in CRM, multi-tabbed agent portals, call center agent training, customer treatment philosophies, and the impact of self-service.
- 21st Century Order Management: The Cross-Channel Sales Conversation — by John Konczal — Selling a mobile service is generally not a one-and-done transaction. It often involves several interactions — across the web, call center, store, and even kiosks. This article explains the power of a “cross-channel hub” which sits above all sales channels, interacts with them all, and allows a CSP to keep the sales conversation moving forward seamlessly.
- Building a B/OSS Business Through Common Sense Customer Service — by David West — Delivering customer service excellence doesn‘t require mastering some secret technique. The premise of this article is that plain dealing with customers and employees is all that’s needed for a winning formula. The argument is spelling out in a simple 4 step methodology along with some practical examples.

